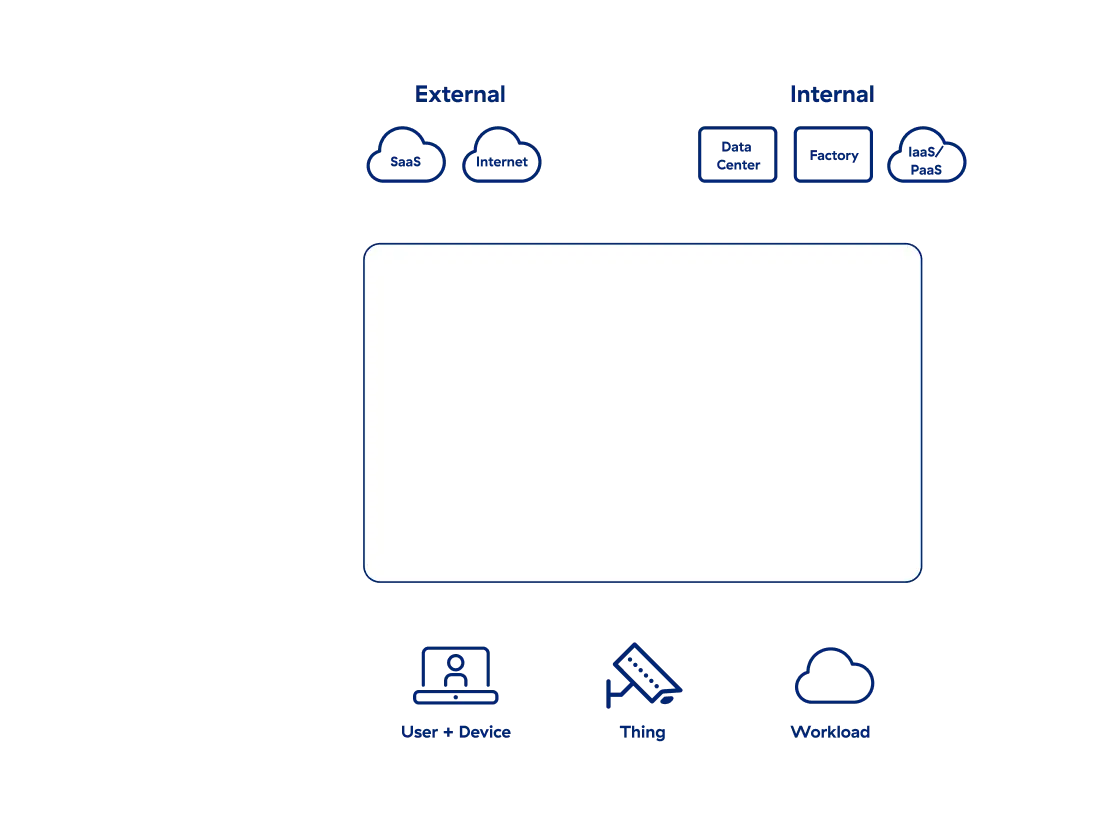
Sept éléments d’une architecture Zero Trust efficace
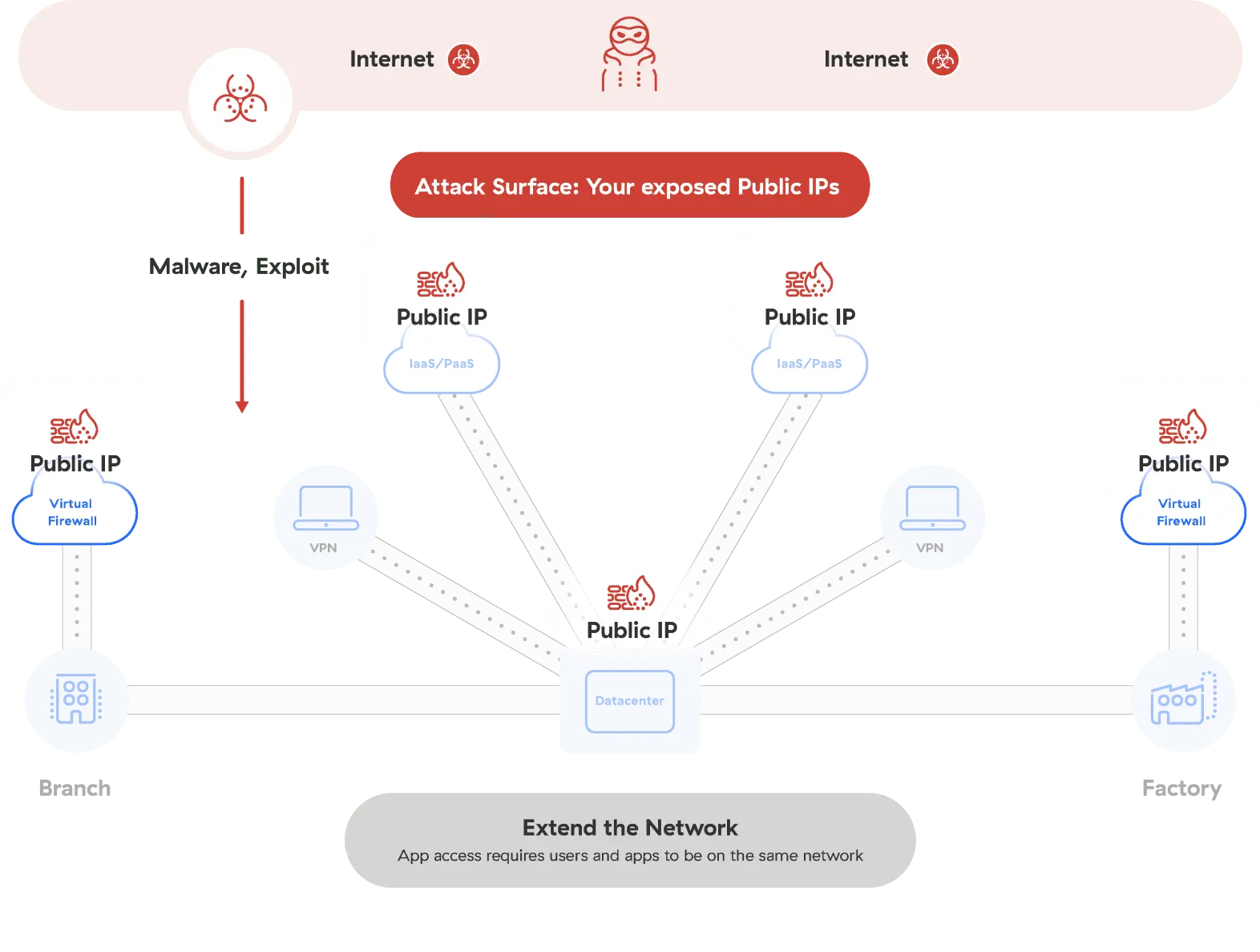
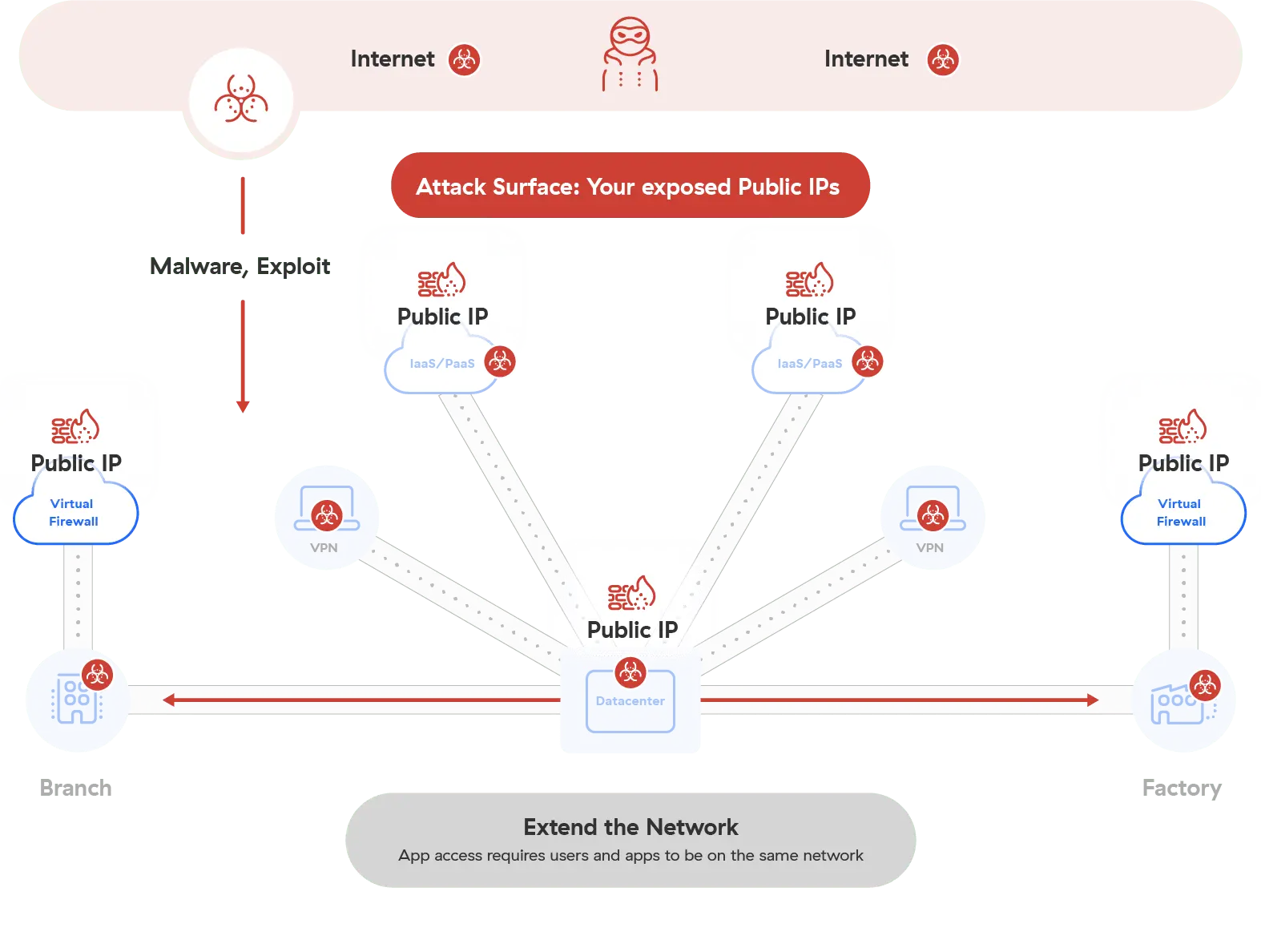
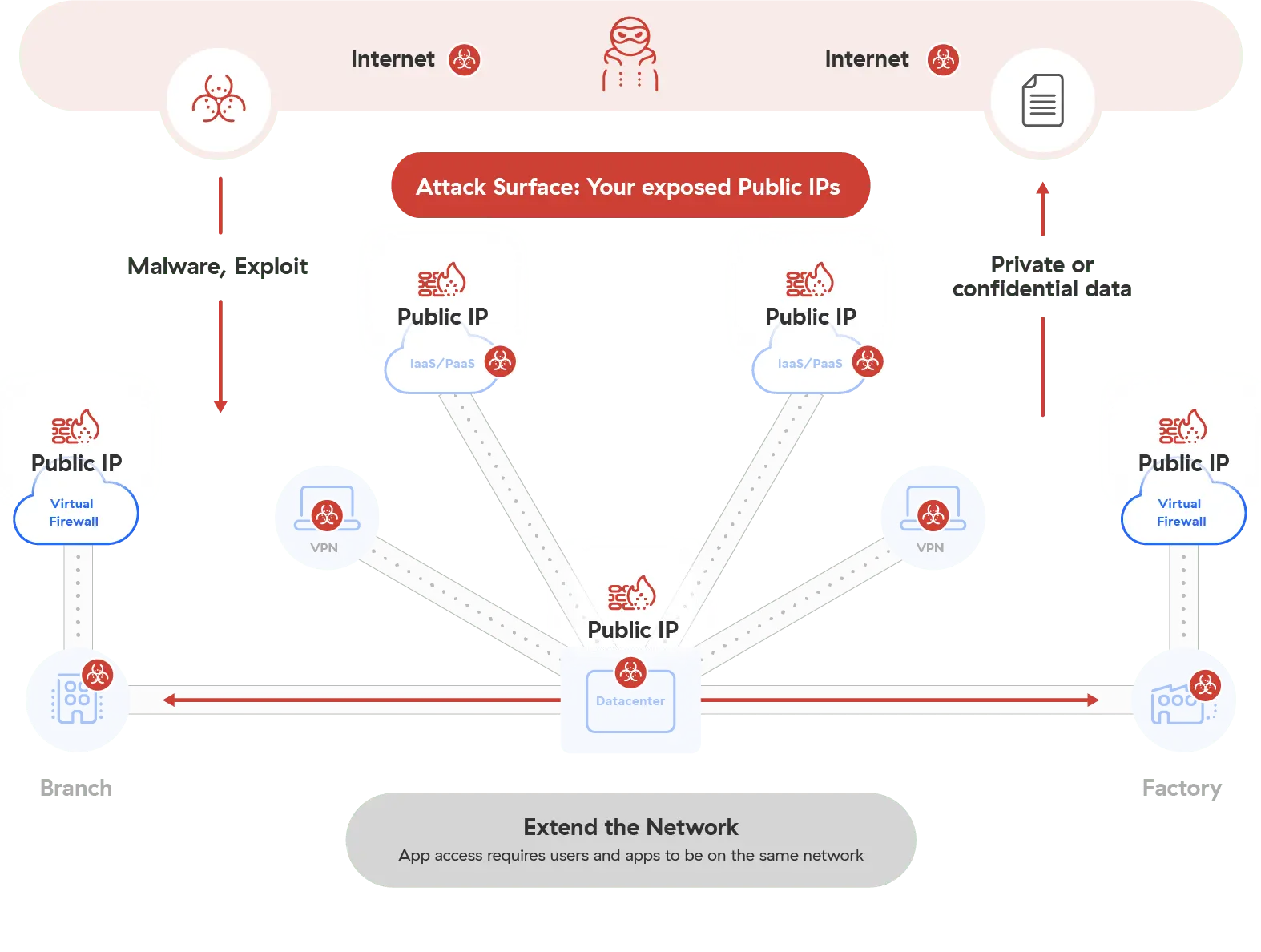
Les architectures traditionnelles vous exposent aux attaques
Les approches traditionnelles en matière de réseau et de sécurité, telles que les VPN et les pare-feux, perdent de leur efficacité à mesure que les applications migrent vers le cloud et que les utilisateurs travaillent de n’importe quel endroit. Ces approches exigent que les utilisateurs se connectent au réseau, ce qui laisse la porte ouverte aux hackers pour compromettre les données sensibles et infliger des dommages substantiels à votre entreprise.

Une sécurité complète pour votre transformation digitale
Pour être performantes dans l’environnement de travail hybride moderne, les équipes informatiques et de sécurité doivent repenser la mise en réseau et la sécurité. C’est là qu’une architecture Zero Trust entre en jeu. Zero Trust désigne une solution de sécurité globale qui repose sur l’accès sur la base du moindre privilège et l’idée qu’aucun utilisateur ou application ne devrait être intrinsèquement considéré comme fiable. Elle suppose que toutes les connexions sont hostiles et n’accorde l’accès qu’une fois l’identité et le contexte vérifiés, et les contrôles de politique appliqués.
Zscaler fournit une solution Zero Trust par le biais de Zero Trust Exchange : une plateforme intégrée, cloud native, qui connecte en toute sécurité les utilisateurs, les charges de travail et les appareils aux applications, sans se connecter au réseau. Cette approche unique élimine la surface d’attaque, empêche le déplacement latéral des menaces, et protège contre la compromission et la perte de données.
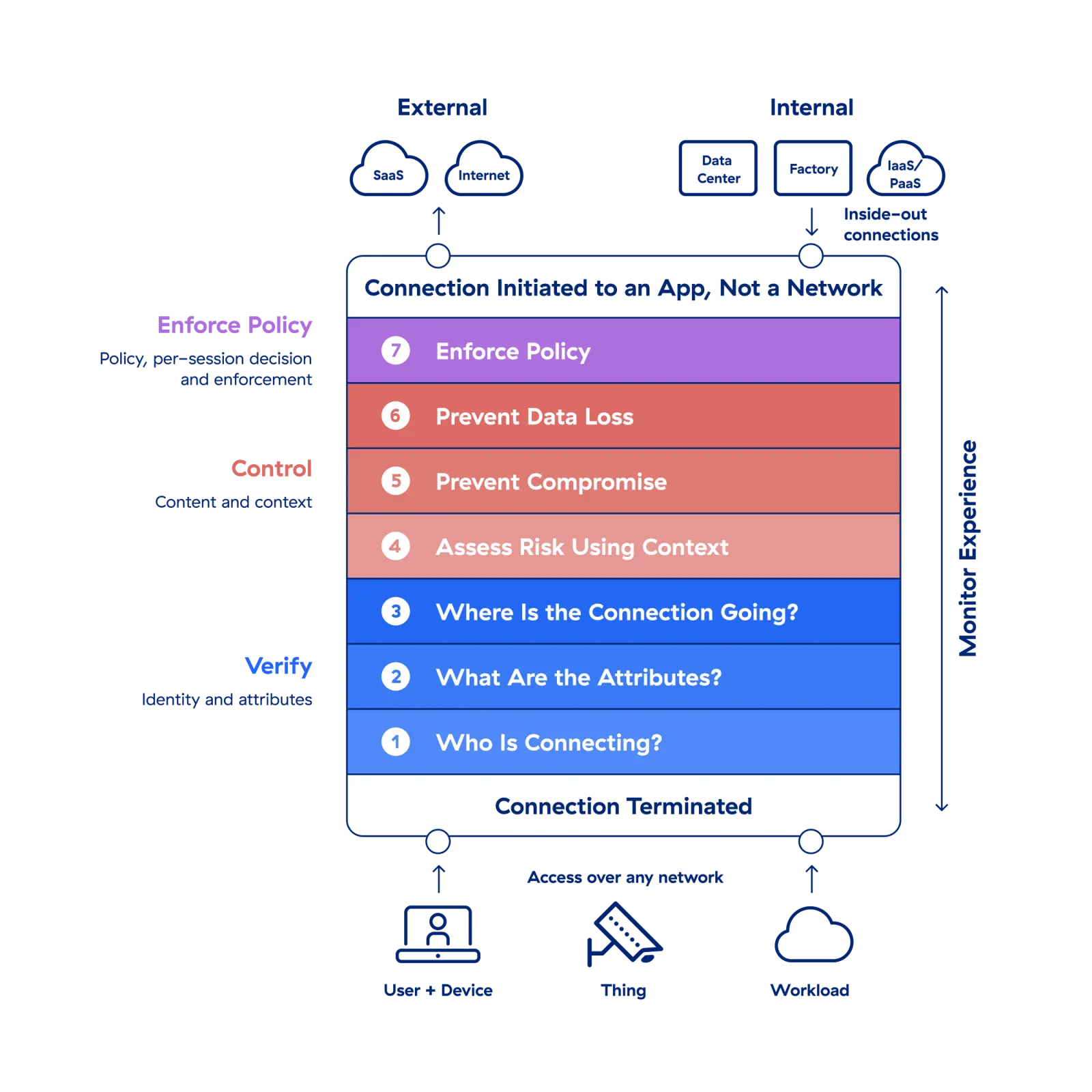
Découvrez une architecture Zero Trust à l’œuvre
Vérifier l’identité et les attributs
Contrôler le contenu et le contexte
Appliquer la politique : décision et application par session
Découvrez l’architecture Zero Trust à l’œuvre
Suivez Jane et John Doe dans leur cheminement à travers le processus de Zero Trust d’accès aux applications pour découvrir comment Zscaler Zero Trust Exchange applique les sept éléments.