Protection contre les cybermenaces
Les utilisateurs, les appareils et les charges de travail étant désormais disséminés, l’approche centrée sur le pare-feu d’hier ne peut plus assurer une protection contre les cyberattaques. Une nouvelle architecture est indispensable.
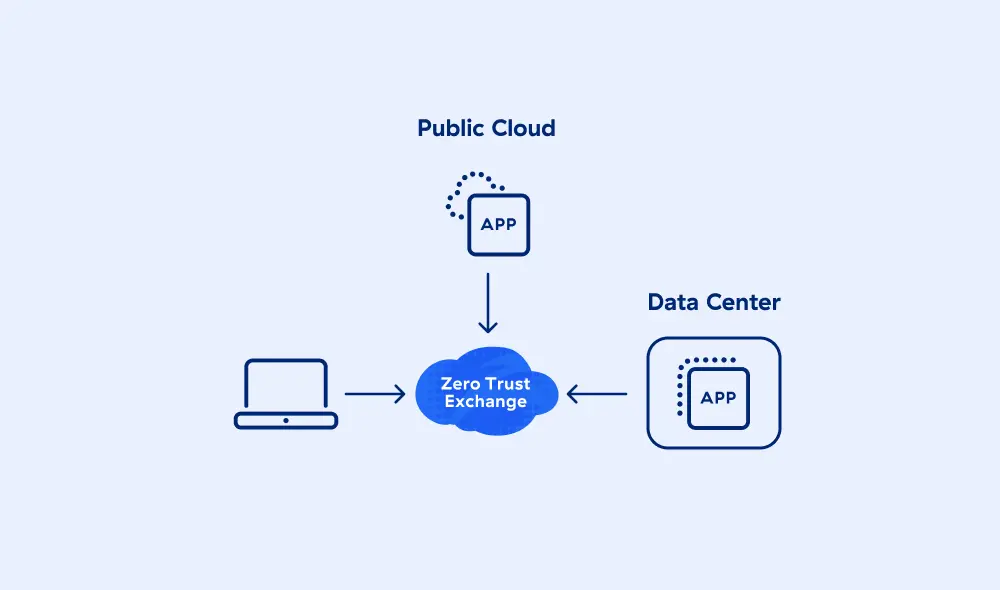
Remplacez les pare-feu et les VPN traditionnels par Zscaler Zero Trust Exchange™, le cloud de sécurité inline le plus important et le plus déployé au monde, pour répondre aux besoins cybernétiques en constante évolution des entreprises modernes.
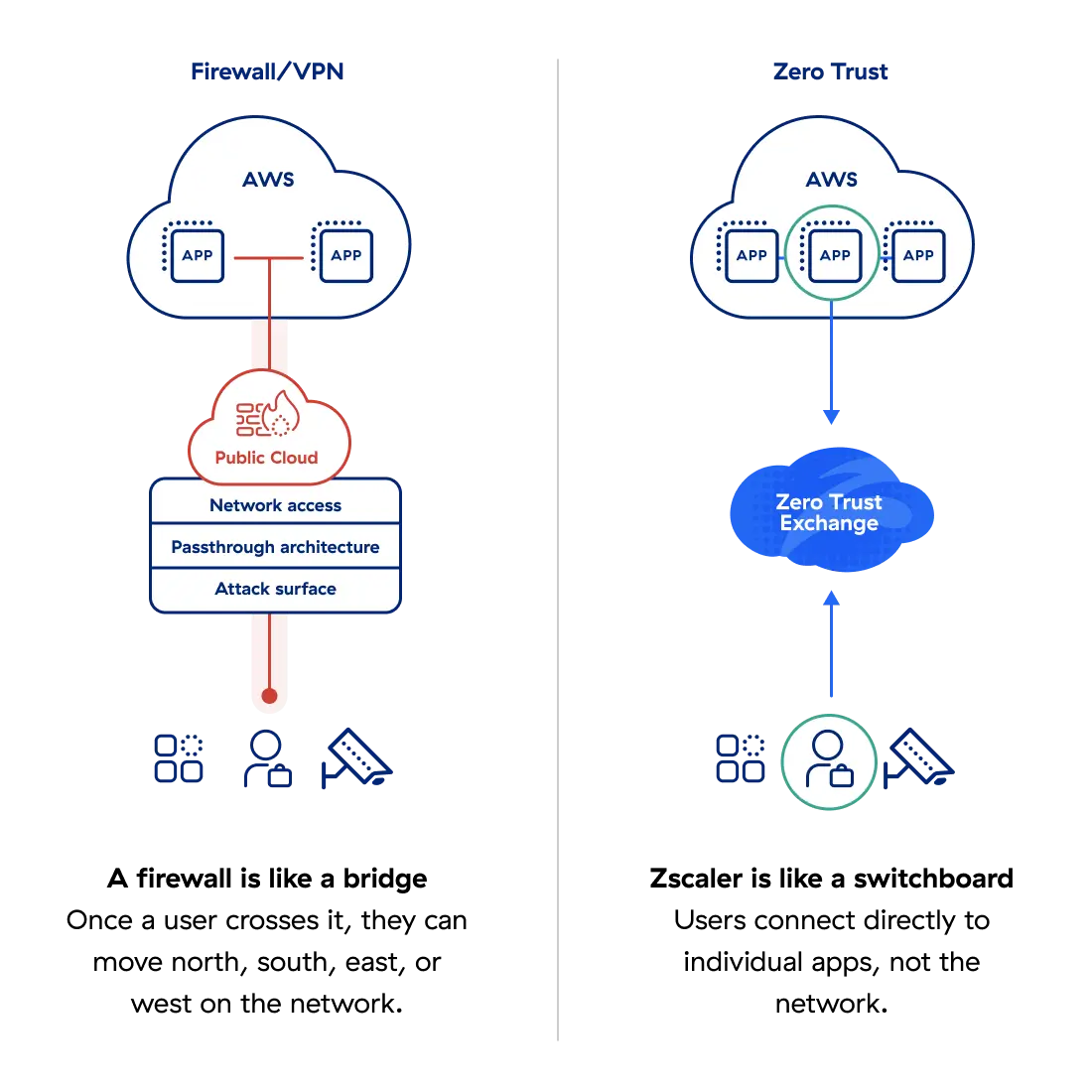
Transformez votre architecture de pare-feu en architecture Zero Trust
Les entreprises du monde entier ont dépensé des milliards en pare-feu, mais les violations se multiplient. Le problème est simple : les architectures traditionnelles centrées sur les pare-feu ne sont plus efficaces contre les cybermenaces.
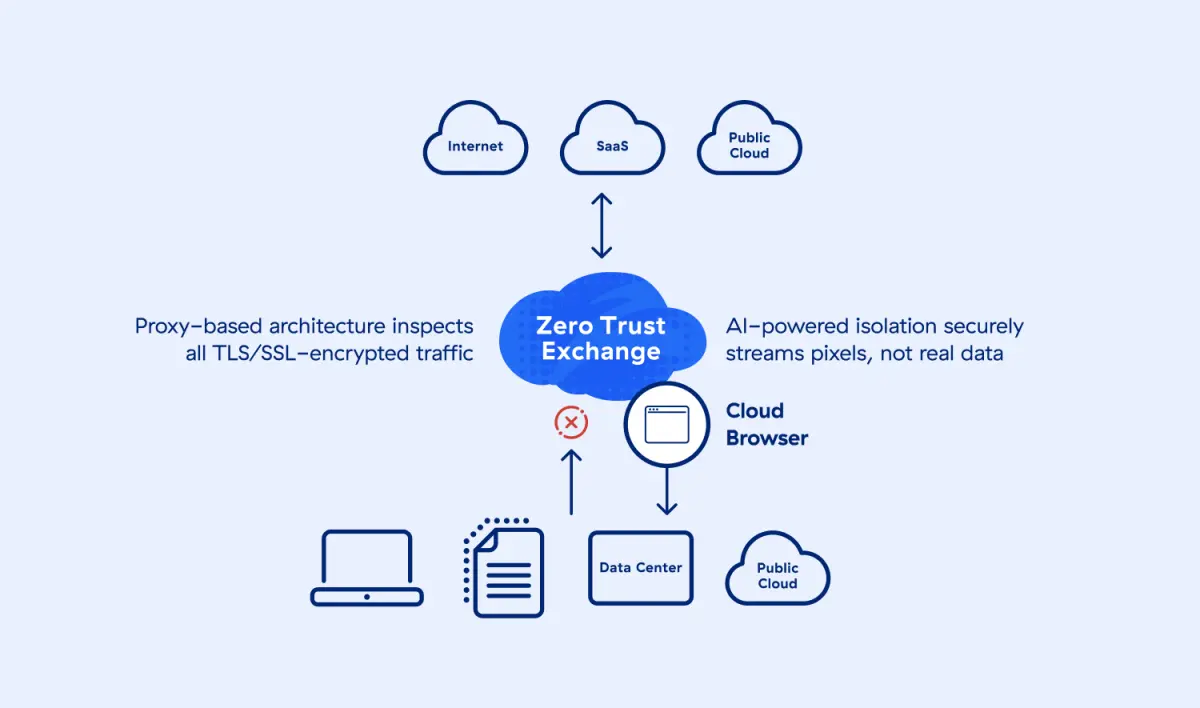
Fondée sur le principe du moindre privilège, l’architecture proxy de Zscaler permet une inspection TLS/SSL complète à l’échelle, avec des connexions négociées entre les utilisateurs et les applications en fonction de l’identité, du contexte et des politiques de l’entreprise.

Zscaler Rated AAA in CyberRatings SSE Report, Q2 2024
Minimise la surface d’attaque, évite les compromissions, élimine les déplacements latéraux et arrête la perte de données
Élimine les produits ponctuels et la complexité, ce qui réduit les risques pour l’entreprise
Protection contre les menaces basée sur l’IA, alimentée par 500 000 milliards de signaux quotidiens et 320 milliards de transactions quotidiennes
Informations exploitables et flux de travail guidés pour la remédiation

Découvrez où résident 86 % des cybermenaces. Consultez le rapport complet de Zscaler ThreatLabz 2023 sur l’état des attaques chiffrées.
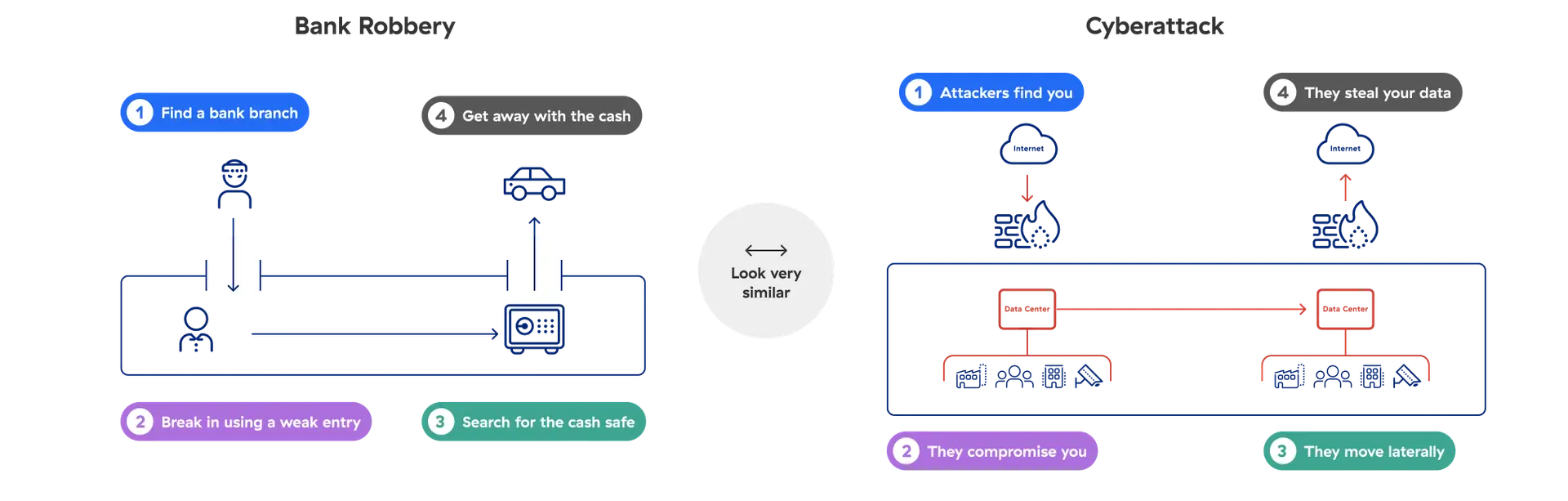
Problème
Une cyberattaque peut être comparée à un braquage de banque
Protection complète contre les menaces pour rompre la chaîne d’attaque
La plateforme cloud native Zscaler Zero Trust Exchange combat chaque étape de la chaîne d’attaque. Cette approche globale s’inscrit dans le cadre MITRE ATT&CK pour minimiser la surface d’attaque, empêcher les compromissions, éliminer les déplacements latéraux et arrêter la perte de données.


Stoppez les cybermenaces avec la sécurité optimisé par l’IA
Réduisez jusqu’à 50 % le nombre d’incidents, de 85 % le nombre de ransomwares et de 55 % les coûts d’architecture de sécurité grâce à une architecture Zero Trust fournie dans le cloud qui sécurise votre entreprise à chaque étape d’une attaque.
DÉTAILS de la solution
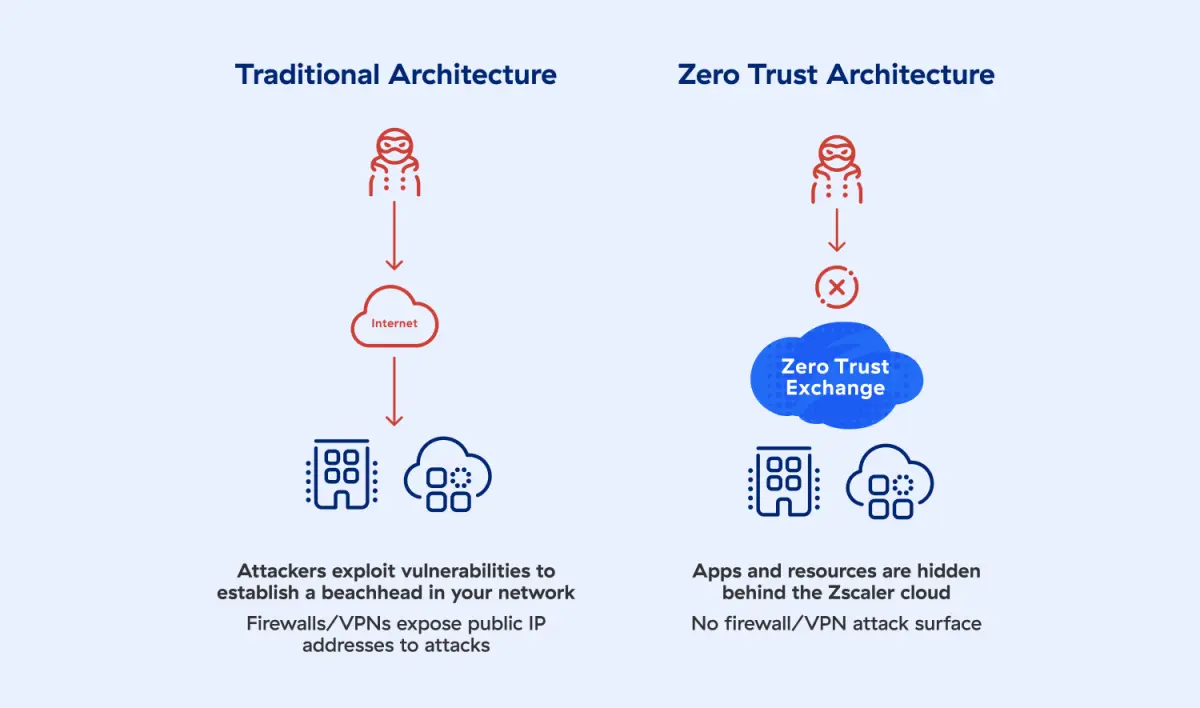
Minimiser la surface d’attaque
Les acteurs malveillants ne peuvent pas s’en prendre ce qu’ils ne peuvent pas voir. En masquant vos applications, emplacements et appareils sur Internet, Zscaler empêche les acteurs malveillants d’atteindre et de violer ces actifs.
Gestion complète de la surface d’attaque
Obtenir une vue globale de ce qui est exposé à Internet, des vulnérabilités et TLS/SSL faiblesses
Mettre en œuvre un accès Zero Trust aux applications
Contrôler l’accès des utilisateurs aux systèmes critiques (SSH/RDP/VNC)
Aucun accès à votre surface d’attaque
Maintenir les utilisateurs, les filiales et les usines cachés derrière le Zero Trust Exchange
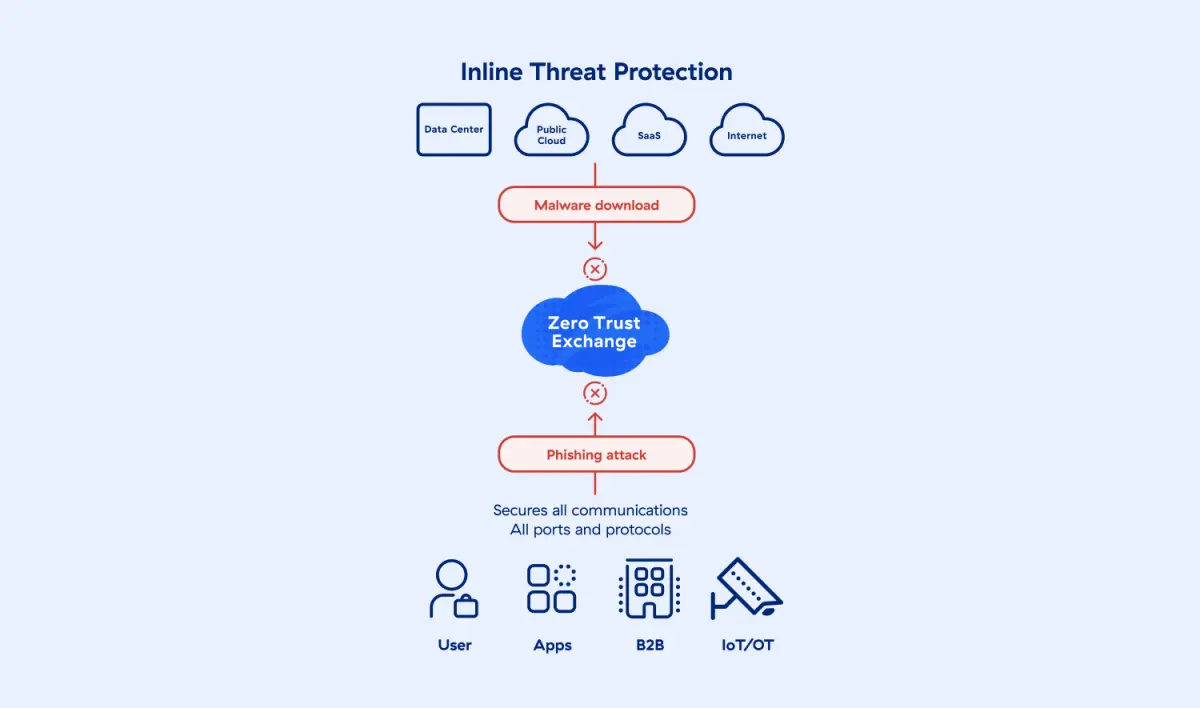
Empêcher l’intrusion
Éliminez les attaques de phishing et les téléchargements de malwares avec une inspection TLS inline complète à l’échelle et la prévention des menaces optimisée r l’IA, alimentée par plus de 320 milliards de transactions d’entreprise quotidiennes.
Isolation de navigateur
Transformer le contenu Web à risque en un flux de pixels inoffensif et dynamique
Anti-malware
Bénéficier d’une protection basée sur les signatures contre plus de 60 flux de menaces
Protection contre les menaces avancées
Tirer parti de l’analyse de contenu, de la corrélation et du score de risque
Cloud Sandbox
Appliquer une quarantaine intelligente pour une protection contre les vulnérabilités zero day
Protection des applications
Tirer parti du Top 10 de l’OWASP, des CVE et de protections personnalisées.
Éliminer le mouvement latéral
La segmentation Zero Trust n’exige aucune segmentation du réseau, votre réseau est simplement un transport. Minimisez le rayon d’action, protégez-vous contre les menaces internes et réduisez les frais opérationnels.
Segmentation de l’application
Appliquer la segmentation utilisateur vers application et application vers application
Accès privilégié
Contrôler l’accès des utilisateurs aux systèmes critiques (SSH/RDP/VNC)
Tromperie
Déployerdes leurres pour détecter et empêcher les utilisateurs infectés de se déplacer latéralement
ITDR
Maintenir la posture d’identité, l’hygiène et la détection active des menaces
Arrêter la perte de données
Découvrez l’informatique fanrtôme et les applications à risque avec la classification automatique des données sensibles. Sécurisez le trafic des utilisateurs, des charges de travail et de l’IoT/OT pour les données au repos et les données en mouvement avec la messagerie en ligne, le DLP des terminaux et l’inspection TLS à l’échelle.
DLP pour les terminaux
USB sécurisé, impression, partage réseau, synchronisation des clients, mode hors ligne
Cloud DLP
Inspection SSL complète, mise en œuvre inline, mode de surveillance et de blocage
CASB inline
Appliquer les contrôles d’application et de partage, les restrictions de location
Minimise la surface d’attaque, évite les compromissions, élimine les déplacements latéraux et arrête la perte de données
Élimine les produits ponctuels et la complexité, ce qui réduit les risques pour l’entreprise
Protection contre les menaces basée sur l’IA, alimentée par 500 000 milliards de signaux quotidiens et 320 milliards de transactions quotidiennes
Informations exploitables et flux de travail guidés pour la remédiation
Découvrez la puissance de Zscaler Zero Trust Exchange
Une plateforme complète pour sécuriser, simplifier et transformer votre entreprise
01 Business Analytics
Obtenez des informations et optimisez les risques, l’informatique et les performances commerciales.
02 Protection contre les menaces en ligne
Adoptez une approche globale de la sécurisation des utilisateurs, des charges de travail et des appareils.
03 Protection des données
Exploitez une inspection TLS/SSL complète à grande échelle pour une protection complète des données sur la plateforme SSE.
04 Zero Trust Networking
Bénéficiez d’une connexion aux applications, et non aux réseaux, pour empêcher tout déplacement latéral avec ZTNA.


L’impact d’un véritable Zero Trust, rapporté par les clients de Zscaler
Des milliers de transformations réussies reposent sur une unique base.


Zscaler accélère la transformation de la sécurité de CSR
L’architecte de sécurité de CSR, Dave Edge, explique comment Zscaler contribue à réduire les risques dans un paysage de menaces en constante expansion.

« Lorsque d’autres sociétés sont victimes d’attaques de ransomware […] je reçois des appels inquiets de dirigeants, et cela me fait chaud au cœur de pouvoir leur dire : Tout va bien pour nous. »
— Ken Athanasiou, vice-président et RSSI, AutoNation

« Nous avons complètement changé la posture [de sécurité] de l’État de l’Oklahoma au cours des 18 derniers mois. Zscaler a joué un rôle important. »
— Matt Singleton, RSSI, Office of Management and Enterprise Service, État de l’Oklahoma

Planifier une démo personnalisée
Appréciez votre exposition aux menaces et la façon dont la plateforme Zscaler Zero Trust Exchange peut transformer rapidement et en toute sécurité la façon dont vous travaillez.











