Cet article a été initialement publié sur Medium.
Merci à Chris Wloch de Zscaler pour cette définition de Zero Trust…
« Si un voleur pénètre dans votre maison, il a un accès total à chaque pièce, à moins que vous ne verrouilliez également toutes les portes intérieures.
Verrouillez toutes les portes et exigez la vérification des empreintes digitales pour chaque accès. C'est ainsi que j'explique Zero Trust à mes grands-parents. »
Nous sommes maintenant dans la deuxième année de « la décennie numérique ». De nombreuses industries, capacités, produits et services traditionnels sont passés en ligne, soit dans le cadre de l'évolution digitale des entreprises, soit en raison de nouveaux besoins opérationnels imposés par la COVID au cours des douze derniers mois. Les entreprises de tous les secteurs (gouvernement, textile, poterie, assurance, finance, et tous les secteurs intermédiaires) passent au numérique. Et cela place le sujet de la sécurité et de la confidentialité au centre des préoccupations des cadres supérieurs.
Les attentes plus élevées des clients (et des utilisateurs finaux !) ont poussé les entreprises à évoluer pour adopter une expérience digitale. La sécurité et la confidentialité connaissent une évolution similaire, et c'est là que la philosophie, les plates-formes et les services de sécurité Zero Trust peuvent avoir un impact sur la prestation de services de votre entreprise, et changer la façon dont vous concevez votre marque, l'expérience client, la vitesse à laquelle vous opérez le changement, la facilité avec laquelle vous menez vos activités, et même votre réputation.
Les architectures de réseau et de sécurité de l'ère qui a suivi le boom des entreprises basées sur Internet ont été conçues pour la stabilité, la rigidité et le contrôle, et non pour l'agilité indispensable à l'évolution rapide des entreprises. Elles sont, de par leur nature intrinsèque, l'exemple même de l'inflexibilité. L'augmentation du volume de données implique une augmentation de la bande passante. Le trafic explose ? Ajoutez des boîtiers supplémentaires. Vous voulez instaurer le télétravail ? Ajoutez des boîtiers supplémentaires. (Ah, et bien sûr, l'approvisionnement en VPN est probablement encombré, donc la livraison sera différée). Pour les entreprises qui utilisent des piles d'appliances de sécurité en double, les idéaux de précision opérationnelle, d'optimisation des performances et d'agilité économique restent des chimères.
Le « retard des correctifs » : faire courir aux entreprises un risque inutile d'attaque
Le changement est difficile. Il est facile pour les services informatiques de se cantonner à un cadre restreint : la pile de matériel située au bout du couloir donne l'illusion d'un contrôle, d'une infrastructure à portée de main. De plus, il est facile de « faire avec ce que l'on connaît », et les certifications de sécurité existantes d'une entreprise peuvent, de manière compréhensible, orienter les décisions vers des technologies plus anciennes, basées sur le matériel.
Mais cette complexité est fatale. Apporter des changements, tels que des correctifs de sécurité, de nouveaux flux de travail réglementaires ou de conformité, dans un environnement encombré de piles et de piles de matériel nécessite une coordination globale considérable… une coordination globale manuelle considérable. Cela conduit inévitablement à des erreurs et, en fin de compte, à une plus grande exposition aux risques.
Alors, qu'est-ce que Zero Trust ?
Une architecture Zero Trust (ZTA) représente l'évolution dans le cloud du modèle de sécurité réseau traditionnel. Les entreprises progressistes transforment les opérations informatiques pour adopter la ZTA. Dans une entreprise ZTA, la sécurité est immédiate, fournie en ligne à partir de la périphérie du cloud, entre l'utilisateur et Internet (via un proxy web), ou entre l'utilisateur et l'application. Les performances sont optimisées car les déplacements de données sont réduits au minimum. Les connexions sont directes, éphémères et sécurisées, que ces connexions relient l'utilisateur à l'application, l'application à l'application ou le système au système. Il n'y a pas de frontière à franchir, et puisque les systèmes ne sont pas visibles sur l'Internet ouvert, la surface attaquable est réduite. Il n'y a pas de douves conceptuelles, pas de château métaphorique exposé (ou de châteaux voisins) que les adversaires pourraient piller (de manière horizontale).
Quelle est la justification économique de Zero Trust ?
En deux mots, une agilité sécurisée ! La ZTA permet à la sécurité de se concentrer sur des objectifs commerciaux partagés. Ainsi, la ZTA peut faire passer l'informatique du ministère du « non » au ministère du « c'est comme ça que l'on fait avancer les choses ».
La transformation numérique sécurisée de l'entreprise à l'aide de l'architecture Zero Trust semble être un choix facile pour une entreprise informatique : meilleure sécurité, plus grande résilience, performances plus rapides et coûts réduits.
Lorsqu'il s'agit de concurrence digitale, la vitesse compte, et il est impératif de conduire le changement à la vitesse de l'éclair. Dans les environnements traditionnels, apporter des modifications à l'infrastructure de pare-feu DMZ existante constitue un processus fastidieux, limité à un trafic plus faible et à une programmation de fin de semaine uniquement. La ZTA basée sur le cloud est dynamique, avec une sécurité basée sur des politiques qui peuvent être adaptées à la volée. Vous ne pouvez pas vous contenter de pouvoir changer une fois par mois alors que vos concurrents numériques en pleine évolution peuvent apporter des changements vingt fois par jour.
Efficacité, économies, temps : cartographier les impacts indirects de la ZTA
La ZTA basée sur le cloud constitue la prochaine évolution de la sécurité des entreprises. Mais cette simple réalité ne doit pas occulter son impact tangible sur une entreprise cliente : la ZTA est une solution d'entreprise qui apporte des avantages économiques. Comparons deux exemples, National Oilwell Varco et Company A.
Cent ordinateurs portables. C'est le nombre de machines que l'équipe informatique du DSI Alex Philips de National Oilwell Varco (NOV) devait reconfigurer chaque mois. Parfois, la réparation était d'ordre technique. Mais le plus souvent, la machine avait été infectée par un programme malveillant. Chaque ordinateur portable devait être expédié au siège, nettoyé, puis entièrement reconfiguré. Et 100 ordinateurs portables, c'était une moyenne : certains mois, entre 2013 et 2016, il a fallu désinfecter jusqu'à 200 machines.
D'un point de vue commercial, l'impact des programmes malveillants sur NOV était onéreux. La reconfiguration est un processus manuel, et chaque ordinateur portable individuel nécessitait un certain niveau d'attention spécifique. Du temps d'arrêt au remplacement des machines, en passant par la coordination des prêts, chaque étape du processus de nettoyage d'un ordinateur portable infecté avait un impact mesurable sur NOV : des données étaient perdues, la productivité diminuait, des coûts étaient engagés et des ressources étaient mobilisées, tout cela pour remettre aussi rapidement que possible un ordinateur portable en état de marche pour un employé. Philips a imaginé un monde dans lequel il n'était pas nécessaire d'en arriver là. Et après août 2016, ce ne fut plus le cas.
Company A s'appuie sur une infrastructure de réseau et de sécurité traditionnelle pour protéger le trafic de données de son entreprise. L'équipe informatique de Company A emploie une pile d'appliances matérielles traditionnelles dans son siège social pour sécuriser le périmètre de son réseau d'entreprise. Chaque machine à fonction unique de cette pile est répliquée dans ses 30 bureaux régionaux répartis dans le monde.
Chaque DMZ individuelle de Company A comprend 12 produits différents dans sa pile matérielle, chaque appliance remplissant un objectif discret de mise en réseau ou de sécurité. (Exemples de fonctions/appliances : pare-feu, filtrage d'URL, antivirus, DLP, inspection SSL, équilibrage de charge, protection DDoS, concentration VPN, sandboxing, etc.) Chacune des 30 DMZ de Company A mobilise deux personnes à temps plein pour la maintenance et l'exploitation de l'infrastructure matérielle de réseau et de sécurité. Chaque appliance individuelle sur chaque site doit être entretenue, avec des correctifs de sécurité mis à jour manuellement (et instantanément). Le provisionnement de ces équipements exige une évaluation des fournisseurs et des produits, des flux de travail d'approvisionnement, un soutien administratif inter-divisions et une importante planification initiale.
Le directeur technique de Company A dirige plus de 60 employés et supervise l'achat, la maintenance et l'exploitation de 360 appliances individuelles de réseau et de sécurité. Le budget annuel du directeur technique s'élève à plusieurs dizaines de millions de dollars.
Que permet d'acheter l'énorme budget du directeur technique de Company A ? Certainement pas une meilleure sécurité. Certainement pas la tranquillité d'esprit. Au lieu de cela, il plonge le directeur technique dans un cercle vicieux de futilité, réagissant à chaque nouvelle menace, faille matérielle ou incendie métaphorique, tout cela pour rester en phase avec les hackers qui se préparent à attaquer. (Ces hackers, soit dit en passant, sont bien financés, parfois parrainés par un État, leurs méthodes deviennent de plus en plus ingénieuses au fil du temps, et leurs intentions de plus en plus destructrices.)
« Alors… pourquoi êtes-vous impliqué dans la sécurité du réseau ? »
Les dirigeants d'entreprise qui s'accrochent (ou permettent tacitement à leurs services informatiques de s'accrocher) à des modèles de sécurité dépassés le font à leurs risques et périls, au grand détriment de leur gagne-pain, et au grand détriment de leur entreprise. Ce faisant, ils limitent l'agilité organisationnelle, engagent des frais généraux inutiles, entravent la croissance et compliquent la gestion opérationnelle.
Le maintien d'un matériel traditionnel obsolète confronte également le service informatique d'une entreprise au problème de la sécurité des réseaux, avec un directeur technique chargé d'exploiter un NOC et une infrastructure destinés à contrer une vague croissante d'adversaires.
Les dirigeants d'entreprise qui conservent une infrastructure non sécurisée et obsolète ont la responsabilité de justifier ces pratiques dépassées ou de les moderniser : pourquoi l'entreprise s'implique-t-elle dans la sécurité du réseau ? Peut-elle sécuriser les données, les utilisateurs, les actifs et les ressources de son entreprise mieux qu'un fournisseur de services cloud dont les milliers d'experts en sécurité travaillent 24 heures sur 24 et 7 jours sur 7 pour bloquer les toutes dernières menaces adverses ? Peut-elle anticiper la prochaine menace qui pèse sur la chaîne d'approvisionnement ? Peut-elle appliquer instantanément les correctifs ? (Vraiment, vraiment instantanément ?)
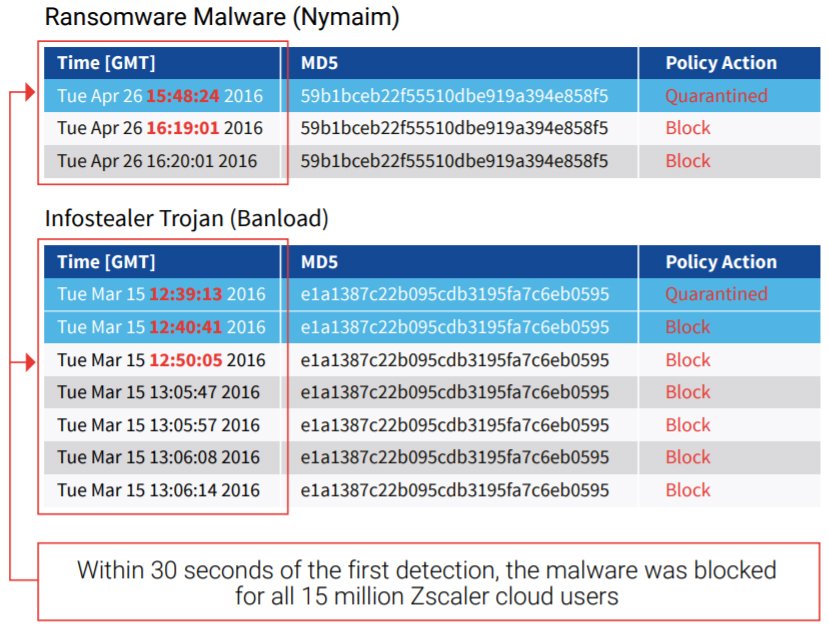
Figure 1. En mars 2016, des hackers ont ciblé un client de Zscaler qui disposait d'une architecture Zero Trust. Zscaler Cloud Sandbox a analysé les menaces et, en l'espace de 30 secondes, les a bloquées pour ce client et pour tous les millions d'utilisateurs du Zero Trust Exchange basé sur le cloud répartis dans le monde.
L'architecture Zero Trust : le nouveau coût (réduit) des activités
Alex Philips, directeur informatique de NOV, connaît l'impact pratique d'une architecture Zero Trust. Il a dirigé la transformation numérique sécurisée de NOV, en adoptant un modèle Zero Trust en août 2016. En passant à une sécurité assurée par des proxy web d'edge-computing, NOV a entièrement supprimé ses DMZ. En réduisant sa dépendance aux réseaux MPLS et à la sécurité matérielle, NOV a « réduit de plusieurs dizaines de millions de dollars son budget [informatique]. » Les employés de NOV bénéficient désormais d'une meilleure connectivité (plus rapide), d'une plus grande sécurité (avec une inspection SSL/TLS complète) et d'un meilleur accès aux appareils mobiles (ce qui s'est avéré particulièrement utile lorsque la société est passée au télétravail l'année dernière). Depuis que Philips et NOV ont adopté une architecture Zero Trust, son équipe informatique ne reconfigure qu'un ou deux ordinateurs portables par mois, ce qui permet au personnel de se concentrer sur les objectifs stratégiques essentiels à l'entreprise.
Comme l'année écoulée l'a démontré, la capacité de basculer constitue un avantage concurrentiel essentiel pour les entreprises. Dans chaque secteur, de nouveaux acteurs utilisent l'agilité pour bouleverser les choses. Une architecture Zero Trust apporte cette agilité. Et une meilleure sécurité. Et de meilleures performances. Les parties prenantes doivent être plus exigeantes vis-à-vis des dirigeants d'entreprise : si ces derniers devaient concevoir l'infrastructure opérationnelle, les flux de travail et les opérations à partir de zéro, ressembleraient-ils à ce qu'ils sont aujourd'hui ? Et si ces dirigeants pouvaient utiliser une architecture Zero Trust pour assurer une meilleure sécurité, une plus grande souplesse, une réduction significative des coûts et une diminution significative des risques, pourquoi s'en priveraient-ils ?





