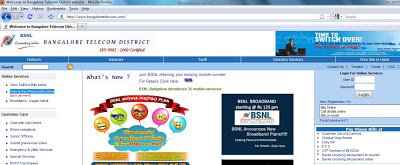
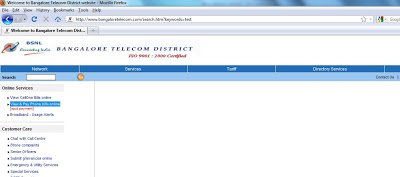
Interestingly, the home page does not contain malicious content, but rather the malicious JavaScript has been injected into one of the “.js” files used for searching the content of the website. If you look at the above screenshot, you will see small search box. The attack will be activated if you search on anything using this functionality. Below is a screenshot of the search page a user is redirected to:
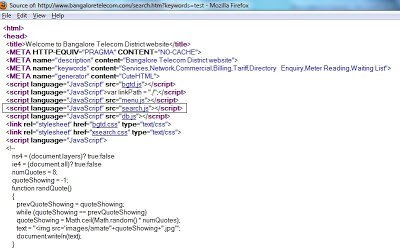
The source code of this page contains various “.js” files. The “search.js” file is infected with malicious JavaScript code. Here is the source code of that file:
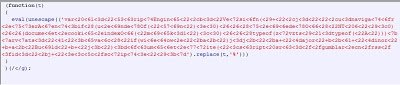
The malicious JavaScript code is inserted at the bottom of this “.js” file. Here is the malicious content:
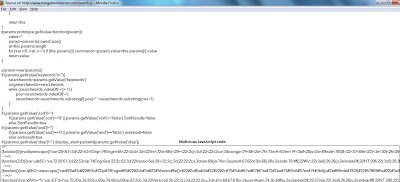
There are six different malicious JavaScript snippets, each obfuscated in a different way, but all ultimately point to same malicious domain. Let’s investigate one of them:
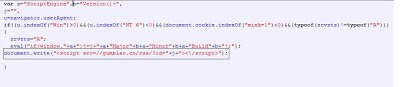
The decoded script is shown below:
The above malicious code points to the malicious domain “gumblar.cn”, which was used by the Gumblar Trojan. Fortunately, the malicious domain has now been taken down.
Zscaler blocks the infected page rather than blocking whole website. This example illustrates how malicious content can be filtered out, while still allowing access to what is an otherwise legitimate site – an important approach, given the prevalence of malicious infections. Our recent posts highlight the fact that numerous popular Indian web sites are struggling with proper application security controls.
Umesh