Karanataka Vikas Grameena Bank is victim of an attack. The site is comprised by the injection of malicious obfuscated JavaScript.
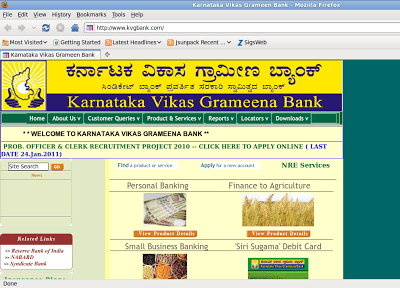
Home page of kvgbank.com :
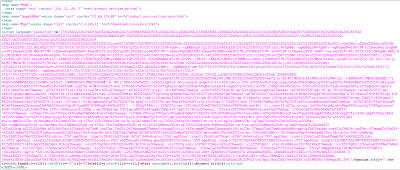
Obfuscated JavaScript :
Multilevel obfuscated JavaScript was used to infect the site. Ultimately, it required two levels of De-obfuscation to fully decode it.
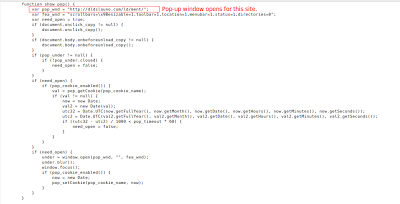
Part of De-obfuscated JavaScript:
The purpose of such attacks is to redirect the victims browser to pull content from a malicious site. Attackers have learned that it is far more effective to simply infect already popular websites, rather than set up a separate malicious site and social engineer victims into visiting it. In this particular instance, the De-obfuscated code opens a pop-up box depending on user's browser version. The link used now points to a parked domain but likely previously hosted malicious code.
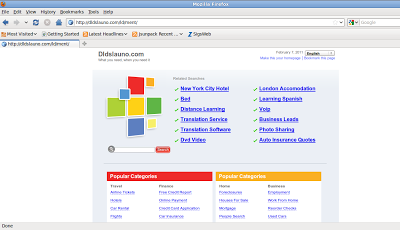
Home Page of http://dldslauno.com/ld/ment/ :
Even though the malicious code is not delivered by above site, it is possible that the vulnerability that led to the attack has not yet been patched and further infection could occur, or in future the linked site may host malicious content. We have informed the bank about the infection.
Virustotal results shows 23 out of 43 AV's vendors trigger on the kvg bank site.
Pradeep.