Introduction
Android Marcher Trojan was first seen in 2013 scamming users for credit card information by prompting fake Google Play store payment page. In subsequent years, Marcher variants also started targeting banking applications by presenting fake login pages to steal user credentials.
Marcher has continued to stay active and was recently covered by
phishlabs. In this blog, we will cover a new wave of Marcher Trojan that is active since past one month where the malware arrives as an adobe flash installer package. We have captured over 50 unique payloads from this campaign. Majority of these Marcher payloads are from pornographic sites serving fake adobe flash player for watching porn. The primary goal of this malware is still the same - display a fake Google Play store payment page and steal financial information from the user.
Technical analysis
The infection cycle starts with the mobile user receiving a malicious URL via e-mail or SMS. Once the user opens this URL, the site will prompt the user to download and install the Adobe Flash Player update as seen below:
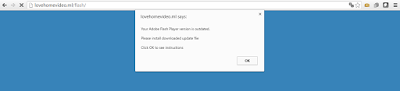 |
| Fake Adobe Flash Player outdated warning |
The file that gets downloaded as a result of this action is aptly named - AdobeFlashPlayer.apk. Upon installation, malware asks for administrative access in order to perform its functions as seen below:
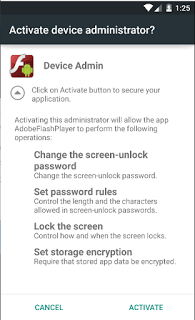 |
| Requests administrative access |
Once installed, Marcher connects to a predetermined Command & Control (C&C) server and sends information about all the installed applications on the infected device as seen here:
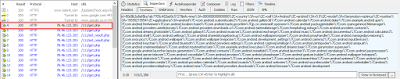 |
| Relaying installed package information to C&C |
During our analysis, we also observed a unique approach where the C&C server will send a response generating a MMS notification on the infected device saying "You have received MMS" and instructs the user to visit "mms-service[.]info/mms" to see the content of the MMS.
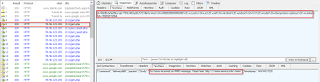 |
| MMS content |
This site redirects the user to the
X-VIDEO app on official Google Play store. According to several reviews of this app, the users are claiming it to be a fake app that simply crashes after installation. We were able to verify the same crash behavior when installed on the latest Android OS Marshmallow 6.0.1. We haven't analyzed this app in any further detail but have been in touch with Google's Android team to review these findings. The app in question has been downloaded more than 100,000 times and some of these downloads may have happened from infected devices. (UPDATE: This app has been verified as clean by Google's Android team but they are monitoring it further.)
 |
| Official Play store app- X-VIDEO |
As part of the infection cycle, Marcher will then display a fake Google Play payment screen asking for payment information to complete the account setup.
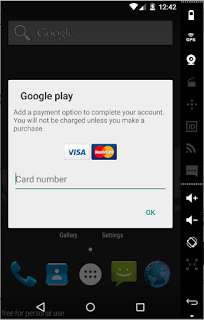 |
| Fake Google Play payment screen. |
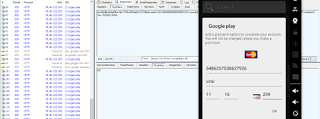 |
| Credit card information. |
If the user falls for this screen then the credit card information is logged and relayed to the C&C server as seen below:
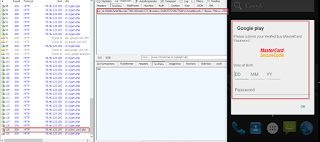 |
| Payment information sent to C&C server. |
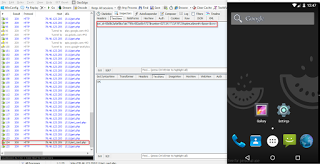 |
| Information being sent to C&C server |
|
Newer variants of the Android marcher will also present a fake online banking login page based on information collected about already installed banking apps on victims device. Here is a sample fake login page that the user will see if the infected device has Commonwealth Bank of Australia mobile app installed.
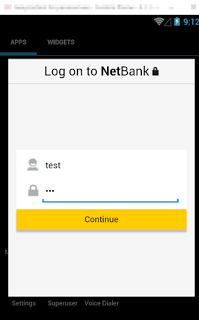 |
| Fake NetBank login screen |
The user banking credential information is relayed back to the C&C server in plain text as seen below:
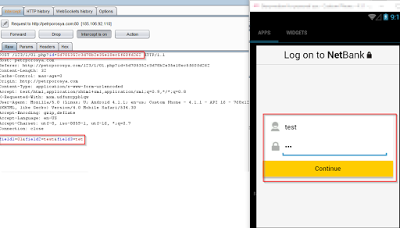 |
| Stolen information sent in plain text |
Following are some of the financial institution mobile apps that are targeted by Marcher:
- BankSA - Bank of South Australia
- Commerzbank
- Commonwealth Bank of Australia - NetBank app
- Deutsche Postbank
- DKB - Deutsche Kreditbank
- DZ Bank
- Deutsche Bank
- Fiducia & GAD IT
- ING Direct
- La Banque Postale
- Mendons
- NAB - National Australia Bank
- PayPal
- Santander Bank
- Westpac
- WellStar billpay app
Conclusion
Android Marcher has been around since year 2013 and continues to actively target mobile user's financial information. To avoid being a victim of such malware, it is always best to download apps only from trusted app stores, such as Google Play. This can be enforced by unchecking the "Unknown Sources" option under the "Security" settings of your device.
Zscaler ThreatLabZ is actively monitoring this malware and ensuring that Zscaler customers are protected.
IOCs
C&C URLs
- hxxp://78[.]46[.]123[.]205/111/get[.]php
- hxxp://78[.]46[.]123[.]205/111/set_card[.]php
- hxxp[:]//petrporosya[.]com/123/1/01[.]php?id=[UNIQID]
Sample URLs serving the Android Marcher payloads
- hxxp://lovehomevideo[.]cf/adobeflashplayer[.]apk
- hxxp://videolike[.]ga/adobeflashplayer[.]apk
- hxxp://lovehomevideo[.]ml/adobeflashplayer[.]apk
- hxxp://analsextube[.]ml/adobeflashplayer[.]apk
- hxxp://myporno[.]cf/adobeflashplayer[.]apk
- hxxp://mymovie-porn[.]ga/adobeflashplayer[.]apk
- hxxp://lovehomevideo[.]ga/adobeflashplayer[.]apk
- hxxp://adobe-flash-player[.]su/flashplayer[.]apk
















