
It’s Time to Take Your Partners Off Your Network
Give them secure, segmented application access instead
Access is overextended when it comes to partners
Many enterprises have fallen victim to security breaches due to third-party partners. Stolen credentials or infected devices can quickly lead to costly security breaches that put the network at risk and expose sensitive data.
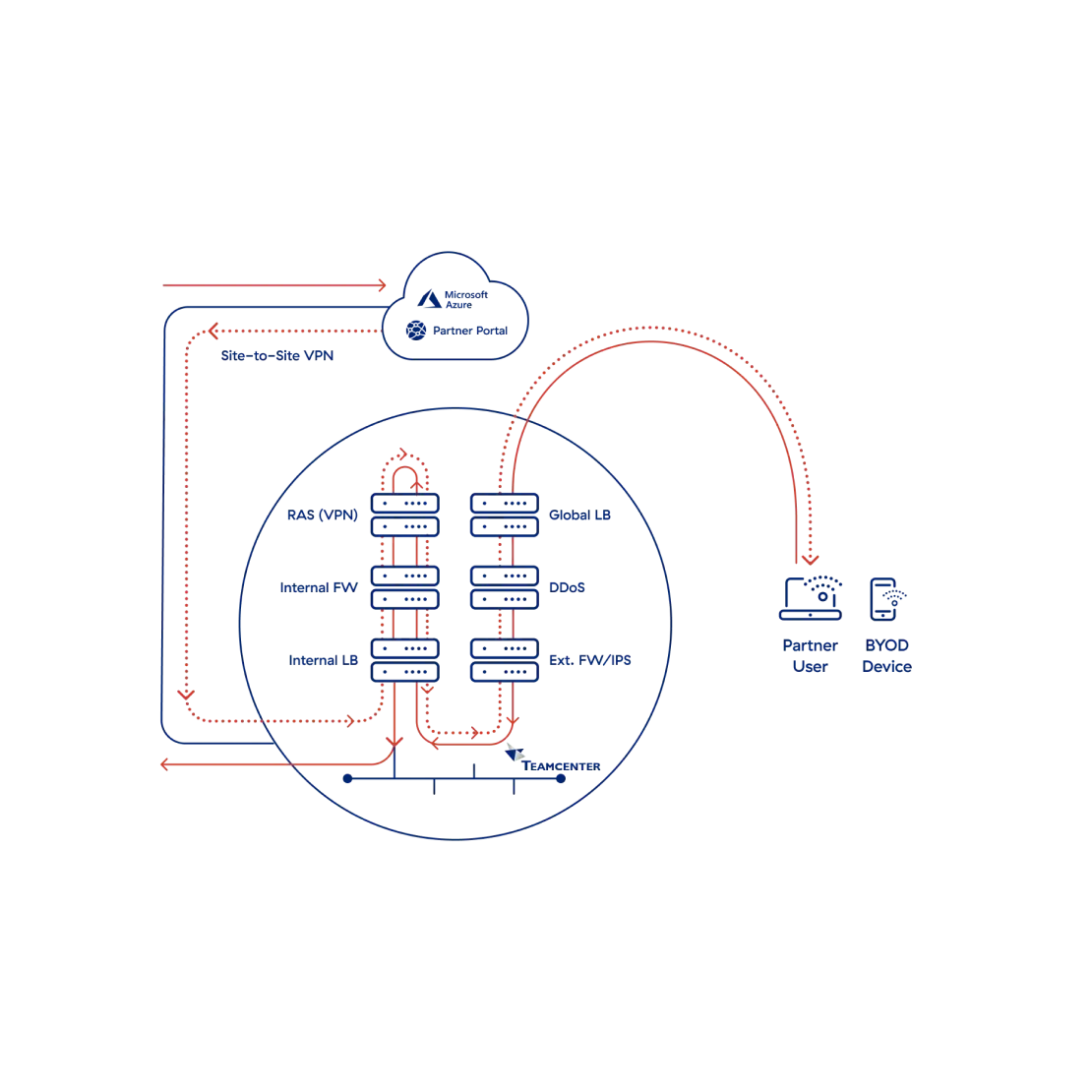
Most remote access solutions grant third-party partners full network access, introducing high risk to the enterprise because you ultimately don’t control the users or the devices they use to connect to your network.
How do you cultivate strong, productive partnerships while protecting your network and private applications?
Partners need application access, so why introduce them to the network?
It’s risky to extend full and lateral network access to your partners, but they need access to a subset of private apps. The solution is to decouple application access from the network while segmenting access based on individual users and apps. And that's only possible with zero trust network access (ZTNA).
While most remote access solutions are network-centric, ZTNA provides secure connectivity between the user and authorized enterprise applications—never the network—delivering microsegmented access that maintains security while reducing risks stemming from overprivileged third parties.
Before: Third parties were given lateral network access, exposing the network to risk.
After: ZTNA only gives third parties access to authorized private applications, not the network.
Before: Remote access required a client to be installed on a managed or personal device.
After: Browser access makes secure partner access seamless. Users can access authorized apps via browser, no matter their device or location.
Before: With remote access solutions, visibility into partner activity was limited to IP address and port data.
After: ZTNA delivers comprehensive visibility into all partner activity, down to the user, device, and named app level.
Eliminating third-party risk is easy with ZTNA
Zscaler Private Access™, the world’s most deployed ZTNA service, offers a user- and application-centric approach to network security, ensuring that only authorized users have access to specific internal applications—without ever providing access to the network.
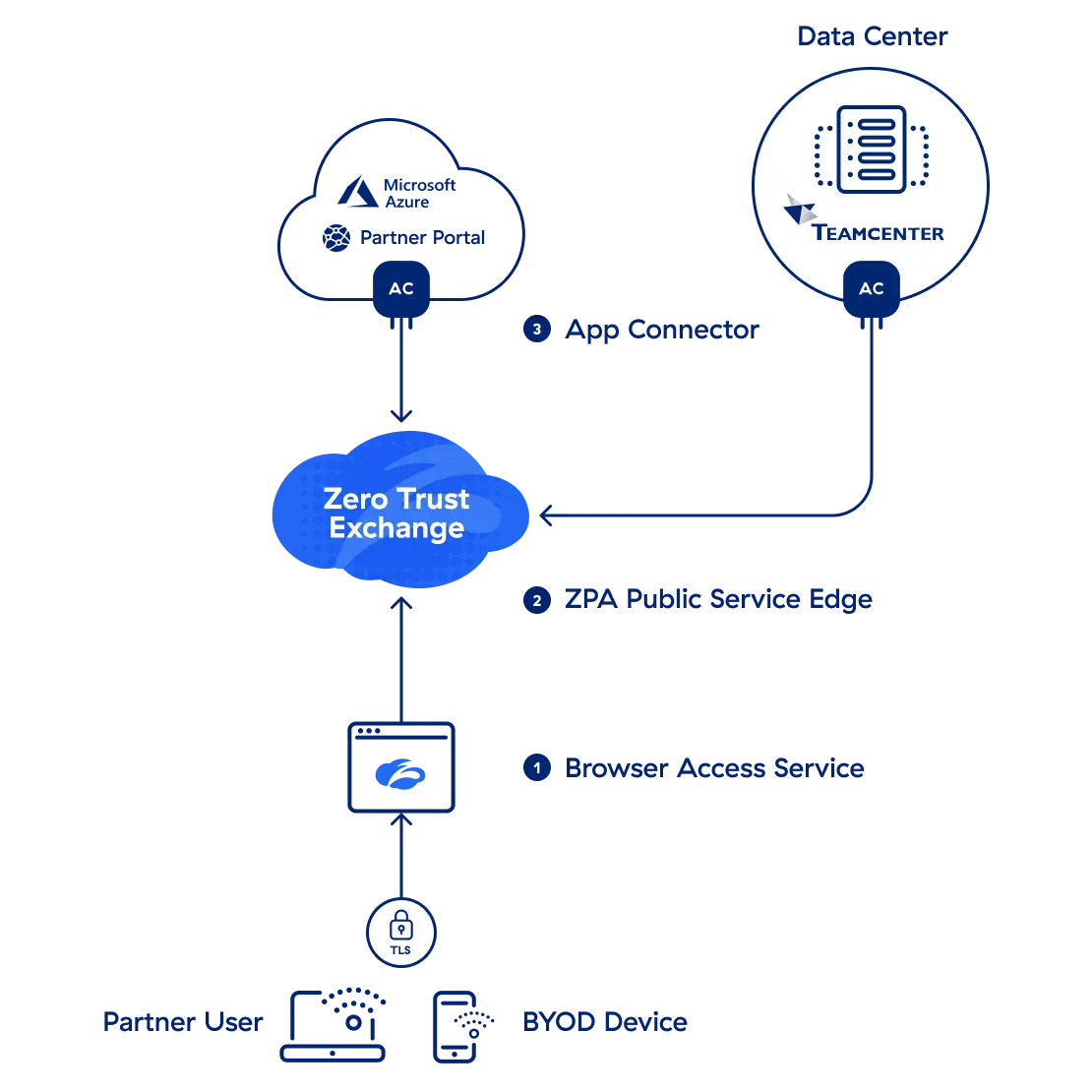
Rather than relying on physical or virtual appliances, ZPA uses lightweight infrastructure-agnostic software, paired with browser access capabilities, to seamlessly connect all types of users to apps via inside-out connections, stitched together within the Zscaler security cloud.
Software-defined perimeter concept
- A browser access service redirects traffic to IdP for authentication and removes the need for a software client on the device
- ZPA Public Service Edge secures the user-to-app connection and enforces all customized admin policies
- App Connector sits in front of apps in the data center and public cloud, provides inside-out TLS 1.3 connections to brokers, and makes apps invisible to prevent DDoS attacks


“Instead of [making users] connect to the environment and then go to the internal registration site to register their second factor tokens, we just [use] ZPA clientless access, and that works phenomenally.”
- Casey Lee, Director of IT Security, NOV
Browser access enables secure partner access in minutes
With ZPA browser access service, third-party partners and users gain secure application access without the need for a client. Partners can simply use their own devices to effortlessly access your private apps over the internet while you maintain granular control over that access, enabling users to connect to private applications anytime, anywhere, from any device.
Secure Third-party Access
Schedule a demo
Let our specialists show you how ZPA can quickly and securely transform your operations with zero trust network access.




