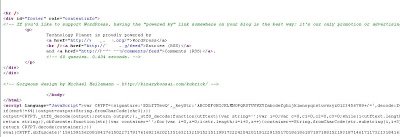
As we have seen, many websites are infected with malicious IFRAMES. The IFRAMES are either injected as plain text or they are heavily obfuscated using JavaScript. Obfuscation is intentionally used by attackers to bypass AV or IPS engines. Attackers are not only using simple obfuscation techniques to encode malicious IFRAMES, they are also using publicly available Base64 encoding/decoding routines to encode their content. Recently, we found one website which was infected with a malicious IFRAME leveraging such a technique. Here is the screenshot of the webpage:
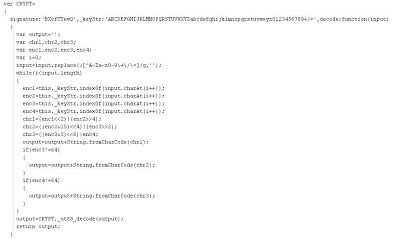
This is the initial part of the JavaScript, which is being used to encrypt the script using signature and key strings. The key string is a long string containing upper and lower case characters, numbers and special characters. Let’s look at the remainder of the script:
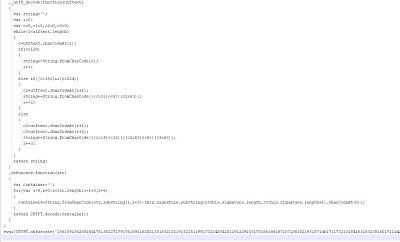
Here, we see a function called _utf8_decode() being used to decode the script and there is also a call to an eval() function. If we decode it using a tool called Malzilla, you will see the following hidden malicious IFRAME:
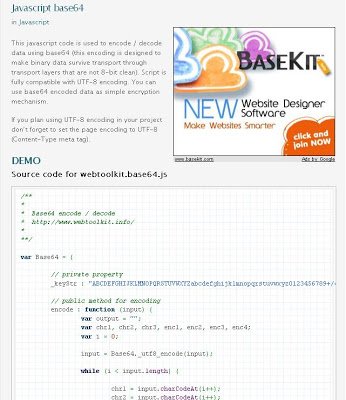
Interestingly, the code used for this encoding technique is publicly available on the Internet. In fact, this Base64 encoding/decoding routine is a part of the webtoolkit. The name of the JavaScript file in question is “webtoolkit.base64.js”. Here is the screenshot of webpage:
In this case, the attacker has used the same code to encode the malicious script with a few minor changes such as adding an eval() function to the script. This shows just how easy for an attacker to create obfuscated JavaScript using publicly available code. Though, the webtoolkit JavaScript is being written for a legitimate purpose, attackers are taking advantage of the freely available code. Detection of this technique remains poor among antivirus vendors. Only 17 vendors out of 41 are detecting this malicious script. The Virustotal results also show that’s many large vendors such as Symantec, Microsoft, Mcafee, etc. are still missing protection for this malicious script. The IFRAME attacks are not new but we are now seeing attackers taking advantages of additional techniques to obfuscate their attacks. Has your source code used in such attacks?
That’s it for now.
Umesh