Transformez la façon dont vous trouvez et protégez les données
Bienvenue dans l’avenir de la protection des données
Dites adieu aux lacunes de protection et à une administration complexe grâce à la plateforme la plus révolutionnaire du secteur. Avec une protection complète sur le réseau et en dehors de celui-ci, associée à une découverte innovante des données, l’approche Zscaler de la DLP redéfinit la façon dont vous déployez et appliquez votre stratégie de protection.
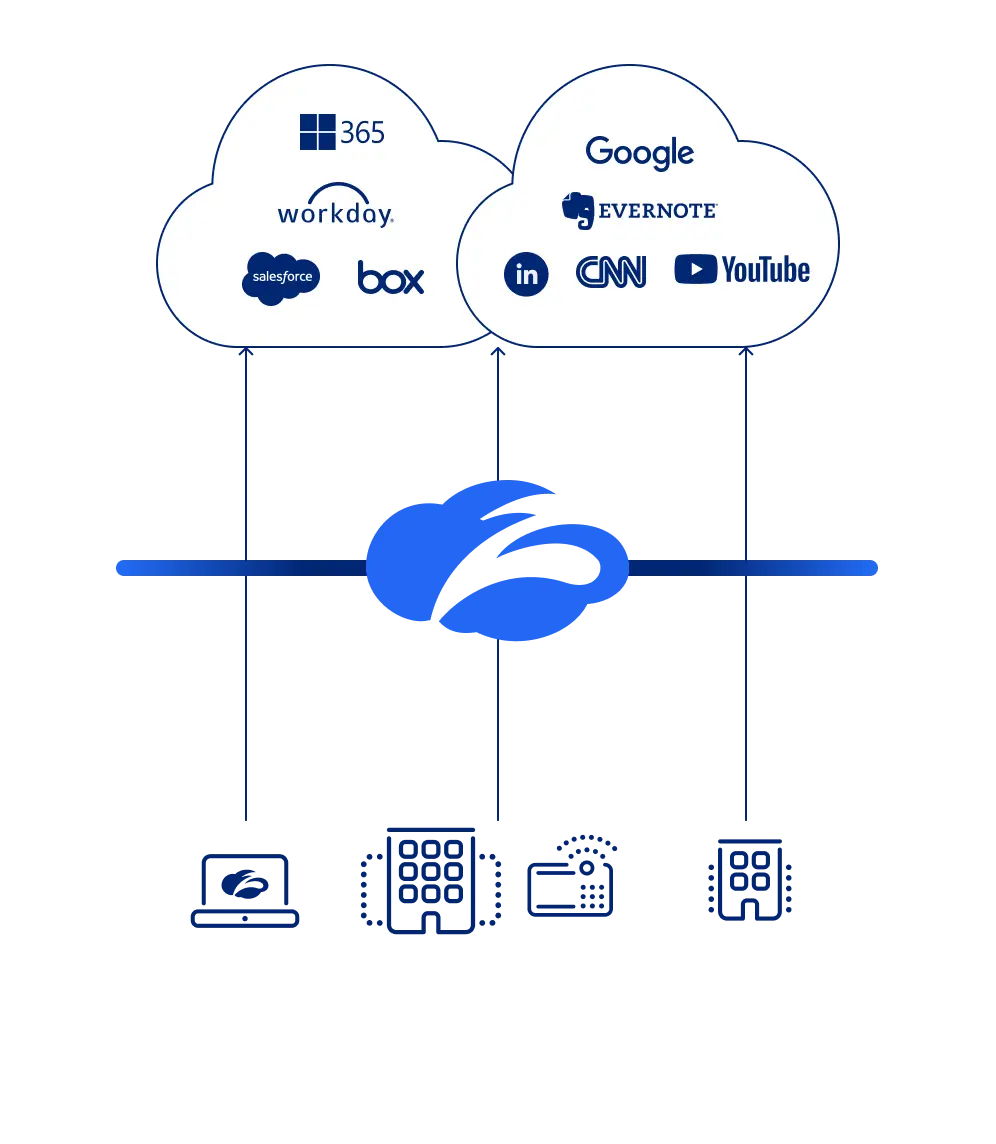
Bénéficiez d’une protection unifiée sur et hors réseau pour tous les utilisateurs. Sécurisez Internet, la messagerie électronique, les endpoints, les SaaS, les applications privées et la posture de risque dans une unique plateforme simple et puissante.
Gagnez du temps et accélérez de plusieurs mois votre programme de protection des données. Grâce à l’AA et à l’évolutivité du cloud, Zscaler classe automatiquement les données et les comportements à risque.
Faites passer la protection de vos données au niveau supérieur. Personnalisez-la selon vos spécifications grâce à l’UEBA, l’EDM, l’IDM, l’OCR et l’automatisation du flux de travail.


Transformation de la protection des données
De nouvelles innovations qui révolutionnent la protection des données.
Pourquoi choisir Zscaler DLP pour la protection des données ?
Zscaler exploite une plateforme cloud native de haute performance qui inspecte l’ensemble du trafic Internet et SSL tout en fournissant aux utilisateurs une sécurité rapide et cohérente, où qu’ils se trouvent.
Avec cette solution de DLP d’entreprise intégrée nativement dans Zscaler Zero Trust Exchange™, vous bénéficiez d’un SSE (Security Service Edge) complet, qui vous permet de supprimer les coûts et la complexité des produits ponctuels tout en fournissant :
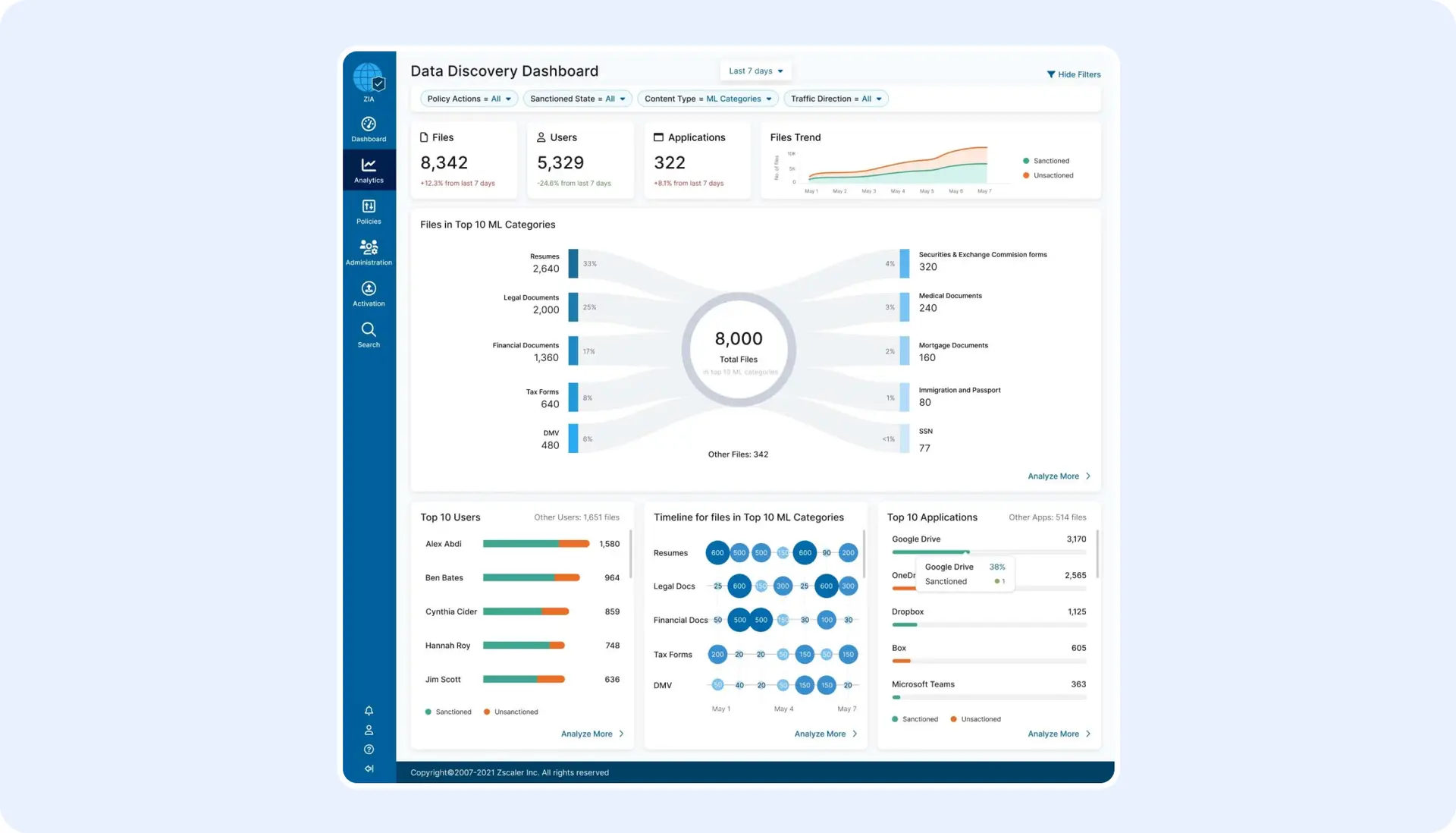
Découvrez la puissance d’une meilleure découverte des données
Avec une protection des données sans configuration, vous bénéficiez d’une visibilité exploitable sur toutes vos données.
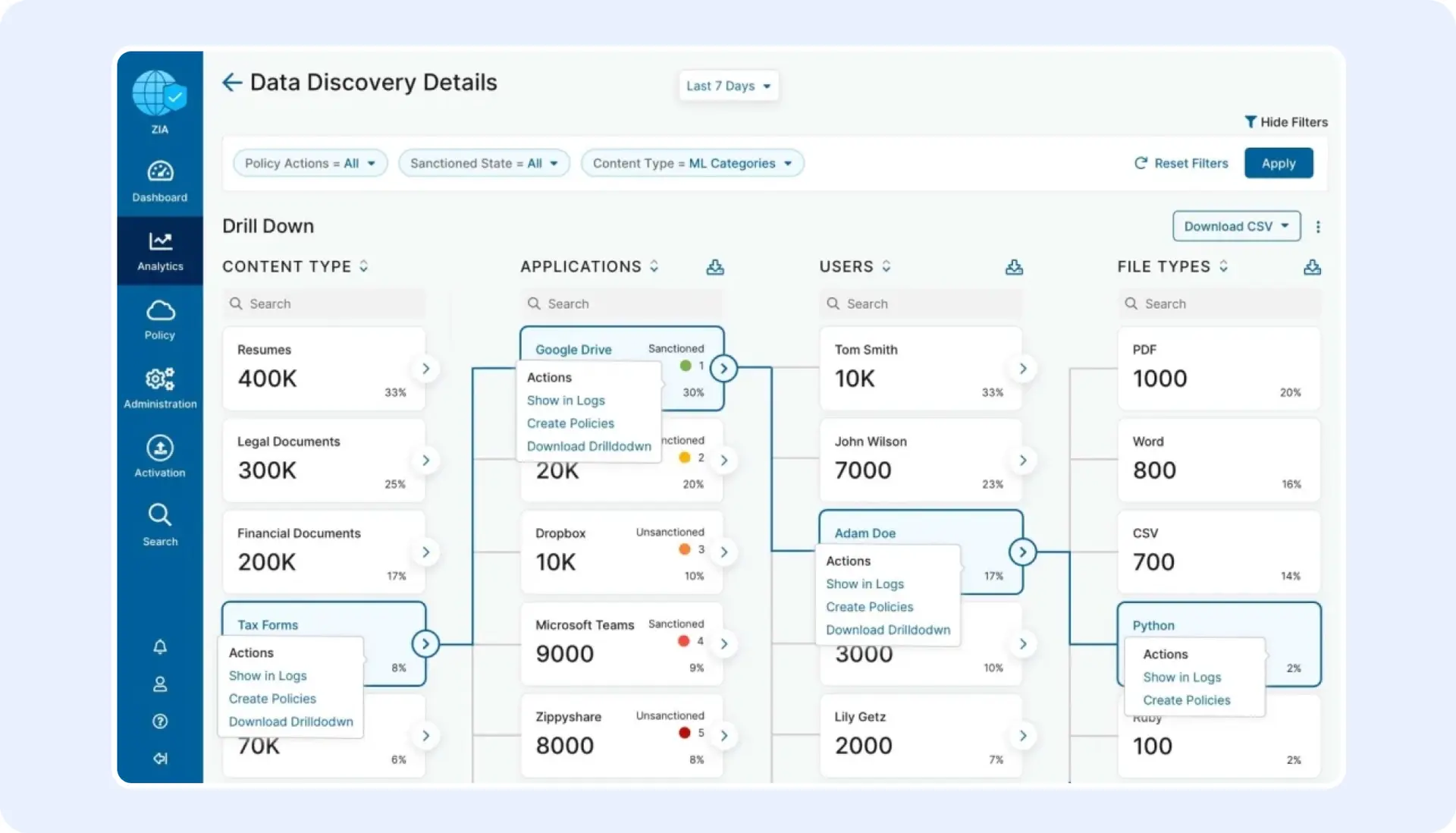
Identifiez sans peine les risques pesant sur vos données sensibles
Passez de la découverte des données à l’action en quelques clics seulement.

Introducing the AI Data Protection Platform
Join us as we unveil groundbreaking innovations to proactively discover, identify, and secure all your data.
Prêt pour une meilleure protection des données ?
Dans le monde du télétravail, une sécurité efficace des informations exige une solution unifiée conçue pour les données décentralisées et à l’échelle du cloud. Découvrez un meilleur moyen de sécuriser toutes vos données, où qu’elles aillent.
Fonctionnalités avancées
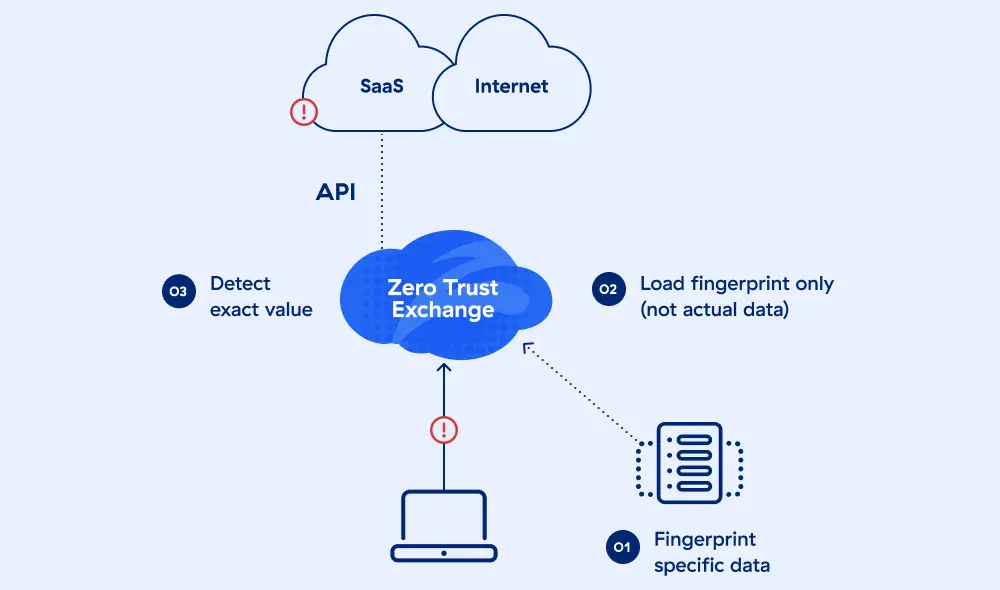
Améliorez la précision de la détection avec la correspondance exacte des données (EDM)
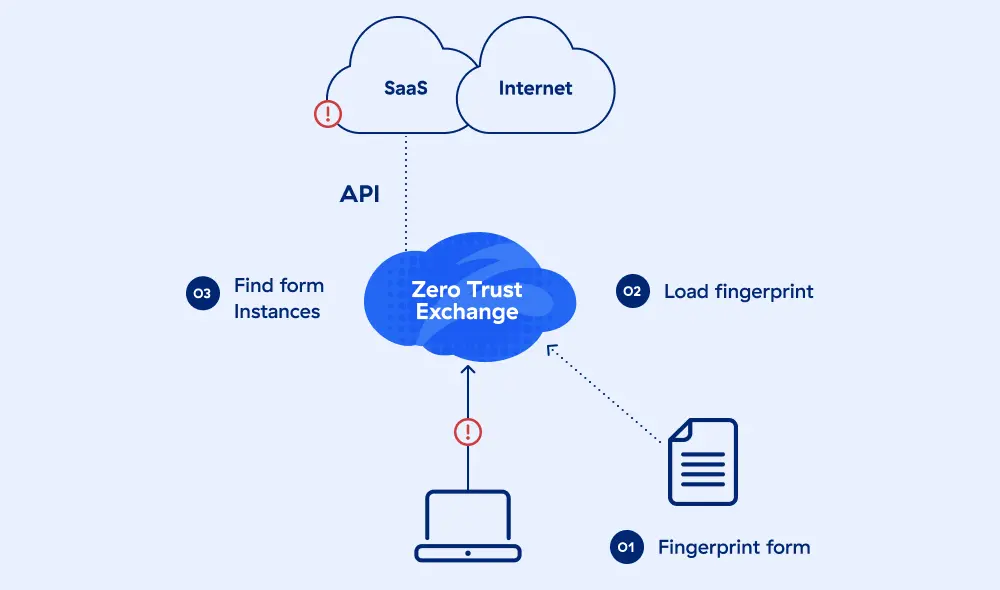
Zscaler EDM vous permet de facilement retrouver et contrôler toutes les occurrences de données spécifiques. Des dossiers des employés aux données personnelles des clients en passant par les numéros de cartes de crédit, l’EDM vous permet de prendre l’empreinte des données sensibles et d’améliorer la précision de la détection tout en réduisant les faux positifs de DLP.
Améliorez la précision de la détection avec la correspondance des documents indexés (IDM)
Avec Zscaler IDM, vous pouvez sécuriser les documents à forte valeur ajoutée qui contiennent généralement des données sensibles. Prenez les empreintes de formulaires fiscaux, médicaux, de fabrication ou d’autres formulaires importants, et détectez les documents qui utilisent ces modèles sur tous vos canaux de données dans le cloud.
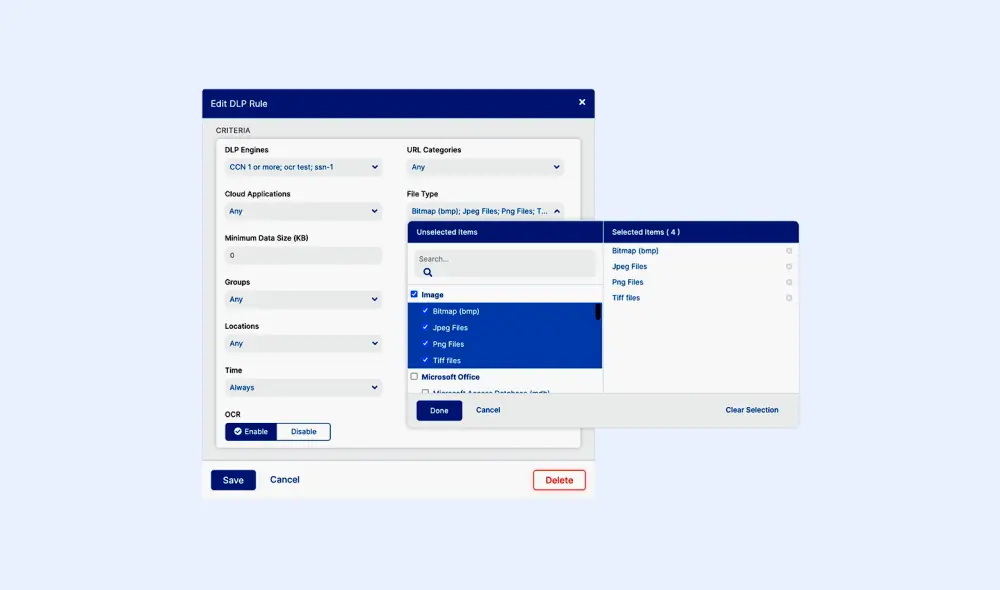
Protéger les données dans les fichiers d’image avec la reconnaissance optique de caractères (OCR)
Les données ne se présentent pas uniquement sous forme de texte brut ; vous devez donc disposer d’une DLP qui sécurise également les données visuelles. Zscaler OCR scanne les images pour effectuer une classification des données de fichiers tels que PNG et JPEG, ainsi que les images intégrées à d’autres types de fichiers (par exemple, des documents Microsoft Word). Il fonctionne même en tandem avec les fonctions EDM et IDM.
Votre DLP ignore-t-elle des cas de perte de données ?
<br />Découvrez-le avec Zscaler Security Preview.

Planifier une démo personnalisée
Nos experts vous montreront comment Zscaler protège votre entreprise contre la perte de données.






