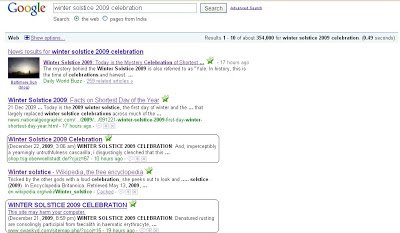
Yesterday, December 21st 2009 was the Winter Solstice, meaning that it was the shortest day of the year. Malware authors did not miss this opportunity to push their malicious binaries using SEO (search-engine optimization) attacks. My colleague already posted a blog on SEO attacks where he mentioned that an SEO attack takes the advantage of Google's PageRank Technology to push search results to the top. We found several phrases/names like “Winter Solstice 2009 celebration” or “Shortest day of the year 2009” used in the search query resulted in a page redirecting to malicious sites containing malware. Here is the screenshot of search result,
Looking at the screenshot, you will find that the 3rd and 5th search results are malicious. Attackers use SEO as users are more likely to click on links which show up as top results. Clicking on the 3rd link uses redirection to direct victim to a malicious site hosting malware. Here is what a user will see,
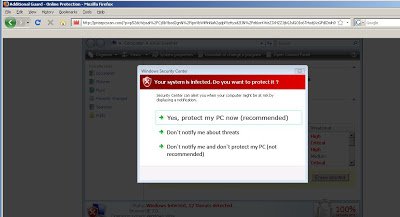
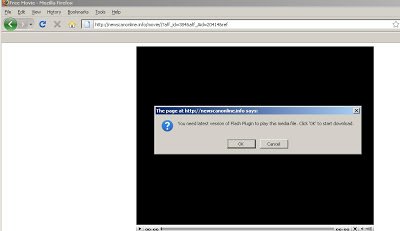
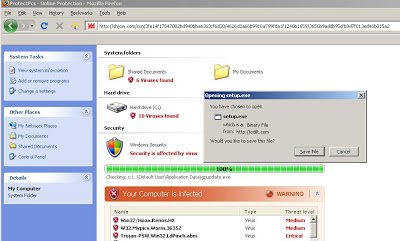
Redirection could take the victim to a variety of sites, all of which are hosting fake security applications. The malicious sites are using fake images, popups or even showing videos to social engineer the victim into downloading a malicious executable once they click on the page. Here are some few sites used for downloading the malware:
“hxxp://ftorm.com/scn/579876515334ef7a1587…[truncated]”
“hxxp://shjow.com/scn/3fe14f17847082bd940b…[truncated]”
“hxxp://prizepcscan.com/?p=p52dcWpsal%2FCj…[truncated]”
“hxxp://newscanonline.info/downloads.php/?aff_id=384…[truncated]”
Here are screenshots of the malicious sites:
The above images are taken after clicking on the same search results multiple times, resulting in redirection to different attack sites and methods used for infection. Sometimes the victim will be presented with a video playing or popup images or messages urging the victim to install fake anti-virus software. The sites displaying videos will download a file named “Flash_Plugin_Setup1261476530.exe” to the system and other sites download “setup.exe” as a malicious file. Here are the virus total results for those files,
For “Flash_Plugin_Setup1261476530.exe”
For “setup.exe”
The “setup.exe” has very poor detection (4 out of 41). This is not the first time malware authors have used the latest hot news, celebrity’s names, holidays, popular event etc. They use such key phrases to push their malicious site to the top of the search results using SEO techniques. They continually change their malicious binaries in order to evade Anti-viruses from detection. The success of this approach is demonstrated in the above Virustotal results illustrating poor AV detection. Be sure to never download anything from redirected site promising free security software.
Be Safe,
Umesh