30% of Internet traffic is in some way related to pornography and this is the primary reason why malware authors are using porn apps to infect large numbers of users. During recent data mining, we noticed an increasing volume of mobile malware using pornography (disguised as porn apps) to lure victims into different scams and stealing personal data or locking phones and demanding ransom payments. We recently wrote about Android Ransomware and an SMS Trojan leveraging pornography to scam victims. In this blog we share the analysis of two adult themed malicious apps - SMS and Infostealer Trojans that we recently spotted.
Case 1: SMS Trojan
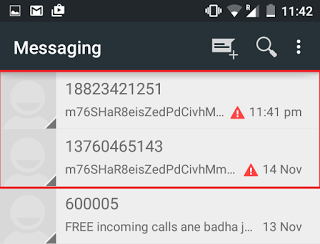
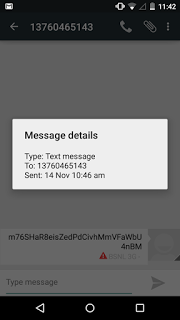
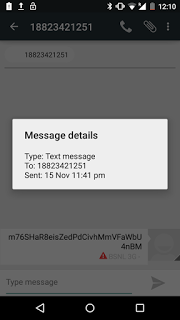
Here we look at a Chinese SMS Trojan disguised as porn app. Upon installation, the malware fools the victim by displaying random adult sites, steals sensitive information and sends SMS to predetermined Chinese numbers in the background.
- Name : 浴室自拍
- URL: http://yg-file.91wapbang[.]com/apk/appad/14461771841467103.apk?uid=ef2592f22af8c568f2b2993467a1e21a
- Package Name : com.uryioen.lkhgonsd
- Flagged by 6/53 AVs on VirusTotal at the time of analysis.
| Icon |
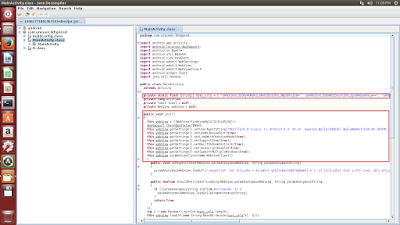
Once a user clicks on the icon, the user will be directed to a random URL from an array defined in the main code module. Interestingly, all the URLs are encoded in base64 format.
 |
| Base64 URLs |
List of URLs:
- http://www.4493[.]com/star/sifang/(aHR0cDovL3d3dy40NDkzLmNvbS9zdGFyL3NpZmFuZy8=)
- http://m.mnsfz[.]com/h/meihuo/(aHR0cDovL20ubW5zZnouY29tL2gvbWVpaHVvLw==)
- http://m.4493[.]com/gaoqingmeinv/(aHR0cDovL20uNDQ5My5jb20vZ2FvcWluZ21laW52Lw==)
- http://www.mm131[.]com/xinggan/(aHR0cDovL3d3dy5tbTEzMS5jb20veGluZ2dhbi8=)
- http://www.5542[.]cc/xingganmeinv/(aHR0cDovL3d3dy41NTQyLmNjL3hpbmdnYW5tZWludi8=)
- http://www.100mz[.]com/a/xingganmeinv/(aHR0cDovL3d3dy4xMDBtei5jb20vYS94aW5nZ2FubWVpbnYv)
- http://m.xgmtu[.]com/( aHR0cDovL20ueGdtdHUuY29tLw==)
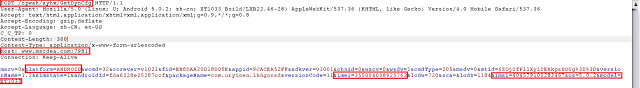 |
| Post Request |
The C&C server responds back to the bot with further instructions as seen below.
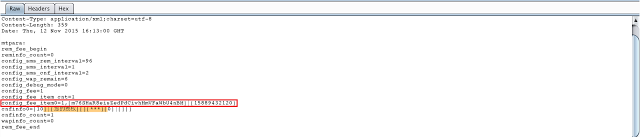 |
| Response |
The C&C response in screenshot shows the malware receiving a phone number with content that needs to be sent to that number via SMS. The following code shows how the malware will parse this response and start sending SMS messages.
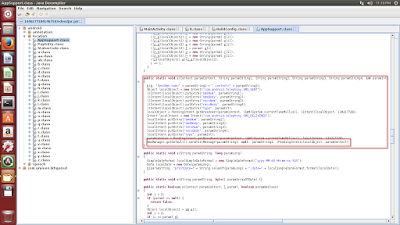 |
| Send SMS code |
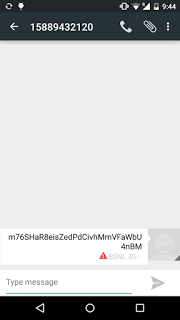 |
| SMS |
After sending the message, the malware sends another POST request notifying the C&C server about the sent SMS activity.
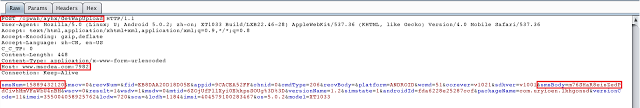 |
| Post Request |
- C&C server - http[:]//www[.]mscdea[.]com:7981
This activity occurs once a day at a random time interval where the malware sends a post request to the C&C server and receives phone numbers with SMS content to be sent out.
The continuous SMS activity can lead to a significant financial loss for the victim.
Case 2: Fake Ransomware stealing personal data
The malware in this case is trying to scare the user with a warning screen accusing them of watching child porn. The malware steals victim's personal data in background and send it to C&C server.
- URL: http://maturefuckporn[.]info/download/kyvcuwc/diper/video.apk (down as of now)
- App Name : video
- Package Name : com.gi.to
- Flagged by 12/53 AV vendors on VirusTotal.
Upon installing the app on device, the user will see a video player icon on the screen.
 |
| Icon |
Once the user clicks on the icon, the malware displays a fake warning page as seen below. The warning page pretends to be from the Industrial Control Systems - Cyber Emergency Response Team (ICS-CERT) but is different from the classic FBI/Police Ransomware pages.
 |
| Warning page |
The malicious app does not ask for administrative privileges to lock the device and is fairly easy to remove. We did not find any code for locking the device. The malware harvests inbox messages, contacts & e-mail addresses, which are then relayed to a remote C&C server in the background.
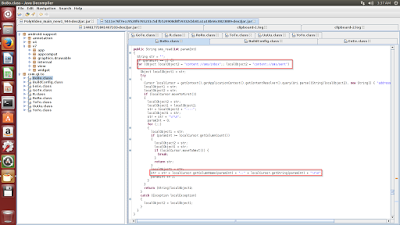 |
| Collecting data |
The malware logs the harvested SMS messages & sender's phone number in a specific format to a temporary file as seen in the code snippet above.
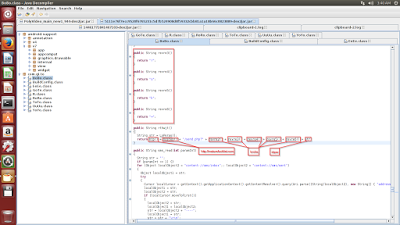 |
| C&C construction. |
The screenshot above shows the C&C URI construction code. The file containing the stolen data is then sent to the remote C&C server as seen in the network capture below.
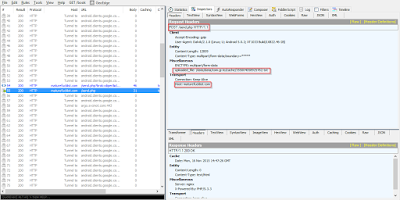 |
| Post capture. |
The stolen SMS messages being sent to the C&C server in a file.
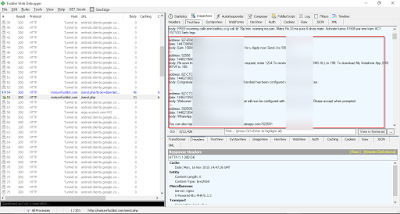 |
| Inbox messages |
The stolen contacts & e-mail addresses being sent to the C&C in a file
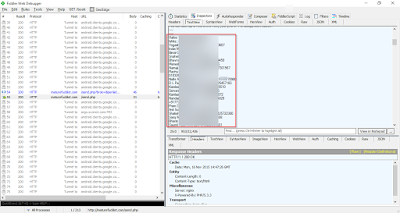 |
| Contacts |
- C&C server - http[:]//maturefucklist[.]com
Conclusion
We are seeing an increasing number of adult themed Android malware apps using pornography to lure victims. To avoid being a victim of such malware, it is always best to download apps only from trusted app stores, such as Google Play. This can be enforced by unchecking the "Unknown Sources" option under the "Security" settings of your device.