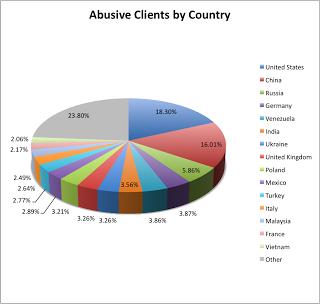
Last week, we announced our IPAbuseCheck lookup tool. We see lots of infected/abusive hosts on the Internet attempting to proxy abusive web transactions through our proxies. Rather than just ignoring these transactions, we’ve decided to provide this lookup utility for security professionals and organizations to query and identify abusive/infected hosts within their networks – based on some feedback, the service has been well received. This follow-up post provides a brief summary of the top offenders that we see in our database to date (July 1 – October 25, 2011).
| ASN by Abusive Clients | ASN by Abusive Transactions | ||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
|
It was interesting to see some well known organizations like Amazon and Microsoft near the top for organizations that have sent us the most abusive transactions. Rather than these being infected corporate systems, it appears to be a handful of hosting service systems that are being abused either directly from the customer or from an infection. Here is a snapshot of a report from our database of a Microsoft IP that we reported to their Abuse Dept. once we started digging into this data:
OriginAS: AS8075
NetName: MICROSOFT-DYNAMIC-HOSTING
Top 5 Abusive Hosts by Date Range
| Host | First Seen | Last Seen | Behavior |
|---|---|---|---|
| 193.17.253.7 | 07/01/11 07:00 | 10/25/11 06:54 | Proxy Scanning |
| 207.226.163.146 | 07/01/11 07:00 | 10/25/11 06:51 | Proxy Scanning |
| 174.34.168.114 | 07/01/11 07:06 | 10/25/11 06:57 | Proxy Scanning |
| 221.187.4.28 | 07/01/11 07:07 | 10/25/11 06:56 | Proxy Scanning |
| 69.164.211.212 | 07/01/11 07:08 | 10/25/11 06:54 | Proxy Scanning |
The following table lists the top 5 abusive hosts by transaction count - these tend to be hosts that attempt to forward bulk transactions through proxies, like forum spam and brute-force attempts. Related to the previous section of organizations with the top abusive transactions - you can see that two Amazon EC2 systems (75.101.225.168, 248) are at the top of the list.
Top 5 Abusive Hosts by Transactions
| Host | Transaction % | Behavior |
|---|---|---|
| 75.101.225.168 | 19.94% | Forum Spam |
| 111.221.81.70 | 6.31% | Forum Spam |
| 75.101.225.248 | 5.17% | Forum Spam |
| 117.41.235.133 | 3.06% | Brute-Forcing |
| 84.16.224.62 | 2.13% | Brute-Forcing |
| Abusive Transactions:
| Abusive Clients:
|
The bulk of the top sites by transaction are forum spam sites - in the top instances, the forums being abused are in Vietnam. One brute-forcing target is in the top 5, which is the Rapidshare file host. The bulk of the top services being used/abused by number of clients are proxy checkers - the Chinese service sina.com.cn was also listed in the top as a spam bot / brute-forcing target.