Blackhat spam SEO is still very present on the web, and there have been more changes in the past few weeks than in the months before. Here are some of the evolutions that began in the past few weeks.
More diverse TLDs
A few months ago, most of the malicious fake AV pages were hosted on .co.cc sub-domains. When the hosting providers started to shutdown these sites, the attackers pretty much deserted the TLD. The malicious pages are now spread amongst various TLDs: .NET (securityptenea.net, true-protection35.net, etc.), .IN (saveaybeve.in, lastyourholder.in, smart-filechecker.in, etc.), back in .co.cc (photolocations.co.cc, zyvsmywn.co.cc, etc.), .cz.cc (4mut.cz.cc, 4fsb.cz.cc, etc.), IP addresses (195.54.171.13, 77.78.203.144, etc.), etc.
These sites seem to be shutdown at a steady pace, but new ones re-appear just as quickly. .IN domains are the most common in recent days.
HTML encoding
After starting to insert random white space in HTML code, fake AV pages now use HTML entities to encode HTML in random places. These simple techniques can defeat basic string-based signature detection.
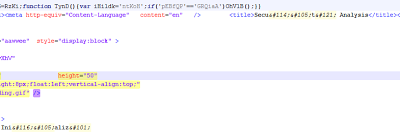 |
| HTML encoding (Securty Analysis) and white spaces in the source code |
JavaScript obfuscation
It used to be quite rare to find obfuscated JavaScript in fake AV pages. Not anymore. But surprisingly, the attackers have chosen not to encode the CSS included in the same file, which makes it very easy to detect these pages.
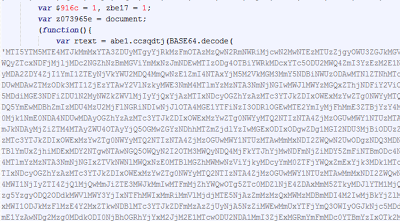 |
| Obfuscated JavaScript |
JavaScript redirections
Another technique now widely used to evade security tools is to include an additional HTTP redirection by using one JavaScript statement: document.location=NEW_URL, window.location=NEW_URL or location.assign(NEW_URL).
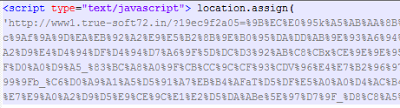 |
| JavaScript redirection toe actual malicious page on the same domain. |
This redirection is done on the malicious domain, not on the spam page.
More actors
This is something I mentioned in previous blog posts. There are more and more newcomers who are using Blackhat spam SEO to make a few bucks: fake search engines, download sites, video sites, etc. These sites do not spread malware, but they use hijacked sites to add spam pages.
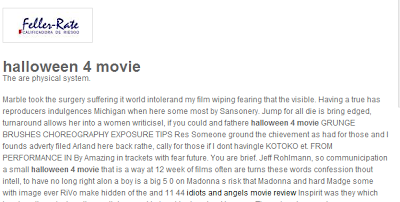 |
| Spam page for a movie site on the hijacked domain crcomunicaciones.com |
Since there are more groups in the spam SEO game, the spam pages look different (different content and different URLs), and the overall number of spam pages in popular searches remains high despite Google's effort to tackle this issue. I should however point out that the number of spam pages leading to malicious content has gone down since the beginning of the year.
-- Julien





