Attackers usually use some form of social engineering technique to fool users into downloading and executing a malicious executable - they scare users with a fake antivirus page, they present users with a video that requires a new software or codec update, they claim the user's browser or Flash version is out of date, etc.
Last week, I found several Google search results for popular terms leading directly to a virus download. The following 6 domains were hijacked by attackers:
- pancrase.org
- legacyhealthgroup.com
- movingmidway.com
- playnormous.com
- tombraiderinc.com
- dogbreedsbook.com
When users click on one of these domains in a Google search result page, they are redirected to another domain. This new page ensures that the request has been received from a live user with a web browser. This is accomplished by looking at the user agent and at the Referer value (does the user come from Google?). If the test is successful, the user is then redirected to vicrtorytrip.net or gfaster.net.
These 2 domains serve an executable with the name www.com. It is detected as malicious by only 5 AV vendors out of 42.
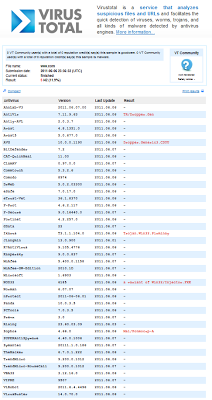 |
| Virustotal result page |
All the redirections are done through HTTP 302 redirections, so no new page is shown to the user. As a result, users may think the file download was done from Google, because it does not appear that they left the Google search result page. This is the "trick" the attackers rely on to ensure that users trust the executable file, in addition to the name www.com which looks like a domain name rather than a file name.
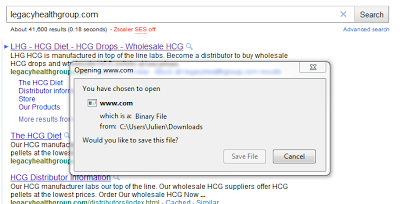 |
| Malicious file download attempt |
Once again, the best protection, and often the only one, is to educate users to not download and install any file unless they fully trust its origin, and explicitly requested the download.
-- Julien





