Introduction
Marcher is sophisticated banking malware that steals users’ financial information, such as online banking credentials and credit card details. We have observed Marcher evolving over time, using new tricks and payload delivery mechanisms. As we reported about previous encounters with this malware here, here, and here, the authors are using new techniques to spread infections, such as pornographic lures and the hype around new games.
In a recent wave, we are seeing the malware payloads disguised as Adobe Flash player. Upon opening the dropper URL, the user will be prompted by a message saying the device’s Flash Player is out of date, and the malware “Adobe_Flash_2016.apk” will be dropped on the user’s device. The malware will also guide the user to disable security and allow third-party apps to install, as shown in the screen below.
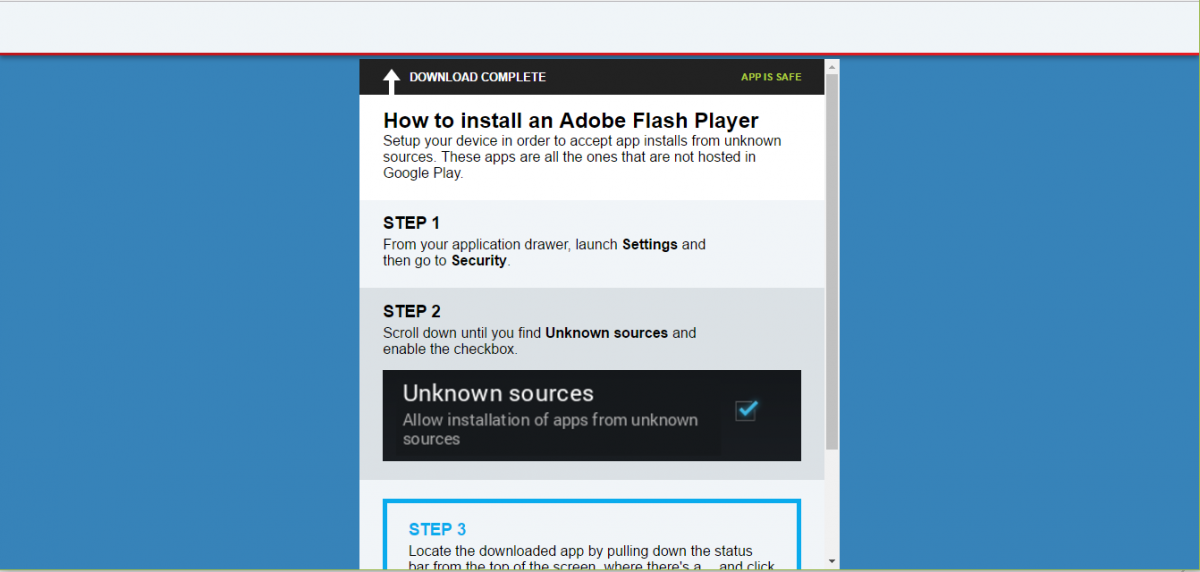
Fig 1: Payload delivery
We saw multiple payloads being served where popcash.net ads were the initial source of infection.
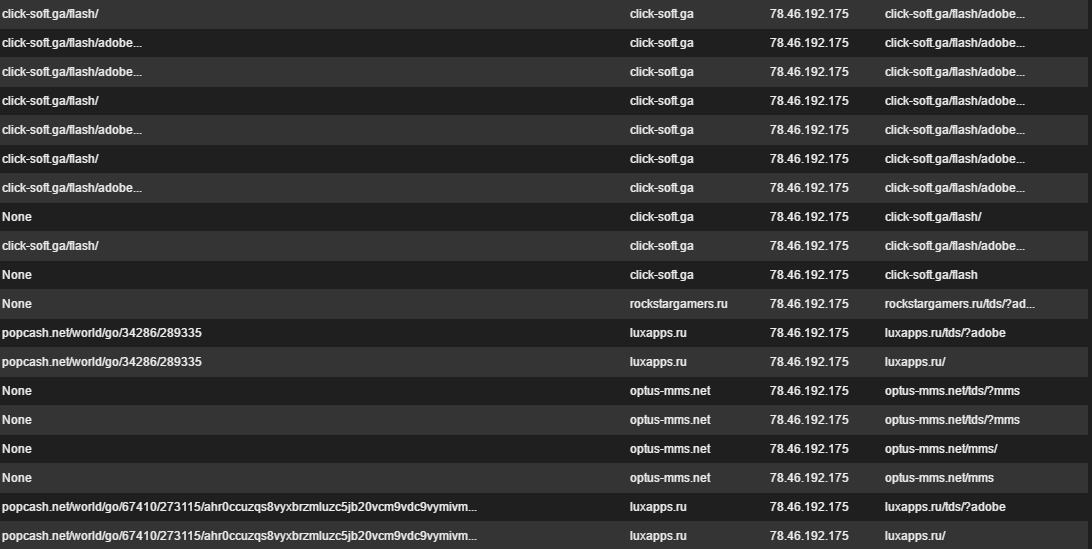
Fig 2: New Android Marcher wave
Upon installation, the malware quickly hides and removes its icon from the phone menu.
Following infection, the malware will register the infected device to its Command & Control (C&C) server. Along with the device’s meta information, the installed apps list is sent to the C&C server as shown below.
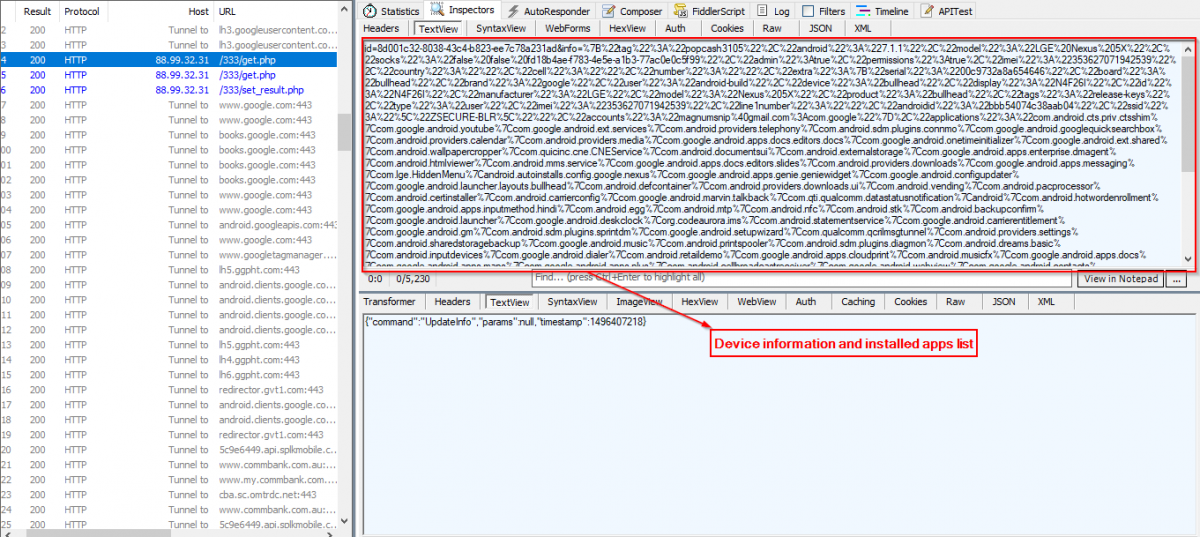
Fig 3: C&C communication
After a few sleep cycles, the malware waits for the user to open an app from its targeted list. We found that this variant is capable of targeting over 40 financial apps. When the user opens any of the targeted apps, the malware will quickly overlay a fake login page, which lures the victim into supplying user credentials. Some of the overlay pages are shown below.
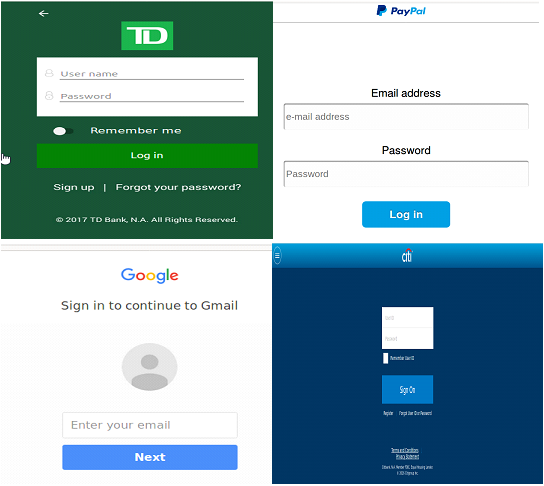
Fig 4: Fake login pages
Unlike Marcher malware we’ve seen in the past, this variant maintains a JavaScript Object Notation (JSON) file that lists each targeted app and its fake login page hosting URL. This list is hardcoded in the malware payload. A screen capture is shown below.
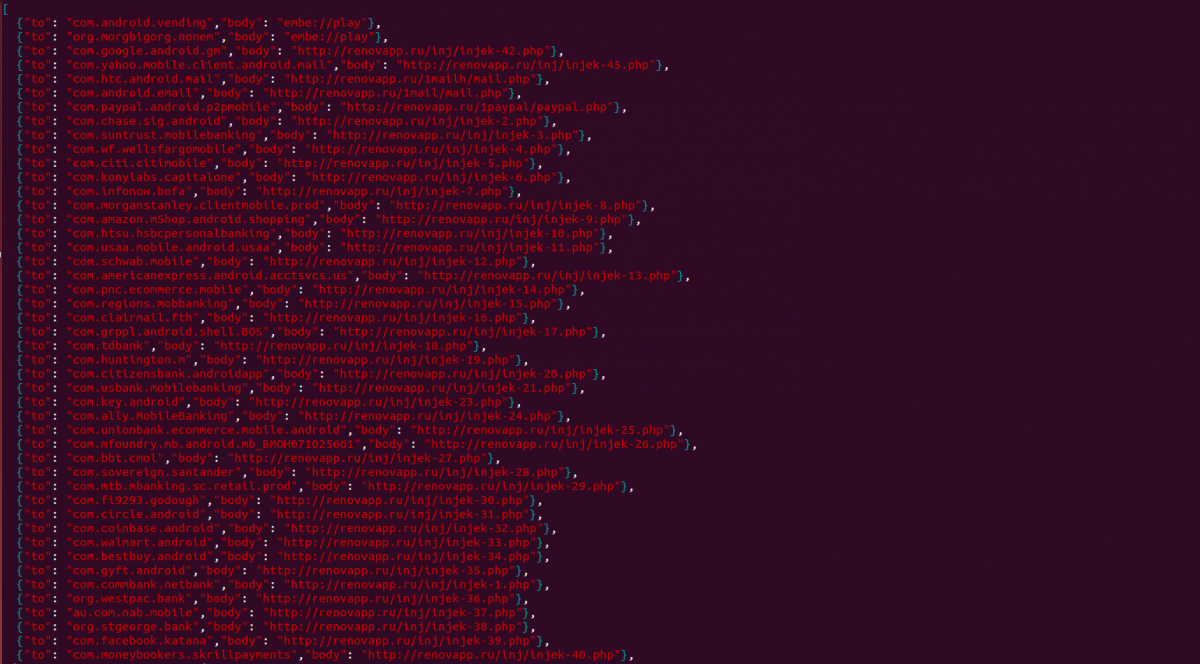
Fig 5: Targeted apps list with the associated URLs that serve the overlay pages
The following is a list of financial apps targeted by the new Marcher variant:
- com.android.vending
- org.morgbigorg.nonem
- com.google.android.gm
- com.yahoo.mobile.client.android.mail
- com.htc.android.mail
- com.android.email
- com.paypal.android.p2pmobile
- com.chase.sig.android
- com.suntrust.mobilebanking
- com.wf.wellsfargomobile
- com.citi.citimobile
- com.konylabs.capitalone
- com.infonow.bofa
- com.morganstanley.clientmobile.prod
- com.amazon.mShop.android.shopping
- com.htsu.hsbcpersonalbanking
- com.usaa.mobile.android.usaa
- com.schwab.mobile
- com.americanexpress.android.acctsvcs.us
- com.pnc.ecommerce.mobile
- com.regions.mobbanking
- com.clairmail.fth
- com.grppl.android.shell.BOS
- com.tdbank
- com.huntington.m
- com.citizensbank.androidapp
- com.usbank.mobilebanking
- com.key.android
- com.ally.MobileBanking
- com.unionbank.ecommerce.mobile.android
- com.mfoundry.mb.android.mb_BMOH071025661
- com.bbt.cmol
- com.sovereign.santander
- com.mtb.mbanking.sc.retail.prod
- com.fi9293.godough
- com.circle.android
- com.coinbase.android
- com.walmart.android
- com.bestbuy.android
- com.gyft.android
- com.commbank.netbank
- org.westpac.bank
- au.com.nab.mobile
- org.stgeorge.bank
- com.facebook.katana
- com.moneybookers.skrillpayments
- com.westernunion.android.mtapp
- au.com.ingdirect.android
- au.com.bankwest.mobile
- org.banksa.bank
- com.ebay.mobile
- com.ebay.gumtree.au
- com.anz.android.gomoney
- com.anz.android
Unlike other Marcher malware, this variant is highly obfuscated, which explains the low antivirus (AV) detection rate. The VirusTotal screen capture below shows that less than 20 percent of AV scanners detected the new variant (at the time of the scan).
VT: 11/59 (at the time of analysis)
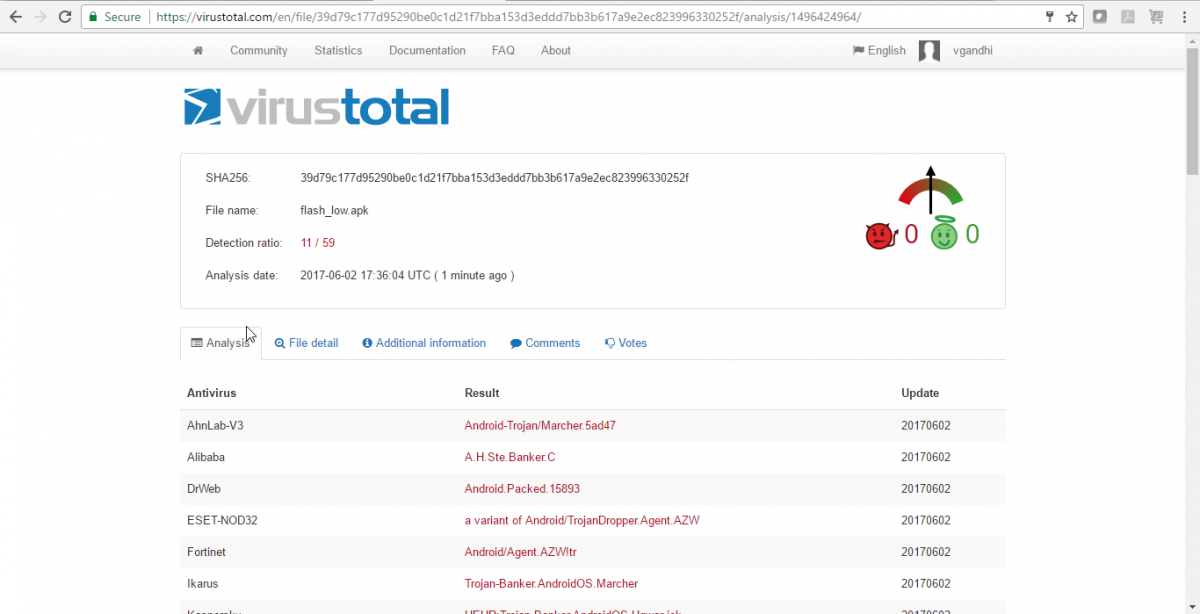
Fig 6: VT detection
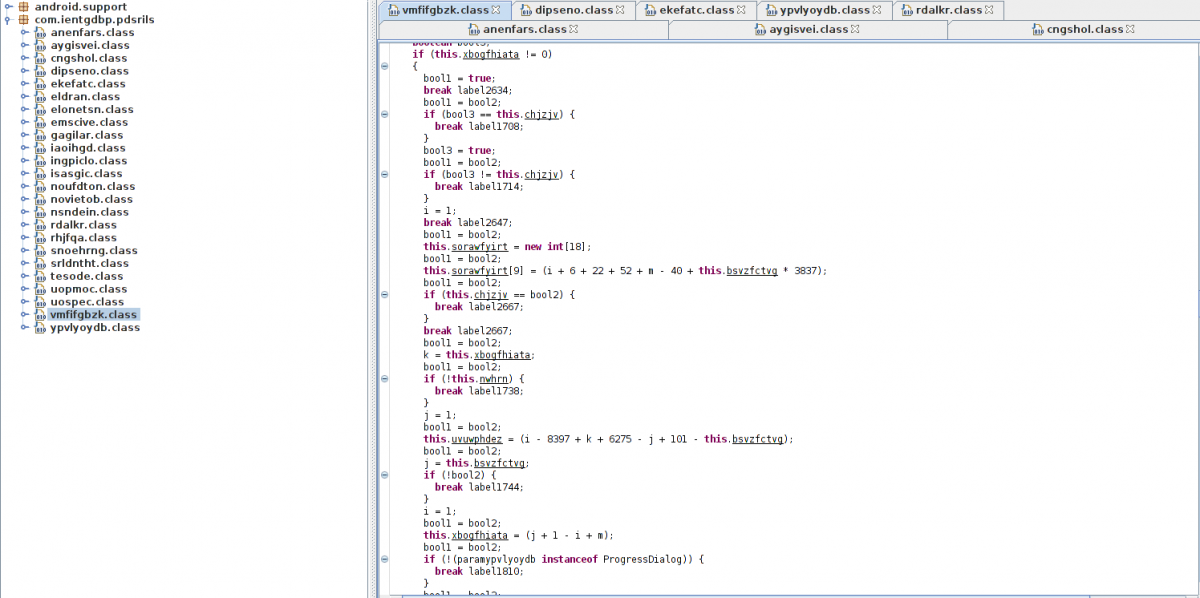
Fig 7: Obfuscated code
The overlay (fake) login pages for the financial apps are hosted remotely, allowing the author to update them as needed. In the sample C&C communication shown below, the user on the infected device tries to launch the Commonwealth Bank of Australia app; it gets intercepted by the Marcher Trojan, which loads an overlay login page from a remote location.
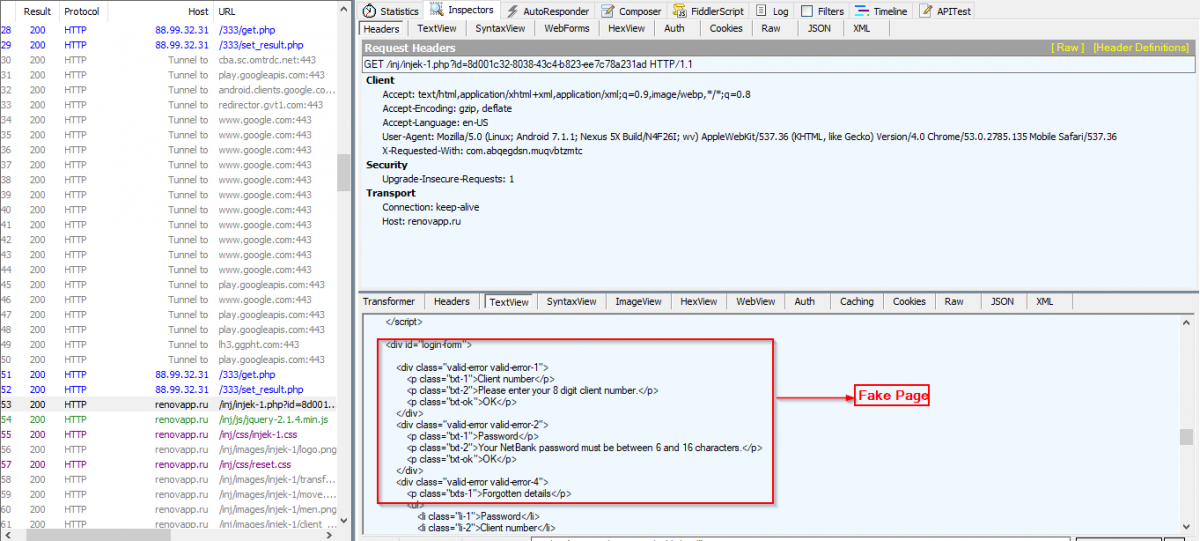
Fig 8: Serving fake page in server response
If the user falls for the fake login page and enters his or her banking credentials, the Marcher Trojan relays the information to the C&C server, as shown in the screenshot below.
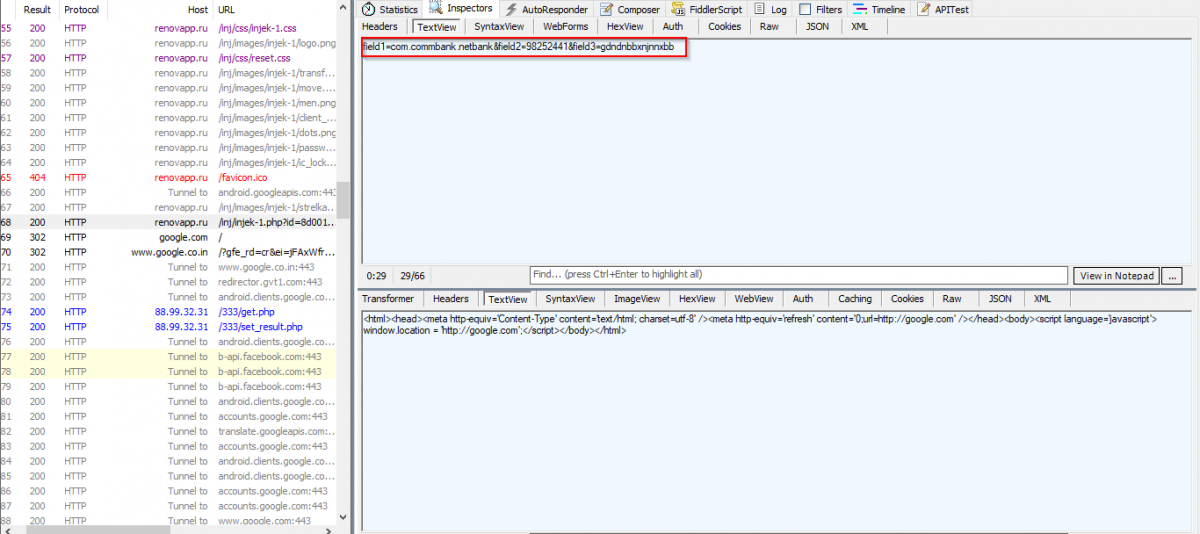
Fig 9: Credential harvesting
Conclusion
We have been seeing regular infection attempts for this Marcher variant in the past month. The frequent changes in the Marcher family indicate that the malware remains an active and prevalent threat to Android devices.
To avoid being a victim of such malware, be sure to download apps only from trusted app stores, such as Google Play. By unchecking the "Unknown Sources" option under the "Security" settings of your device, you can prevent inadvertent downloads from questionable sources.
Zscaler ThreatLabZ is actively monitoring Android Marcher and its variants to ensure that Zscaler customers are protected.
Indicators of compromise (IOCs):
Dropper URLs
- hxxp://click-soft[.]ga/flash/
- hxxp://rockstargamers[.]ru/flash
- hxxp://optus-mms[.]net/flash
- hxxp://luxapps[.]ru/flash
- hxxp://apdate[.]tk/flash/
C&Cs:
- hxxp://88[.]99[.]32[.]31
- hxxp://adminhasdp2123[.]ru





