Zero trust and CARTA. These are two of the biggest topics being talked about in the security world. If you were at RSA earlier this year you were probably hard-pressed to find a booth without zero trust plastered all over it. CARTA, the Gartner Continuous Adaptive Risk and Trust Assessment (CARTA) strategy, and the newest Gartner technology approach, zero trust network access (ZTNA), are quickly gaining traction within enterprise IT teams—especially those that subscribe to Gartner’s security perspective.
But why now? What’s causing this massive buzz?
The attention can mainly be attributed to digital transformation (yes, I totally just completed the trifecta of buzzwords). Specifically, enterprises and government agencies are recognizing the benefits of cloud and mobility for more speed, stronger competitive differentiation, and greater cost savings for the business. This transformation from a network-based operating environment to one that’s cloud-based is pushing legacy security models to the brink. For the first time in 30 years, security is being forced to evolve. Enterprises are in need of a new approach—one that replaces data center and perimeter-centric security with a user- and app-centric model.
Consider these three factors, identified by Gartner in its CARTA report:
- There will be more users outside of the enterprise accessing services than inside
- Customers will have more unmanaged devices connecting to services than managed devices
- Internal users will consume more apps delivered from outside of the enterprise network than from the inside
Each one of these factors highlights pitfalls with legacy security technologies. VPNs place users on the network, giving them the keys to your castle and allowing any malware on those users’ devices to be introduced to the network where it can spread laterally. In fact, this is often the source of ransomware attacks like NotPetya and iEncrypt.
DMZs were designed to help the good guys gain access to enterprise services over the internet, but they also give the bad guys access to those services! And that leaves your crown jewels exposed potential internet-based attacks.
The inherent trust implied when VPNs and DMZs are used is often abused by the bad guys. Instead, minimizing trust to the point where access is delivered just in time and on a least-privilege basis should be the goal.
Contrary to popular belief, the security perimeter is not going away—that would be an oversimplification. Instead, the perimeter has been extended and now exists everywhere. It’s with mobile users accessing private apps on personal devices from home, the hotel, airport, or Starbucks. The private apps now running in the public cloud.
THIS is the new perimeter.
With it, zero trust network access and the CARTA framework become incredibly important. Now, companies should look to understand how they work together.
Zero trust today builds atop the initial zero trust model that Forrester’s John Kindervag developed 10 years ago. The name is a bit misleading as trust must inevitably be established in order for work to get done, but the main idea was to adopt a default-deny posture, and trust no one.
The reality is that zero trust in itself is important, but it is only the starting point in a greater journey. A one-time gate at the initiation of a session is not a framework in itself. This is where Gartner’s Continuous Adaptive Risk & Trust Assessment (CARTA) comes in.
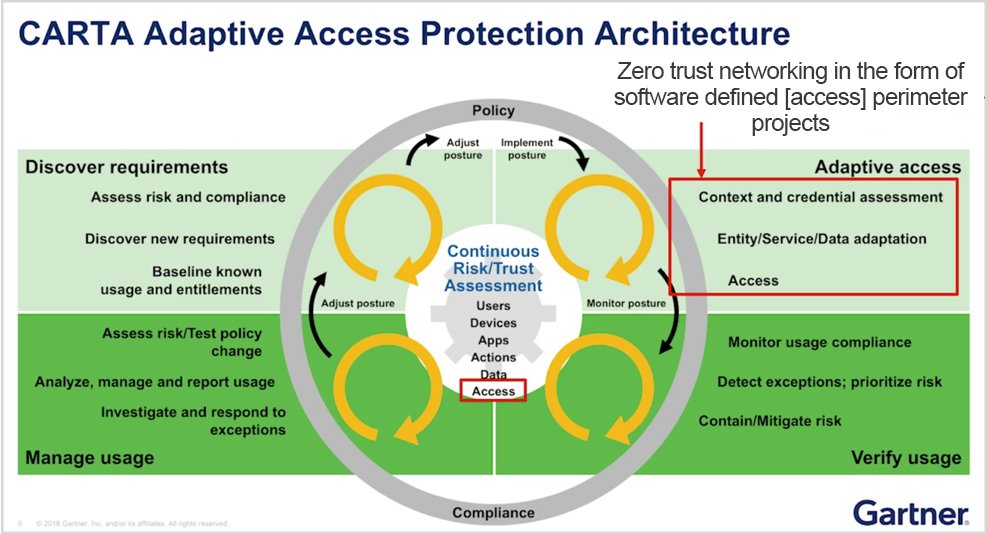
Source: Gartner (December 2018)
CARTA is the next iteration of the Gartner Adaptive Security Architecture from 2014. Here, zero trust becomes a starting point and one of the key pillars of CARTA, as explained below:
- Security should always begin with zero trust
- Access should be based on context, for example, the identity of the user, the device being used, etc.
- Monitoring should be on an ongoing basis to assess risk; access is adaptive and varies based on context
Security is not just at the point of initiation. It is a dynamic entity that must be flexible enough to extend to a perimeter that has evolved. This is why Gartner recommends software-defined perimeter (SDP) solutions, due to their ability to perform app segmentation, as the first zero trust project enterprises take on.
While enterprises should look to embrace CARTA, they must consider the challenges they may face when trying to get there. I’ll highlight a few below:
- Attempting to use traditional technologies – Firewall appliances and virtual appliances are built to secure the network. With the adoption of public cloud services, you no longer control the network, which is the internet, so how do you do network security? Traditional technologies place employees (and partners) on the corporate network, expose apps to the internet, and they’re expensive to scale and manage. What happens with 5G?! SDP solutions were built to address all these challenges—keeping users off the network and keeping apps invisible to the internet—and they’re infinitely scalable—which makes SDP a requirement for today’s IT.
- Planning for no-agent and no-MDM on devices – Being able to deliver user-centric security when there is no agent on the device is difficult. Users working on any number of devices must have the flexibility to connect over a browser, instead, and go agentless. This is especially important when partners need to access private apps.
- Performing risk assessment on an ongoing basis – Security can no longer be a one-and-done mindset. Teams should adopt technologies that adapt to the user and the changing context in which they access business services. Adopting modern, cloud-first technologies that integrate well together across user, device, logging, and connectivity is a must.
Read Gartner's Market Guide to zero trust network access. Feel free to reach out to me if you have any questions about the model, SDP, or how Zscaler can help: [email protected].
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Chris Hines is head of product marketing for Zscaler Private Access and Z App.






