CVE-2010-0806, a use-after-free vulnerability in the Peer Objects component, was announced in mid-March 2010. The vulnerability impacts Internet Explorer 6, 6 SP1, and 7 - a patch was made available by Microsoft in the MS10-018 security update last week. Zscaler received early notification of the vulnerability through our trusted partnership with Microsoft and was able to deploy signatures to detect and block exploit attempts soon after the public release of the vulnerability.
Today this site was detected and blocked for attempting to exploit CVE-2010-0806:
hxxp://cn.cnsa56.info/w/woz.htm
--> and supporting script: hxxp://cn.cnsa56.info/w/k.js
The JavaScript used to exploit the vulnerability is heavily obfuscated,
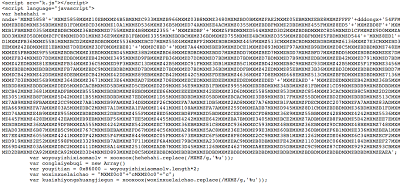 And the script contains some try-catch statements to evade detection and some automated analysis tools,
And the script contains some try-catch statements to evade detection and some automated analysis tools,
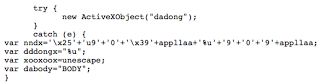 and
and
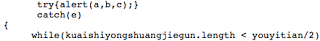 The above try{} statements will fail, so the code within catch{} will be run, which defines some variables and logic for decoding the above shellcode.
The above try{} statements will fail, so the code within catch{} will be run, which defines some variables and logic for decoding the above shellcode.
Wepawet fails to decode/analyze properly, and categorizes the URL as benign. VirusTotal has 2/39 Anti-Virus engines that detect as a suspicious JavaScript downloader through their heuristic engines.
After decoding and analyzing the shellcode, it downloads the payload:
hxxp://v.vkjk6.info/w/win.exe
Unfortunately, VirusTotal shows no detection for this file. When conducting basic analysis on the binary payload, it becomes obvious that this is not a valid PE executable. It is likely that the binary is encrypted or obfuscated and that the shellcode run from the CVE-2010-0806 exploit will decode the binary on the victim's machine. (I will run the exploit in a sandbox, and post any follow-on analysis of the payload).
Often times, the domain information for malicious domains is masked through a domain privacy service (like Domains by Proxy)- however, this was not the case for the domains involved in this attack.
Here is the billing information for the cnsa56.info domain:
 This same registration information was used for another live domain: ac364.info
This same registration information was used for another live domain: ac364.info
And for vkjk6.info:
 126.com is a free email provider,
126.com is a free email provider,